Content for TS 33.501 Word version: 19.0.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
D Algorithms for ciphering and integrity protection
D.1 Null ciphering and integrity protection algorithms
D.2 Ciphering algorithms
D.2.1 128-bit Ciphering algorithms
D.2.1.1 Inputs and outputs
D.2.1.2 128-NEA1
D.2.1.3 128-NEA2
D.2.1.4 128-NEA3
D.3 Integrity algorithms
D.3.1 128-Bit integrity algorithms
D.3.1.1 Inputs and outputs
D.3.1.2 128-NIA1
D.3.1.3 128-NIA2
D.3.1.4 128-NIA3
D.4 Test Data for the security algorithms
D.4.1 General
D.4.2 128-NEA1
D.4.3 128-NIA1
D.4.4 128-NEA2
D.4.5 128-NIA2
D.4.6 128-NEA3
D.4.7 128-NIA3
...
...
D (Normative) Algorithms for ciphering and integrity protection p. 246
D.1 Null ciphering and integrity protection algorithms p. 246
The NEA0 algorithm shall be implemented such that it generates a KEYSTREAM of all zeroes (see clause D.2.1). The length of the KEYSTREAM generated shall be equal to the LENGTH input parameter. The generated KEYSTREAM requires no other input parameters but the LENGTH. Apart from this, all processing performed in association with ciphering shall be exactly the same as with any of the ciphering algorithms specified in this Annex.
The NIA0 algorithm shall be implemented in such way that it shall generate a 32 bit MAC-I/NAS-MAC and XMAC-I/XNAS-MAC of all zeroes (see clause D.3.1). Replay protection shall not be activated when NIA0 is activated. All processing performed in association with integrity (except for replay protection) shall be exactly the same as with any of the integrity algorithms specified in this Annex except that the receiver does not check the received MAC.
The NIA0 shall not be used for signalling radio bearers (SRBs) except for unauthenticated emergency sessions for unauthenticated UEs in LSM.
The NIA0 shall not be used for data radio bearers (DRBs).
D.2 Ciphering algorithms p. 246
D.2.1 128-bit Ciphering algorithms p. 246
D.2.1.1 Inputs and outputs p. 246
The input parameters to the ciphering algorithm are a 128-bit cipher key named KEY, a 32-bit COUNT, a 5-bit bearer identity BEARER, the 1-bit direction of the transmission i.e. DIRECTION, and the length of the keystream required i.e. LENGTH. The DIRECTION bit shall be 0 for uplink and 1 for downlink.
Figure D.2.1.1-1 illustrates the use of the ciphering algorithm NEA to encrypt plaintext by applying a keystream using a bit per bit binary addition of the plaintext and the keystream. The plaintext may be recovered by generating the same keystream using the same input parameters and applying a bit per bit binary addition with the ciphertext.
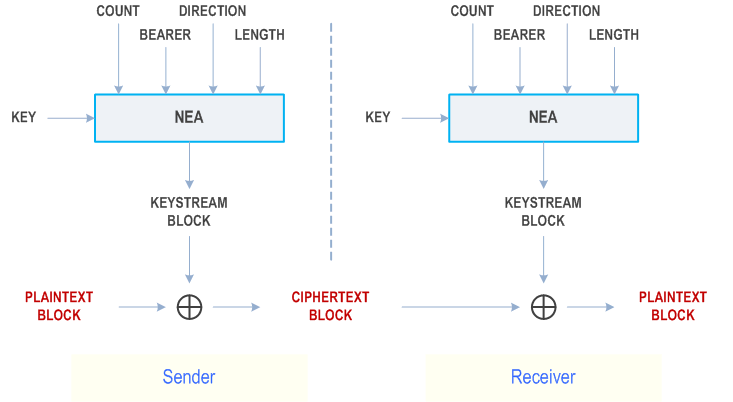
Based on the input parameters the algorithm generates the output keystream block KEYSTREAM which is used to encrypt the input plaintext block PLAINTEXT to produce the output ciphertext block CIPHERTEXT.
