Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.7 Security algorithm selection, key establishment and security mode command procedure
6.7.1 Procedures for NAS algorithm selection
6.7.1.1 Initial NAS security context establishment
6.7.1.2 AMF change
6.7.2 NAS security mode command procedure
6.7.3 Procedures for AS algorithm selection
6.7.3.0 Initial AS security context establishment
6.7.3.1 Xn-handover
6.7.3.2 N2-handover
6.7.3.3 Intra-gNB-CU handover/intra-ng-eNB handover
6.7.3.4 Transitions from RRC_INACTIVE to RRC_CONNECTED states
6.7.3.5 RNA Update procedure
6.7.3.6 Algorithm negotiation for unauthenticated UEs in LSM
6.7.4 AS security mode command procedure
...
...
6.7 Security algorithm selection, key establishment and security mode command procedure p. 77
6.7.1 Procedures for NAS algorithm selection p. 77
6.7.1.1 Initial NAS security context establishment p. 77
Each AMF shall be configured via network management with lists of algorithms which are allowed for usage. There shall be one list for NAS integrity algorithms, and one for NAS ciphering algorithms. These lists shall be ordered according to a priority decided by the operator.
To establish the NAS security context, the AMF shall choose one NAS ciphering algorithm and one NAS integrity protection algorithm. The AMF shall then initiate a NAS security mode command procedure, and include the chosen algorithm and UE security capabilities (to detect modification of the UE security capabilities by an attacker) in the message to the UE (see subclause 6.7.2 of the present document). The AMF shall select the NAS algorithm which have the highest priority according to the ordered lists.
6.7.1.2 AMF change p. 77
If the change of the AMF at N2-Handover or mobility registration update results in the change of algorithm to be used for establishing NAS security, the target AMF shall indicate the selected algorithm to the UE as defined in Clause 6.9.2.3.3 for N2-Handover (i.e., using NAS Container) and Clause 6.9.3 for mobility registration update (i.e., using NAS SMC). The AMF shall select the NAS algorithm which has the highest priority according to the ordered lists (see subclause 6.7.1.1 of the present document).
6.7.2 NAS security mode command procedure p. 77
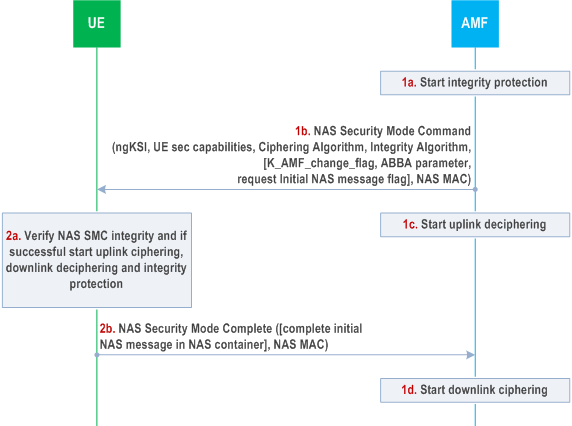
The NAS SMC shown in Figure 6.7.2-1 shall be used to establish NAS Security context between the UE and the AMF. This procedure consists of a roundtrip of messages between the AMF and the UE. The AMF sends the NAS Security Mode Command message to the UE and the UE replies with the NAS Security Mode Complete message.
Step 1a.
The AMF activates the NAS integrity protection before sending the NAS Security Mode Command message.
Step 1b.
The AMF sends the NAS Security Mode Command message to the UE. The NAS Security Mode Command message shall contain: the replayed UE security capabilities, the selected NAS algorithms, and the ngKSI for identifying the KAMF. The NAS Security Mode Command message may contain: K_AMF_change_flag (carried in the additional 5G security parameters IE specified in TS 24.501) to indicate a new KAMF is calculated, a flag requesting the complete initial NAS message (see subclause 6.4.6), Anti-Bidding down Between Architectures (ABBA) parameter. In the case of horizontal derivation of KAMF during mobility registration update or during multiple registration in same PLMN, K_AMF_change_flag shall be included in the NAS Security Mode Command message as described in clause 6.9.3.
This message shall be integrity protected (but not ciphered) with NAS integrity key based on the KAMF indicated by the ngKSI in the NAS Security Mode Command message (see Figure 6.7.2-1).
