Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.12 Subscription identifier privacy
6.12.1 Subscription permanent identifier
6.12.2 Subscription concealed identifier
6.12.3 Subscription temporary identifier
6.12.4 Subscription identification procedure
6.12.5 Subscription identifier de-concealing function (SIDF)
...
...
6.12 Subscription identifier privacy p. 111
6.12.1 Subscription permanent identifier p. 111
In the 5G system, the globally unique 5G subscription permanent identifier is called SUPI as defined in TS 23.501. The SUCI is a privacy preserving identifier containing the concealed SUPI.
The SUPI is privacy protected over-the-air by using the SUCI which is described in clause 6.12.2. Handling of SUPI and privacy provisioning related to concealing the SUPI shall be done according to the requirements specified in clause 5 and details provided in clause 6.12.2.
6.12.2 Subscription concealed identifier p. 111
The SUbscription Concealed Identifier, called SUCI, is a privacy preserving identifier containing the concealed SUPI.
The UE shall generate a SUCI using a protection scheme with the raw public key, i.e. the Home Network Public Key, that was securely provisioned in control of the home network. The protection schemes shall be the ones specified in Annex C of this document or the ones specified by the HPLMN.
The UE shall construct a scheme-input from the subscription identifier part of the SUPI as follows:
- For SUPIs containing IMSI, the subscription identifier part of the SUPI includes the MSIN of the IMSI as defined in TS 23.003.
- For SUPIs taking the form of a NAI, the subscription identifier part of the SUPI includes the "username" portion of the NAI as defined in NAI RFC 7542.
- The SUPI Type as defined in TS 23.003 identifies the type of the SUPI concealed in the SUCI.
- The Home Network Identifier is set to the MCC and MNC of the IMSI as specified in 23.003 [19].
- The Routing Indicator as specified in TS 23.003.
- The Protection Scheme Identifier as specified in Annex C of this specification.
- The Home Network Public Key Identifier as specified in this document and detailed in TS 23.003.
- The Scheme Output as specified in this document and detailed in TS 23.003.
- realm part of the SUCI is set to the realm part of the SUPI.
- username part of the SUCI is formatted as specified in TS 23.003 using the SUPI Type, Routing Indicator, the Protection Scheme Identifier, the Home Network Public Key Identifier and the Scheme Output.
- if the UE is sending a Registration Request message of type "initial registration" to a PLMN for which the UE does not already have a 5G-GUTI, the UE shall include a SUCI to the Registration Request message, or
- if the UE responds to an Identity Request message by which the network requests the UE to provide its permanent identifier, the UE includes a SUCI in the Identity Response message as specified in clause 6.12.4.
- if the UE is sending a De-Registration Request message to a PLMN during an initial registration procedure for which the UE did not receive the registration accept message with 5G-GUTI, the UE shall include the SUCI used in the initial registration to the De-Registration Request message.
- if the UE is making an unauthenticated emergency session and it does not have a 5G-GUTI to the chosen PLMN, or
- if the home network has configured "null-scheme" to be used, or
- if the home network has not provisioned the public key needed to generate a SUCI.
6.12.3 Subscription temporary identifier p. 113
A new 5G-GUTI shall be sent to a UE only after a successful activation of NAS security. The 5G-GUTI is defined in TS 23.003.
Upon receiving Registration Request message of type "initial registration" or "mobility registration update" from a UE, the AMF shall send a new 5G-GUTI to the UE in the registration procedure.
Upon receiving Registration Request message of type "periodic registration update" from a UE, the AMF should send a new 5G-GUTI to the UE in the registration procedure.
Upon receiving Service Request message sent by the UE in response to a Paging message, the AMF shall send a new 5G-GUTI to the UE. This new 5G-GUTI shall be sent before the current NAS signalling connection is released or the N1 NAS signalling connection is suspended.
Upon receiving an indication from the lower layers that the RRC connection has been resumed for a UE in 5GMM-IDLE mode with suspend indication in response to a Paging message, the AMF shall send a new 5G-GUTI to the UE. This new 5G-GUTI shall be sent before the current NAS signalling connection is released or the suspension of the N1 NAS signalling connection.
5G-TMSI generation should be following the best practices of unpredictable identifier generation.
A new I-RNTI shall be sent to a UE only after a successful activation of AS security.
On transition of UE to RRC INACTIVE state requested by gNB during RRC Resume procedure or RNAU procedure, the gNB shall assign a new I-RNTI to the UE.
6.12.4 Subscription identification procedure p. 114
The subscriber identification mechanism may be invoked by the serving network when the UE cannot be identified by means of a temporary identity (5G-GUTI). In particular, it should be used when the serving network cannot retrieve the SUPI based on the 5G-GUTI by which the subscriber identifies itself on the radio path.
The mechanism described in Figure 6.12.4-1 allows the identification of a UE on the radio path by means of the SUCI.
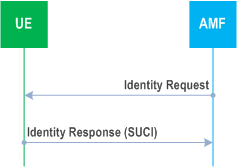
The mechanism is initiated by the AMF that requests the UE to send its SUCI.
The UE shall calculate a fresh SUCI from SUPI using the Home Network Public Key, and respond with Identity Response carrying the SUCI. The UE shall implement a mechanism to limit the frequency at which the UE responds with a fresh SUCI to an Identity Request for a given 5G-GUTI.
AMF may initiate authentication with AUSF to receive SUPI as specified in clause 6.1.3.
In case the UE registers for Emergency Services and receives an Identity Request, the UE shall use the null-scheme for generating the SUCI in the Identity Response.
6.12.5 Subscription identifier de-concealing function (SIDF) p. 114
SIDF is responsible for de-concealing the SUPI from the SUCI. When the Home Network Public Key is used for encryption of SUPI, the SIDF shall use the Home Network Private Key that is securely stored in the home operator's network to decrypt the SUCI. The de-concealment shall take place at the UDM. Access rights to the SIDF shall be defined, such that only a network element of the home network is allowed to request SIDF.