Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
4 Overview of security architecture
4.1 Security domains
4.2 Security at the perimeter of the 5G Core network
4.2.0 General
4.2.1 Security Edge Protection Proxy (SEPP)
4.2.2 Inter-PLMN UP Security (IPUPS)
4.3 Security entities in the 5G Core network
...
...
4 Overview of security architecture p. 28
4.1 Security domains p. 28
Figure 4-1 gives an overview of security architecture.
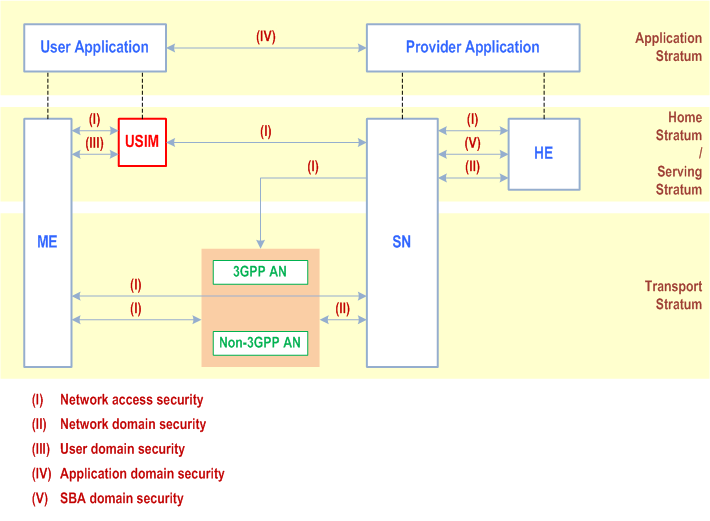
The Figure illustrates the following security domains:
- Network access security (I): the set of security features that enable a UE to authenticate and access services via the network securely, including the 3GPP access and Non-3GPP access, and in particularly, to protect against attacks on the (radio) interfaces. In addition, it includes the security context delivery from SN to AN for the access security.
- Network domain security (II): the set of security features that enable network nodes to securely exchange signalling data and user plane data.
- User domain security (III): the set of security features that secure the user access to mobile equipment.
- Application domain security (IV): the set of security features that enable applications in the user domain and in the provider domain to exchange messages securely. Application domain security is out of scope of the present document.
- SBA domain security (V): the set of security features that enables network functions of the SBA architecture to securely communicate within the serving network domain and with other network domains . Such features include network function registration, discovery, and authorization security aspects, as well as the protection for the service-based interfaces. SBA domain security is a new security feature compared to TS 33.401.
- Visibility and configurability of security (VI): the set of features that enable the user to be informed whether a security feature is in operation or not.
4.2 Security at the perimeter of the 5G Core network p. 29
4.2.0 General |R16| p. 29
The security specified in this document applies to both roaming and PLMN interconnect.
4.2.1 Security Edge Protection Proxy (SEPP) |R16| p. 29
The 5G System architecture introduces a Security Edge Protection Proxy (SEPP) as an entity sitting at the perimeter of the PLMN for protecting control plane messages.
The SEPP enforces inter-PLMN security on the N32 interface.
4.2.2 Inter-PLMN UP Security (IPUPS) |R16| p. 29
The 5G System architecture introduces Inter-PLMN UP Security (IPUPS) at the perimeter of the PLMN for protecting user plane messages.
The IPUPS is a functionality of the UPF that enforces GTP-U security on the N9 interface between UPFs of the visited and home PLMNs.
4.3 Security entities in the 5G Core network p. 29
The 5G System architecture introduces the following security entities in the 5G Core network:
AUSF:
AUthentication Server Function;
ARPF:
Authentication credential Repository and Processing Function;
SIDF:
Subscription Identifier De-concealing Function;
SEAF:
SEcurity Anchor Function.