Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.15 UE parameters update via UDM control plane procedure security mechanism
6.15.1 General
6.15.2 Security mechanisms
6.15.2.1 Procedure for UE Parameters Update
6.15.2.2 UE Parameters Update Counter
...
...
6.15 UE parameters update via UDM control plane procedure security mechanism p. 120
6.15.1 General p. 120
This clause describes the security functions necessary to update the UE parameters using the UDM control plane procedure specified in TS 23.502. The security functions are described in the context of the functions supporting the delivery of UE Parameters Update Data from the UDM to the UE after the UE has successfully registered to the 5G network.
If the control plane procedure for UE parameters update is supported by the UDM, the AUSF shall store the latest KAUSF after the completion of the latest primary authentication.
The content of UE Parameters Update Data and the conditions for sending it to the UE as well as how it is handled at the UE are specified in TS 24.501.
6.15.2 Security mechanisms p. 120
6.15.2.1 Procedure for UE Parameters Update p. 120
The UDM may decide to perform UE parameters update anytime after the UE has been successfully authenticated and registered to the 5G system. The security procedure for the UE parameters update is described below in Figure 6.15.2.1-1:
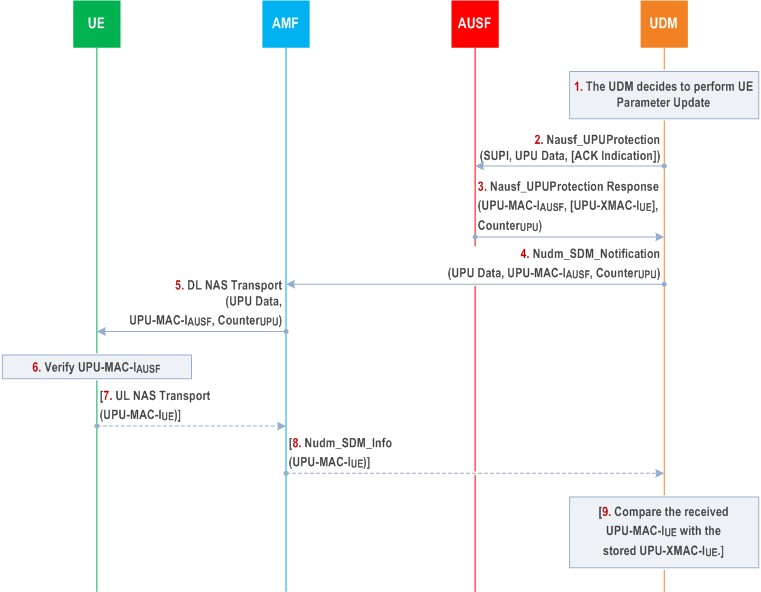
Step 1.
If the UDM supports Home triggered authentication (see clause 6.1.5), the UDM based on its local policy may decide to trigger a primary authentication to refresh the UPU counter based on the value of counter received in step 3.
The UDM decides to perform the UE Parameters Update (UPU) using the control plane procedure while the UE is registered to the 5G system. If the final consumer of any of the UE parameters to be updated (e.g., the updated Routing ID Data) is the USIM, the UDM shall protect these parameters using a secured packet mechanism (see TS 31.115) to update the parameters stored on the USIM. The UDM shall then prepare the UE Parameters Update Data (UPU Data) by including the parameters protected by the secured packet, if any, as well as any UE parameters for which final consumer is the ME (see TS 24.501).
Step 2-3.
The UDM shall invoke Nausf_UPUProtection service operation message by including the UPU Data to the AUSF to get UPU-MAC-IAUSF and CounterUPU as specified in subclause 14.1.4 of this document. The UDM shall select the AUSF that holds the latest KAUSF of the UE.
If the UDM decided that the UE is to acknowledge the successful security check of the received UE Parameters Update Data, then the UDM shall include the ACK Indication in the Nausf_UPUProtection service operation message to signal that it also needs the expected UPU-MAC-IIUE, as specified in subclause 14.1.4 of this document.
The details of the CounterUPU is specified in subclause 6.15.2.2 of this document. The inclusion of UE Parameters Update Data in the calculation of UPU-MAC-IAUSF allows the UE to verify that it has not been tampered by any intermediary. The expected UPU-MAC-IIUE allows the UDM to verify that the UE received the UE Parameters Update Data correctly.
Step 4.