In case the network supports interworking using the N26 interface between MME and AMF, the AMF shall also include the selected EPS NAS algorithms (defined in Annex B of TS 33.401) to be used after mobility to EPS in the NAS Security Mode Command message (see clause 8.5.2). The UE shall store the algorithms for use after mobility to EPS using the N26 interface between MME and AMF. The AMF shall store the selected EPS NAS algorithms in the UE security context.
Step 1c.
The AMF activates NAS uplink deciphering after sending the NAS Security Mode Command message.
Step 2a.
The UE shall verify the NAS Security Mode Command message. This includes checking that the UE security capabilities sent by the AMF match the ones stored in the UE to ensure that these were not modified by an attacker and verifying the integrity protection using the indicated NAS integrity algorithm and the NAS integrity key based on the KAMF indicated by the ngKSI.
In case the NAS Security Mode Command message includes a K_AMF_change_flag, the UE shall derive a new KAMF as described in Annex A.13 and set the NAS COUNTs to zero.
If the verification of the integrity of the NAS Security Mode Command message is successful, the UE shall start NAS integrity protection and ciphering/deciphering with the security context indicated by the ngKSI.
Step 2b.
The UE sends the NAS Security Mode Complete message to the AMF ciphered and integrity protected. The NAS Security Mode Complete message shall include PEI in case AMF requested it in the NAS Security Mode Command message. The AMF shall set the NAS COUNTs to zero if horizontal derivation of KAMF is performed. The UE may include the complete initial NAS message (see subclause 6.4.6 for details).
If the verification of the NAS Security Mode Command message is not successful in the UE, it shall reply with a NAS Security Mode Reject message (see TS 24.501). The NAS Security Mode Reject message and all subsequent NAS messages shall be protected with the previous, if any, 5G NAS security context, i.e., the 5G NAS security context used prior to the failed NAS Security Mode Command message. If no 5G NAS security context existed prior to the NAS Security Mode Command message, the NAS Security Mode Reject message shall remain unprotected.
The AMF shall de-cipher and check the integrity protection on the NAS Security Mode Complete message using the key and algorithm indicated in the NAS Security Mode Command message. NAS downlink ciphering at the AMF with this security context shall start after receiving the NAS Security Mode Complete message.
Step 1d.
The AMF activates NAS downlink ciphering.
6.7.3 Procedures for AS algorithm selection p. 79
6.7.3.0 Initial AS security context establishment p. 79
This clause provides the details for AS security algorithms negotiation and consideration during the UE initial AS security context establishment.
Each gNB/ng-eNB shall be configured via network management with lists of algorithms which are allowed for usage. There shall be one list for integrity algorithms, and one for ciphering algorithms. These lists shall be ordered according to a priority decided by the operator. When AS security context is to be established in the gNB/ng-eNB, the AMF shall send the UE 5G security capabilities to the gNB/ng-eNB. The gNB/ng-eNB shall choose the ciphering algorithm which has the highest priority from its configured list and is also present in the UE 5G security capabilities.
The gNB/ng-eNB shall choose the integrity algorithm which has the highest priority from its configured list and is also present in the UE 5G security capabilities. The chosen algorithms shall be indicated to the UE in the AS SMC. The chosen ciphering algorithm is used for ciphering (when activated) of the user plane and RRC traffic. The chosen integrity algorithm is used for integrity protection (when activated) of the user plane and RRC traffic. Activation of ciphering and integrity protection for the RRC traffic shall be done as defined by clause 6.7.4. Activation of ciphering and integrity protection for the user plane traffic shall be done based on the UP security policy received from the SMF as defined by clause 6.6.2.
6.7.3.1 Xn-handover p. 79
At handover from a source gNB/ng-eNB over Xn to a target gNB/ng-eNB, the source gNB/ng-eNB shall include the UE's 5G security capabilities and ciphering and integrity algorithms used in the source cell in the handover request message. The target gNB/ng-eNB shall select the algorithm with highest priority from the received 5G security capabilities of the UE according to the prioritized locally configured list of algorithms (this applies for both integrity and ciphering algorithms). The chosen algorithms shall be indicated to the UE in the Handover Command message if the target gNB/ng-eNB selects different algorithms compared to the source gNB/ng-eNB. If the UE does not receive any selection of integrity and ciphering algorithms, it continues to use the same algorithms as before the handover (see TS 38.331 for gNB or TS 36.331 for ng-eNB). When a Xn-handover takes place from ng-eNB to gNB or vice versa, then the selected algorithms in the target node shall always be signalled in the Handover Command to the UE. In the Path-Switch message, the target gNB/ng-eNB shall send the UE's 5G security capabilities received from the source gNB/ng-eNB to the AMF. The AMF shall verify that the UE's 5G security capabilities received from the target gNB/ng-eNB are the same as the UE's 5G security capabilities that the AMF has locally stored. If there is a mismatch, the AMF shall send its locally stored 5G security capabilities of the UE to the target gNB/ng-eNB in the Path-Switch Acknowledge message. The AMF shall support logging capabilities for this event and may take additional measures, such as raising an alarm.
