Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.1.4 Linking increased home control to subsequent procedures
6.1.4.1 Introduction
6.1.4.1a Linking authentication confirmation to Nudm_UECM_Registration procedure from AMF
6.1.4.2 Guidance on linking authentication confirmation to Nudm_UECM_Registration procedure from AMF
6.1.5 Home network triggered primary authentication procedure
6.1.5.1 General
6.1.5.2 Security mechanisms
...
...
6.1.4 Linking increased home control to subsequent procedures p. 54
6.1.4.1 Introduction p. 54
The 5G authentication and key agreement protocols provide increased home control. Compared to EPS AKA in EPS, this provides better security useful in preventing certain types of fraud as explained in more detail below.
This increased home control comes in the following forms in 5GS:
UECM_Registration Request for registering the subscriber's serving AMF in UDM that are not actually present in the visited network. But an authentication protocol by itself cannot provide protection against such fraud. The authentication result needs to be linked to subsequent procedures, e.g. the Nudm_UECM_Registration procedure from the AMF in some way to achieve the desired protection.
The actions taken by the home network to link authentication confirmation (or the lack thereof) to subsequent procedures are subject to operator policy and are not standardized.
But informative guidance is given in subclause 6.1.4.2 as to what measures an operator could usefully take. Such guidance may help avoiding a proliferation of different solutions.
The feature of increased home control is also used to allow the UDM to keep track of the AUSF that stores the KAUSF to be used during e.g. the control plane solution for Steering of Roaming or UE Parameter Update procedures; i.e. the AUSF that stores the latest KAUSF generated after successful completion of the latest primary authentication reported to the UDM.
After the UDM is informed that the UE has been successfully (re-)authenticated, the UDM shall store the AUSF instance which reported the successful authentication. If the UDM has been previously informed that the UE was authenticated by a different AUSF instance, the UDM may request the old AUSF to clear the stale security parameters (KAUSF, SOR counter and UE parameter update counter). If the UDM determines to delete the security parameters in the old AUSF, then the UDM shall use the Nausf_UEAuthentication_deregister service operation (see clause 14.1.5).
- In the case of EAP-AKA', the AUSF in the home network obtains confirmation that the UE has been successfully authenticated when the EAP-Response/AKA'-Challenge received by the AUSF has been successfully verified, cf. subclause 6.1.3.1 of the present document.
-
In the case of 5G AKA, the AUSF in the home network obtains confirmation that the UE has been successfully authenticated when the authentication confirmation received by the AUSF in Nausf_
UEAuthentication_ Request message has been successfully verified, cf. subclause 6.1.3.2 of the present document.Authenticate
6.1.4.1a Linking authentication confirmation to Nudm_UECM_Registration procedure from AMF p. 55
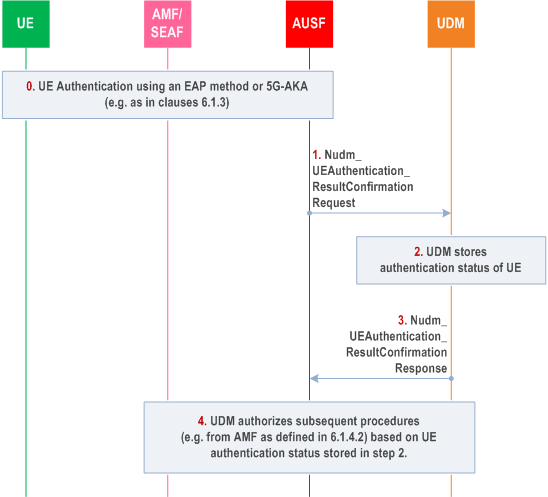
The information sent from the AUSF to the UDM that a successful or unsuccessful authentication of a subscriber has occurred, shall be used to link authentication confirmation to subsequent procedures. The AUSF shall send the Nudm_UEAuthentication_ResultConfirmation service operation for this purpose as shown in Figure 6.1.4.1a-1.
Step 1.
The AUSF shall inform UDM about the result and time of an authentication procedure with a UE using a Nudm_UEAuthentication_ResultConfirmation Request. This shall include the SUPI, a timestamp of the authentication, the authentication type (e.g. EAP method or 5G-AKA), and the serving network name.
Step 2.
The UDM shall store the authentication status of the UE (SUPI, authentication result, timestamp, and the serving network name).
Step 3.
UDM shall reply to AUSF with a Nudm_UEAuthentication_ResultConfirmation Response.
Step 4.
Upon reception of subsequent UE related procedures (e.g. Nudm_UECM_Registration_Request from AMF) UDM may apply actions according to home operator's policy to detect and achieve protection against certain types of fraud (e.g. as proposed in clause 6.1.4.2).
6.1.4.2 Guidance on linking authentication confirmation to Nudm_UECM_Registration procedure from AMF p. 55
This subclause gives informative guidance on how a home operator could link authentication confirmation (or the lack thereof) to subsequent Nudm_UECM_Registration procedures from AMF to achieve protection against certain types of fraud, as mentioned in the preceding subclause.
Approach 1:
The home network records the time of the most recent successfully verified authentication confirmation of the subscriber together with the identity of the 5G visited network that was involved in the authentication. When a new Nudm_UECM_Registration Request arrives from a visited network, the home network checks whether there is a sufficiently recent authentication of the subscriber by this visited network. If not, the Nudm_UECM_Registration Request is rejected. The rejection message may include, according to the home networks policy, an indication that the visited network should send a new Nausf_UEAuthentication_Authenticate Request (cf. subclause 6.1.2 of the present document) for fetching a new authentication vector before repeating the Nudm_UECM_Registration Request.
