Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.4 NAS security mechanisms
6.4.1 General
6.4.2 Security for multiple NAS connections
6.4.2.1 Multiple active NAS connections with different PLMNs
6.4.2.2 Multiple active NAS connections in the same PLMN's serving network
6.4.3 NAS integrity mechanisms
6.4.3.0 General
6.4.3.1 NAS input parameters to integrity algorithm
6.4.3.2 NAS integrity activation
6.4.3.3 NAS integrity failure handling
6.4.4 NAS confidentiality mechanisms
6.4.4.0 General
6.4.4.1 NAS input parameters to confidentiality algorithm
6.4.4.2 NAS confidentiality activation
6.4.5 Handling of NAS COUNTs
6.4.6 Protection of initial NAS message
6.4.7 Security aspects of SMS over NAS
...
...
6.4 NAS security mechanisms p. 68
6.4.1 General p. 68
This subclause describes the security mechanisms for the protection of NAS signalling and data between the UE and the AMF over the N1 reference point. This protection involves both integrity and confidentiality protection. The security parameters for NAS protection are part of the 5G security context described in subclause 6.3 of the present document.
6.4.2 Security for multiple NAS connections p. 68
6.4.2.1 Multiple active NAS connections with different PLMNs p. 68
TS 23.501 has a scenario when the UE is registered to a VPLMN's serving network via 3GPP access and to another VPLMN's or HPLMN's serving network via non-3GPP access at the same time. When the UE is registered in one PLMN's serving network over a certain type of access (e.g. 3GPP) and is registered to another PLMN's serving network over another type of access (e.g. non-3GPP), then the UE has two active NAS connections with different AMF's in different PLMNs. As described in clause 6.3.2.1, the UE shall independently maintain and use two different 5G security contexts, one per PLMN serving network. The 5G security context maintained by the UE shall contain the full set of 5G parameters, including NAS context parameters for 3GPP and non-3GPP access types per PLMN. In case of connection to two different PLMNs, it is necessary to maintain a complete 5G NAS security context for each PLMN independently, each with all associated parameters (such as two pairs of NAS COUNTs, i.e. one pair for 3GPP access and one pair for non-3GPP access).
Each security context shall be established separately via a successful primary authentication procedure with the Home PLMN.
All the NAS and AS security mechanisms defined for single registration mode are applicable independently on each access using the corresponding 5G security context.
6.4.2.2 Multiple active NAS connections in the same PLMN's serving network p. 68
When the UE is registered in a serving network over two types of access (e.g. 3GPP and non-3GPP), then the UE has two active NAS connections with the same AMF. A common 5G NAS security context is created during the registration procedure over the first access type.
In order to realize cryptographic separation and replay protection, the common NAS security-context shall have parameters specific to each NAS connection. The connection specific parameters include a pair of NAS COUNTs for uplink and downlink and unique NAS connection identifier. The value of the unique NAS connection identifier shall be set to "0x01" for 3GPP access and set to "0x02" for non-3GPP access. All other parameters as e.g. algorithm identifiers in the common NAS security context are common to multiple NAS connections.
In non-mobility cases, when the UE is simultaneously registered over both types of accesses, and if NAS key re-keying as described in clause 6.9.4.2 or if NAS key refresh as described in clause 6.9.4.3 takes place over one of the accesses (say access A):
- If the other access (access B) is in CM-CONNECTED state, then the new NAS security context shall only be activated over that access (access A). The UE and the AMF shall not change the NAS security context in use on the other access (say access B). In order to activate the new NAS security context over the other access (access B), the AMF shall trigger a NAS SMC run over that access either in the current running procedure or a subsequent NAS procedure. During the second NAS SMC run (on access B), the AMF shall include the same ngKSI associated with the new NAS security context and the same algorithm choices as for the first access. After a successful second NAS SMC procedure over the other access (access B), both the UE and the AMF shall delete the old NAS security context.
- Whenever the AMF sends a NAS SMC over access (access A) and AMF considers the UE to not be in CM-CONNECTED state on the other access (access B), the AMF shall additionally activate (if not already in use on the other access) the security context that is active on the other accesses. Similarly, whenever the UE receives a NAS SMC over the access (access A) and UE is not in CM-CONNECTED state on the other access (access B), the UE additionally activates (if not already in use on the other access) the security context on the other access.
-
If the UE is in CM-CONNECTED state on the non-3GPP access, then:
- if the AMF does not have the security context the UE is using on the non-3GPP access (e.g. KAMF change on 3GPP access when the AMF changes), then in order to activate the same NAS security context that is in use over the 3GPP access the AMF shall run a NAS SMC procedure on the non-3GPP access; or
- in the case of handover from EPS, then a mapped context will be in use on the 3GPP access and a different security context will be active on the non-3GPP access. To align the security contexts in use over both accesses, the AMF shall run a NAS SMC procedure over one access to take into use on that access the security context that is in use on the other access. In the case that a native security context is in use on the non-3GPP access, then the NAS SMC procedure shall be on the 3GPP access to take the native security context into use.