The UDM shall invoke Nudm_SDM_Notification service operation, which includes the UPU transparent container if the AMF supports UPU transparent container, or includes individual IEs comprising the UE Parameters Update Data, UPU-MAC-IAUSF, CounterUPU within the Access and Mobility Subscription data. If the UDM requests an acknowledgement, it shall temporarily store the expected UPU-MAC-IIUE.
Step 5.
Upon receiving the Nudm_SDM_Notification message, the AMF shall send a DL NAS Transport message to the served UE. The AMF shall include in the DL NAS Transport message the transparent container if received from the UDM in step 4. Otherwise, if the UDM provided individual IEs in step 4, then the AMF shall construct a UPU transparent container.
Step 6.
On receiving the DL NAS Transport message, the UE shall calculate the UPU-MAC-IAUSF in the same way as the AUSF (as specified in Annex A.19) on the received UE Parameters Update Data and the CounterUPU and verify whether it matches the UPU-MAC-IAUSF value received within the UPU transparent container in the DL NAS Transport message. If the verification of UPU-MAC-IAUSF is successful and the UPU Data contains any parameters that is protected by secured packet (see TS 31.115), the ME shall forward the secured packet to the USIM using procedures in TS 31.111. If the verification of UPU-MAC-IAUSF is successful and the UPU Data contains any parameters that is not protected by secure packet, the ME shall update its stored parameters with the received parameters in UDM Updata Data.
Step 7.
If the UDM has requested an acknowledgement from the UE and the UE has successfully verified and updated the UE Parameters Update Data provided by the UDM, then the UE shall send the UL NAS Transport message to the serving AMF. The UE shall generate the UPU-MAC-IUE as specified in Annex A.20 and include the generated UPU-MAC-IUE in a transparent container in the UL NAS Transport message.
Step 8.
If a transparent container with the UPU-MAC-IUE was received in the UL NAS Transport message, the AMF shall send a Nudm_SDM_Info request message with the transparent container to the UDM.
Step 9.
If the UDM indicated that the UE is to acknowledge the successful security check of the received UE Parameters Update Data, then the UDM shall compare the received UPU-MAC-IUE with the expected UPU-MAC-IIUE that the UDM stored temporarily in step 4.
6.15.2.2 UE Parameters Update Counter p. 121
The AUSF and the UE shall associate a 16-bit counter, CounterUPU, with the key KAUSF.
The UE shall initialize the CounterUPU to 0x00 0x00 when the newly derived KAUSF is stored (see clause 6.2.2.2). The UE shall store the UPU counter . If the USIM supports both 5G parameters storage and 5G parameters extended storage, then CounterUPU shall be stored in the USIM. Otherwise, CounterUPU shall be stored in the non-volatile memory of the ME.
To generate the UPU-MAC-IAUSF, the AUSF shall use the CounterUPU. The CounterUPU shall be incremented by the AUSF for every new computation of the UPU-MAC-IAUSF. The CounterUPU is used as freshness input into UPU-MAC-IAUSF and UPU-MAC-IUE derivations as described in the Annex A.19 and Annex A.20 respectively, to mitigate the replay attack. The AUSF shall send the value of the CounterUPU (used to generate the UPU-MAC-IAUSF) along with the UPU-MAC-IAUSF to the UE. The UE shall only accept CounterUPU value that is greater than stored CounterUPU value. The UE shall update the stored CounterUPU with the received CounterUPU, only if the verification of the received UPU-MAC-IAUSF is successful. The UE shall use the CounterUPU received from the UDM, when deriving the UPU-MAC-IUE for the UE Parameters Upadate Data acknowledgement.
The AUSF and the UE shall maintain the CounterUPU for lifetime of the KAUSF.
The AUSF that supports the UE parameters update using control plane procedure shall initialize the CounterUPU to 0x00 0x01 when the newly derived KAUSF is stored (see clause 6.2.2.1). The AUSF shall set the CounterUPU to 0x00 0x02 after the first calculated UPU-MAC-IAUSF, and monotonically increment it for each additional calculated UPU-MAC-IAUSF. The UPU Counter value of 0x00 0x00 shall not be used to calculate the UPU-MAC-IAUSF and UPU-MAC-IUE.
The AUSF shall suspend the UE Parameters Update protection service for the UE, if the CounterUPU associated with the KAUSF of the UE, is about to wrap around. When a fresh KAUSF is generated for the UE, the CounterUPU at the AUSF is reset to 0x00 0x01 as defined above and the AUSF shall resume theUE Parameters Update protection service for the UE.