Approach 2:
As a variant of the above Approach 1, Approach 2 is based on a more fine-grained policy applied by the home network; the home network could classify roaming partners into different categories, depending on the trust - e.g. derived from previous experience placed in them, for example as follows:
-
For a visited network in the first category, the home network would require a successful authentication 'immediately preceding' the Nudm_
UECM_ Request from an AMF.Registration - For a visited network in the second category, the home network would only check that an authentication in a network visited by the subscriber was sufficiently recent (taking into account that there may have been a security context transfer between the visited networks).
-
For a visited network in the third category, the home network would perform no checks regarding Nudm_
UECM_ Requests and authentication at all.Registration
6.1.5 Home network triggered primary authentication procedure |R18| p. 56
6.1.5.1 General p. 56
The support of Home Network triggered authentication is optional for the HN and the SN. If both the networks (HN and SN) support Home Network triggered primary authentication, the following clauses apply.
6.1.5.2 Security mechanisms p. 56
The UDM may initiate primary authentication based on procedures initiated by the UE (e.g. UE registration in 5GC) or towards the UE (e.g. SoR/UPU) or events from other NFs, considering the local policy into account as well.
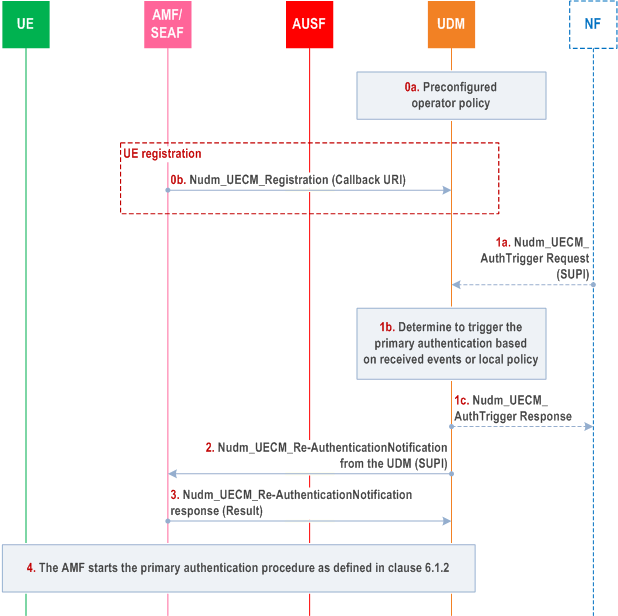
Step 0a and step 0b are the pre-requisites of the whole procedure.
Step 0a.
The UDM may execute other procedures (e.g. SoR/UPU) depending on the reason that motivated the UDM triggered (re-)authentication procedure in step 1.
The UDM may be pre-configured with an operator authentication policy in order to determine when to trigger a primary authentication procedure.
Step 0b.
The UE registers to the network. As part of the registration, the serving AMF registers the UE with the UDM via the Nudm_UECM_Registration as per clause 4.2.2.2.2 of TS 23.502. The AMF shall provide a callback URI within the AMF registration for the UDM to create an implicit subscription to later notify the AMF for potential home network triggered re-authentication using the Nudm_UECM_Re-AuthenticationNotification service operation as in step 2.
Step 1a-c.
The UDM decides itself based on events (e.g., SoR/UPU or NF requests such as AAnF requests as defined in TS 33.535) or authentication policy and performs home network triggered primary authentication as described in the following steps. The NF such as the AAnF considers based on operator's local authentication policy described in TS 33.535 to send Nudm_UECM_AuthTrigger request to the UDM for primary authentication using the UDM services as described in clause 14.2.6. The NF may send a Nudm_UECM_AuthTrigger Request message to the UDM with the SUPI of the target UE. The UDM may acknowledge the request with an Nudm_UECM_AuthTrigger Response to the NF.
If there are different AMFs registered in the UDM for different access, the UDM shall select one AMF to perform the re-authentication. The criteria for selecting the AMF are dependent of the local UDM authentication policy.
Step 2.
The UDM sends a Nudm_UECM_Re-AuthenticationNotification message to the AMF/SEAF with the UE's SUPI.
Step 3.
After receiving the Nudm_UECM_Re-AuthenticationNotification message from the UDM, the AMF/SEAF shall decide whether to run the primary authentication procedure based on its own local authentication policy, and the UE state (e.g. , if the UE is under handover, or if the UE is already under authentication by the AMF before receiving the authentication notification from the UDM). If the AMF/SEAF determines that it cannot run a primary authentication as described in step 4 (e.g., due to local policy), the AMF/SEAF sends the authentication response message to the UDM with a failure cause else it acknowledges the request. If the AMF/SEAF acknowledged the request but the AMF/SEAF is not able to initiate the primary authentication towards the UE (e.g. if UE is not reachable), the AMF/SEAF shall set the authentication pending flag. Upon receiving a failure from the AMF, the UDM may check if another AMF is available over the other access. If available, the UDM may select another AMF and retry Step 2.
When UE re-attaches to the same AMF or becomes reachable, the AMF checks the authentication pending flag and performs the reauthentication if needed. Once UE reauthentication is done, the AMF resets the authentication pending flag.
Step 4.
The AMF/SEAF starts the primary authentication procedure as defined in clause 6.1.2 of the present document.