- Whenever the AMF sends a Registration Accept over the 3GPP access and AMF considers the UE to not be in CM-CONNECTED state on the non-3GPP access, the AMF shall activate (if not already in use on the non-3GPP access) the security context that is in use on the 3GPP access on the non-3GPP access. The AMF shall keep a native security context that was in use on non-3GPP access if the security context in use on the 3GPP access is a mapped security context. In order to take this native security context into use, the AMF shall run a NAS SMC procedure. Similarly, whenever the UE receives a Registration Accept over the 3GPP access and UE is not in CM-CONNECTED state on the non-3GPP access, the UE activates (if not already in use on the non-3GPP access) the security context that is in use on the 3GPP access on the non-3GPP access. The UE shall keep a native security context that was in use on non-3GPP access if the security context in use on the 3GPP access is a mapped security context.
6.4.3 NAS integrity mechanisms p. 69
6.4.3.0 General p. 69
Integrity protection for NAS signalling messages shall be provided as part of the NAS protocol.
6.4.3.1 NAS input parameters to integrity algorithm p. 69
The input parameters to the NAS 128-bit integrity algorithms as described in Annex D shall be set as follows.
The KEY input shall be equal to the KNASint key.
The BEARER input shall be equal to the NAS connection identifier.
The DIRECTION bit shall be set to 0 for uplink and 1 for downlink.
The COUNT input shall be constructed as follows:
The use and mode of operation of the 128-bit integrity algorithms are specified in Annex D.
COUNT := 0x00 || NAS COUNT
Where NAS COUNT is the 24-bit NAS UL COUNT or the 24-bit NAS DL COUNT value, depending on the direction, that is associated to the current NAS connection identified by the value used to form the BEARER input.
A NAS COUNT shall be constructed as follows:
NAS COUNT := NAS OVERFLOW || NAS SQN
Where
- NAS OVERFLOW is a 16-bit value which is incremented each time the NAS SQN is incremented from the maximum value.
- NAS SQN is the 8-bit sequence number carried within each NAS message.
6.4.3.2 NAS integrity activation p. 70
NAS integrity shall be activated using the NAS SMC procedure or after an inter-system handover from EPC.
Replay protection shall be activated when integrity protection is activated, except when the NULL integrity protection algorithm is selected. Replay protection shall ensure that the receiver only accepts each incoming NAS COUNT value once using the same NAS security context.
Once NAS integrity has been activated, NAS messages without integrity protection shall not be accepted by the UE or the AMF. Before NAS integrity has been activated, NAS messages without integrity protection shall only be accepted by the UE or the AMF in certain cases where it is not possible to apply integrity protection.
NAS integrity shall stay activated until the 5G security context is deleted in either the UE or the AMF. It shall not be possible to change from non-NULL integrity protection algorithm to NULL integrity protection.
6.4.3.3 NAS integrity failure handling p. 70
The supervision of failed NAS integrity checks shall be performed both in the ME and the AMF. In case of failed integrity check (i.e. faulty or missing NAS-MAC) is detected after the start of NAS integrity protection, the concerned message shall be discarded except for some NAS messages specified in TS 24.501. For those exceptions the AMF shall take the actions specified in TS 24.501 when receiving a NAS message with faulty or missing NAS-MAC. Discarding NAS messages can happen on the AMF side or on the ME side.
6.4.4 NAS confidentiality mechanisms p. 70
6.4.4.0 General p. 70
Confidentiality protection for NAS signalling messages shall be provided as part of the NAS protocol.
6.4.4.1 NAS input parameters to confidentiality algorithm p. 70
The input parameters for the NAS 128-bit ciphering algorithms shall be the same as the ones used for NAS integrity protection as described in clause 6.4.3, with the exception that a different key, KNASenc, is used as KEY, and there is an additional input parameter, namely the length of the key stream to be generated by the encryption algorithms.
The use and mode of operation of the 128-bit ciphering algorithms are specified in Annex D.
6.4.4.2 NAS confidentiality activation p. 70
NAS confidentiality shall be activated using the NAS SMC procedure or after an inter-system handover from EPC.
Once NAS confidentiality has been activated, NAS messages without confidentiality protection shall not be accepted by the UE or the AMF. Before NAS confidentiality has been activated, NAS messages without confidentiality protection shall only be accepted by the UE or the AMF in certain cases where it is not possible to apply confidentiality protection.
NAS confidentiality shall stay activated until the 5G security context is deleted in either the UE or the AMF.
6.4.5 Handling of NAS COUNTs p. 71
The NAS security context created at the registration time of the first access type contains the NAS integrity and encryption keys, selected algorithm common for all NAS connections. In addition, each NAS connection shall have a unique NAS connection identifier, a distinct pair of NAS COUNTs, one NAS COUNT for uplink and one NAS COUNT for downlink, associated with it. In the NAS security context, the NAS connection identifier shall be the differentiator for the connection-specific parameters.