The input parameter LENGTH shall affect only the length of the KEYSTREAM BLOCK, not the actual bits in it.
D.2.1.2 128-NEA1 p. 247
D.2.1.3 128-NEA2 p. 247
D.2.1.4 128-NEA3 p. 247
D.3 Integrity algorithms p. 247
D.3.1 128-Bit integrity algorithms p. 247
D.3.1.1 Inputs and outputs p. 247
The input parameters to the integrity algorithm are a 128-bit integrity key named KEY, a 32-bit COUNT, a 5-bit bearer identity called BEARER, the 1-bit direction of the transmission i.e. DIRECTION, and the message itself i.e. MESSAGE. The DIRECTION bit shall be 0 for uplink and 1 for downlink. The bit length of the MESSAGE is LENGTH.
Figure D.3.1.1-1 illustrates the use of the integrity algorithm NIA to authenticate the integrity of messages.
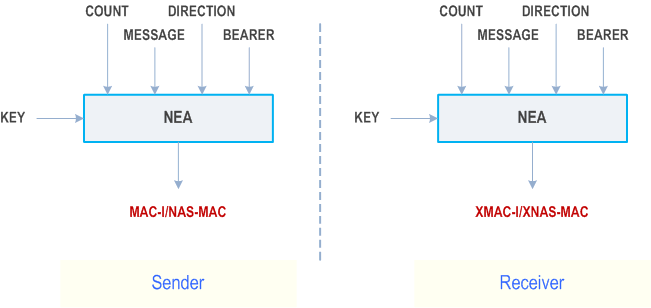
Based on these input parameters the sender computes a 32-bit message authentication code (MAC-I/NAS-MAC) using the integrity algorithm NIA. The message authentication code is then appended to the message when sent. For integrity protection algorithms, the receiver computes the expected message authentication code (XMAC-I/XNAS-MAC) on the message received in the same way as the sender computed its message authentication code on the message sent and verifies the data integrity of the message by comparing it to the received message authentication code, i.e. MAC-I/NAS-MAC.
D.3.1.2 128-NIA1 p. 248
D.3.1.3 128-NIA2 p. 248
D.3.1.4 128-NIA3 p. 248
D.4 Test Data for the security algorithms p. 248
D.4.1 General p. 248
Annex D.4 contains references to the test data for each of the specified algorithms.
D.4.2 128-NEA1 p. 248
For 128-NEA1 is the test data for UEA2 in TS 35.217 can be reused directly as there is an exact, one-to-one mapping between UEA2 inputs and 128-NEA1 inputs.
D.4.3 128-NIA1 p. 248
For 128-NIA1 is the test data for 128-EIA1 in clause C.4 of TS 33.401 can be reused directly as there is an exact, one-to-one mapping between 128-EIA1 inputs and 128-NIA1 inputs.
D.4.4 128-NEA2 p. 248
For 128-NEA2 is the test data for 128-EEA2 in clause C.1 of TS 33.401 can be reused directly as there is an exact, one-to-one mapping between 128-EEA2 inputs and 128-NEA2 inputs.
D.4.5 128-NIA2 p. 249
For 128-NIA2 is the test data for 128-EIA2 in clause C.2 of TS 33.401 can be reused directly as there is an exact, one-to-one mapping between 128-EIA2 inputs and 128-NIA2 inputs.
D.4.6 128-NEA3 p. 249
For 128-NEA3 is the test data for 128-EEA3 in TS 35.223 can be reused directly as there is an exact, one-to-one mapping between 128-EEA3 inputs and 128-NEA3 inputs.
D.4.7 128-NIA3 p. 249
For 128-NIA3 is the test data for 128-EIA3 in TS 35.223 can be reused directly as there is an exact, one-to-one mapping between 128-EIA3 inputs and 128-NIA3 inputs.