If the target gNB/ng-eNB receives UE's 5G security capabilities from the AMF in the Path-Switch Acknowledge message, the target gNB/ng-eNB shall update the AS security context of the UE with these 5G security capabilities of the UE. The target gNB/ng-eNB shall select the algorithm with highest priority from these 5G security capabilities according to the locally configured prioritized list of algorithms (this applies for both integrity and ciphering algorithms). If the algorithms selected by the target gNB/ng-eNB are different from the algorithms used at the source gNB/ng-eNB, then the target gNB/ng-eNB shall initiate intra-cell handover procedure which includes RRC Connection Reconfiguration procedure indicating the selected algorithms and an NCC to the UE.
6.7.3.2 N2-handover p. 79
At handover from a source gNB/ng-eNB to a target gNB/ng-eNB over N2 (possibly including an AMF change and hence a transfer of the UE's 5G security capabilities from the source AMF to the target AMF), the target AMF shall send the UE's 5G security capabilities to the target gNB/ng-eNB in the NGAP HANDOVER REQUEST message (see TS 38.413). The target gNB/ng-eNB shall select the algorithm with highest priority from the UE's 5G security capabilities according to the locally configured prioritized list of algorithms (this applies for both integrity and ciphering algorithms). The chosen algorithms shall be indicated to the UE in the Handover Command message if the target gNB/ng-eNB selects different algorithms compared to the source gNB/ng-eNB. If the UE does not receive any selection of integrity and ciphering algorithms, it continues to use the same algorithms as before the handover (see TS 38.331).
For N2-handover, the source gNB/ng-eNB shall include AS algorithms used in the source cell (ciphering and integrity algorithms) in the source to target transparent container that shall be sent to the target gNB/ng-eNB. The AS algorithms used by the source cell are provided to the target gNB/ng-eNB so that it can use them during the potential RRC Connection Re-establishment procedure use them as specified in clause 6.11 for gNB and TS 33.401 for ng-eNB.
6.7.3.3 Intra-gNB-CU handover/intra-ng-eNB handover p. 80
It is not required to change the AS security algorithms during intra-gNB-CU/intra-ng-eNB handover. If the UE does not receive an indication of new AS security algorithms during an intra-gNB-CU/intra-ng-eNB handover, the UE shall continue to use the same algorithms as before the handover (see TS 38.331 for gNB and TS 36.331 for ng-eNB).
6.7.3.4 Transitions from RRC_INACTIVE to RRC_CONNECTED states p. 80
At state transition from RRC_INACTIVE to RRC_CONNECTED, the source gNB/ng-eNB shall include the UE 5G security capabilities and the ciphering and integrity algorithms the UE was using with the source cell in the Xn-AP Retrieve UE Context Response message.
The target gNB/ng-eNB shall check if it supports the received algorithms, if the target gNB/ng-eNB supports the received ciphering and integrity algorithms, the target gNB/ng-eNB shall check the received algorithms to its locally configured list of algorithms (this applies for both integrity and ciphering algorithms). If the target gNB/ng-eNB selects the same security algorithms, the target gNB/ng-eNB shall use the selected algorithms to derive RRC integrity and RRC encryption keys to protect the RRCResume message and send to the UE on SRB1.
If the target gNB/ng-eNB does not support the received algorithms or if the target gNB/ng-eNB prefers to use different algorithms, the target gNB/ng-eNB shall send an RRCSetup message on SRB0 in order to proceed with RRC connection establishment as if the UE was in RRC_IDLE (fallback procedure) to the UE. Then the UE performs NAS based RRC recovery and negotiates a suitable algorithm with target gNB/ng-eNB via AS SMC procedure.