It is essential that the NAS COUNTs for a particular KAMF are not reset to the start values (that is the NAS COUNTs only have their start value when a new KAMF is generated). This prevents the security issue of using the same NAS COUNTs with the same NAS keys, e.g. key stream re-use, in the case a UE moves back and forth between two AMFs and the same NAS keys are re-derived.
In the AMF, all the distinct pairs of NAS COUNTs part of the same 5G NAS security context, shall only be set to the start value in the following cases:
- for a partial native 5GC NAS security context created by a successful primary authentication run on one of the NAS connections established between the same AMF and the UE, or,
- for a mapped 5G security context generated when a UE moves from an MME to the AMF during both idle and connected mode mobility, or,
- for a new KAMF taken into use in a target AMF during mobility registration update or handover.
6.4.6 Protection of initial NAS message p. 71
The initial NAS message is the first NAS message that is sent after the UE transitions from the idle state. The UE shall send a limited set of IEs (called the cleartext IEs) including those needed to establish security in the initial message when it has no NAS security context. When the UE has a NAS security context, the UE shall send a message that has the complete initial NAS message ciphered in a NAS Container along with the cleartext IEs with whole message integrity protected. The complete initial message is included in the NAS Security Mode Complete message in a NAS Container when needed (e.g. AMF cannot find the used security context) in the latter case and always in the former case as described below.
In case, the UE selects a PLMN other than Registered PLMN/EPLMN in the 5GMM-IDLE state and the UE has a NAS security context containing the NEA0, then the UE shall discard the NAS security context and shall follow the procedure specified in this clause for protection of initial NAS message.
The protection of the initial NAS message proceeds as shown in Figure 6.4.6-1.
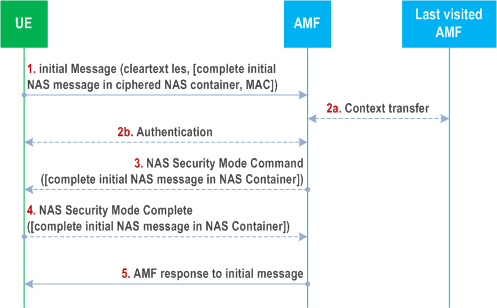
Step 1.
The UE shall send the initial NAS message to the AMF. If the UE has no NAS security context, the initial NAS message shall only contain the cleartext IEs, i.e. subscription identifiers (e.g. SUCI or GUTIs), UE security capabilities, ngKSI, indication that the UE is moving from EPC, Additional GUTI, and IE containing the TAU Request in the case idle mobility from LTE.
If the UE has a NAS security context, the message sent shall contain the information given above in cleartext and the complete initial NAS message ciphered in a NAS container which is ciphered. With a NAS security context, the sent message shall also be integrity protected. In the case that the initial NAS message was protected and the AMF has the same security context, then steps 2 to 4 may be omitted In this case the AMF shall use the complete initial NAS message that is in the NAS container as the message to respond to.
Step 2.
If the AMF is not able to find the security context locally or from last visited AMF, or if the integrity check fails, then the AMF shall initiate an authentication procedure with the UE. If the AMF fetches old security context from the last visited AMF, the AMF may decipher the NAS container with the same security context, and get the initial NAS message, then the step 2b to 4 may be omitted. If the AMF fetches new K AMF from the last visited AMF (receiving keyAmfChangeInd), the step 2b may be omitted.
Step 3.
If the authentication of the UE is successful, the AMF shall send the NAS Security Mode Command message. If the initial NAS message was protected but did not pass the integrity check (due either to a MAC failure or the AMF not being able to find the used security context) or the AMF could not decrypt the complete initial NAS message in the NAS container (due to receiving "keyAmfChangeInd" from the last visited AMF), then the AMF shall include in the Security Mode Command message a flag requesting the UE to send the complete initial NAS message in the NAS Security Mode Complete message.
Step 4.
The UE shall send the NAS Security Mode Complete message to the network in response to a NAS Security Mode Command message. The NAS Security Mode Complete message shall be ciphered and integrity protected. Furthermore the NAS Security Mode Complete message shall include the complete initial NAS message in a NAS Container if either requested by the AMF or the UE sent the initial NAS message unprotected. The AMF shall use the complete initial NAS message that is in the NAS container as the message to respond to.
Step 5.
The AMF shall send its response to the Initial NAS message. This message shall be ciphered and integrity protected.
6.4.7 Security aspects of SMS over NAS p. 72
Specific services of SMS over NAS are defined in TS 23.501, and procedures for SMS over NAS are specified in TS 23.502.
For registration and de-registration procedures for SMS over NAS, the details are specified in subclause 4.13.3.1 and 4.13.3.2 in TS 23.502. The NAS message can be protected by NAS security mechanisms.
For MO/MT SMS over NAS via 3GPP/non-3GPP when the UE has already activated NAS security with the AMF before sending/receiving SMS, the NAS Transport message shall be ciphered and integrity protected using the NAS security context by the UE/AMF as described in subclause 6.4 in the present document.