6.7.3.5 RNA Update procedure p. 80
If the source gNB/ng-eNB decides to relocate UE context to the target gNB/ng-eNB during an RNA Update procedure, the source gNB/ng-eNB shall include the UE 5G security capabilities and the ciphering and integrity algorithms the UE was using with the source cell in the <Xn-AP Retrieve UE Context Response> message. AS security algorithm selection is as described in clause 6.7.3.4.
6.7.3.6 Algorithm negotiation for unauthenticated UEs in LSM p. 80
UEs that are in limited service mode (LSM) and that cannot be authenticated by the AMF/SEAF (for whatever reason) may still be allowed to establish emergency session by sending the emergency registration request message. It shall be possible to configure whether the AMF allows unauthenticated UEs in LSM to establish bearers for emergency session or not. If an AMF allows unauthenticated UEs in LSM to establish bearers for an emergency session, then for the NAS protocol, the AMF shall use NIA0 and NEA0 as the integrity and ciphering algorithm respectively.
If the AMF allows an unauthenticated UE in LSM to establish bearers for emergency session after it has received the emergency registration request message from the UE, the AMF shall:
- Select NIA0 and NEA0, regardless of the supported algorithms announced previously by the UE as the NAS algorithms and signal this to the UE via the NAS security mode command procedure when activating the 5G NAS security context.
-
Set the UE 5G security capabilities to only contain EIA0, EEA0, NIA0 and NEA0 when sending these to the gNB/ng-eNB in the following messages:
- NGAP UE INITIAL CONTEXT SETUP
- NGAP UE CONTEXT MODIFICATION REQUEST
- NGAP HANDOVER REQUEST
6.7.4 AS security mode command procedure p. 81
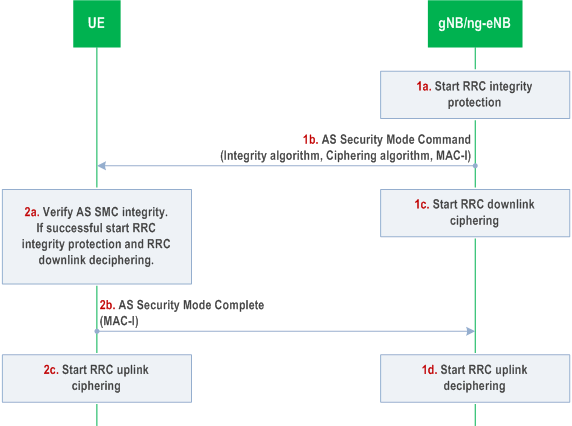
The AS SMC procedure is for RRC and UP security algorithms negotiation and RRC security activation. for the gNB/ng-eNB. AS SMC procedure can be triggered to establish a secure RRC signalling-only connection during UE registration or PDU session establishment as specified in TS 38.413 and TS 23.502. The activation of UP security is as described in clause 6.6.2. AS SMC procedure consists of a roundtrip of messages between gNB/ng-eNB and UE. The gNB/ng-eNB sends the AS security mode command to the UE and the UE replies with the AS security mode complete message. See Figure 6.7.4-1.
The AS security mode command message sent from gNB/ng-eNB to UE shall contain the selected RRC and UP encryption and integrity algorithms. This AS security mode command message shall be integrity protected with RRC integrity key based on the current KgNB.
The AS security mode complete message from UE to gNB/ng-eNB shall be integrity protected with the selected RRC algorithm indicated in the AS security mode command message and RRC integrity key based on the current KgNB.
RRC downlink ciphering (encryption) at the gNB/ng-eNB shall start after sending the AS security mode command message. RRC uplink deciphering (decryption) at the gNB/ng-eNB shall start after receiving and successful verification of the AS security mode complete message.
RRC uplink ciphering (encryption) at the UE shall start after sending the AS security mode complete message. RRC downlink deciphering (decryption) at the UE shall start after receiving and successful verification of the AS security mode command message.
If any control of the AS security mode command is not successful in the UE, the UE shall reply with an unprotected security mode failure message (see TS 38.331).
Ciphering and integrity protection of UP downlink and uplink, at the UE and the gNB/ng-eNB, shall start as defined by clause 6.6.2.
AS SMC shall be used only during an initial context setup between the UE and the gNB/ng-eNB (i.e., to activate an initial KgNB at RRC_IDLE to RRC_CONNECTED state transition).