Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.1.3 Authentication procedures
6.1.3.1 Authentication procedure for EAP-AKA'
6.1.3.2 Authentication procedure for 5G AKA
6.1.3.2.0 5G AKA
6.1.3.2.2 RES* verification failure in SEAF or AUSF or both
6.1.3.3 Synchronization failure or MAC failure
6.1.3.3.1 Synchronization failure or MAC failure in USIM
6.1.3.3.2 Synchronization failure recovery in Home Network
...
...
6.1.3 Authentication procedures p. 48
6.1.3.1 Authentication procedure for EAP-AKA' p. 48
EAP-AKA' is specified in RFC 5448. The 3GPP 5G profile for EAP-AKA' is specified in the normative Annex F.
The selection of using EAP-AKA' is described in subclause 6.1.2 of the present document.
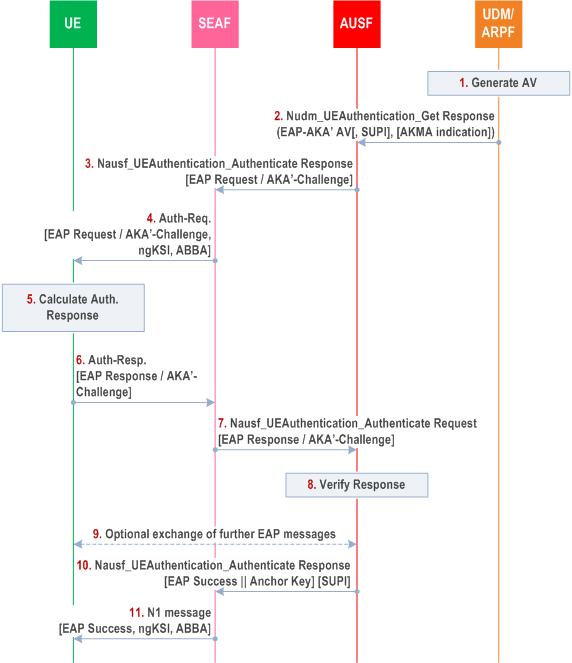
The authentication procedure for EAP-AKA' works as follows, cf. also Figure 6.1.3.1-1:
Step 1.
The further steps taken by the AUSF upon receiving a successfully verified EAP-Response/AKA'-Challenge message are described in subclause 6.1.4 of the present document.
If the EAP-Response/AKA'-Challenge message is not successfully verified, the subsequent AUSF behaviour is determined according to the home network's policy.
If AUSF and SEAF determine that the authentication was successful, then the SEAF provides the ngKSI and the KAMF to the AMF.
The UDM/ARPF shall first generate an authentication vector with Authentication Management Field (AMF) separation bit = 1 as defined in TS 33.102. The UDM/ARPF shall then compute CK' and IK' as per the normative Annex A and replace CK and IK by CK' and IK'.
Step 2.
The UDM shall subsequently send this transformed authentication vector AV' (RAND, AUTN, XRES, CK', IK') to the AUSF from which it received the Nudm_UEAuthentication_Get Request together with an indication that the AV' is to be used for EAP-AKA' using a Nudm_UEAuthentication_Get Response message.
In case SUCI was included in the Nudm_UEAuthentication_Get Request, UDM will include the SUPI in the Nudm_UEAuthentication_Get Response.
If a subscriber has an AKMA subscription, the UDM shall include the AKMA indication and Routing indicator in the Nudm_UEAuthentication_Get Response.
Step 3.
The AUSF shall send the EAP-Request/AKA'-Challenge message to the SEAF in a Nausf_UEAuthentication_Authenticate Response message.
Step 4.
The SEAF shall transparently forward the EAP-Request/AKA'-Challenge message to the UE in a NAS message Authentication Request message. The ME shall forward the RAND and AUTN received in EAP-Request/AKA'-Challenge message to the USIM. This message shall include the ngKSI and ABBA parameter. In fact, SEAF shall include the ngKSI and ABBA parameter in all EAP-Authentication request message. The ngKSI will be used by the UE and AMF to identify the partial native security context that is created if the authentication is successful. The SEAF shall set the ABBA parameter as defined in Annex A.7.1. During an EAP authentication, the value of the ngKSI and the ABBA parameter sent by the SEAF to the UE shall not be changed.
Step 5.
At receipt of the RAND and AUTN, the USIM shall verify the freshness of the AV' by checking whether AUTN can be accepted as described in TS 33.102. If so, the USIM computes a response RES. The USIM shall return RES, CK, IK to the ME. If the USIM computes a Kc (i.e. GPRS Kc) from CK and IK using conversion function c3 as described in TS 33.102, and sends it to the ME, then the ME shall ignore such GPRS Kc and not store the GPRS Kc on USIM or in ME. The ME shall derive CK' and IK' according to Annex A.3.
If the verification of the AUTN fails on the USIM, then the USIM and ME shall proceed as described in subclause 6.1.3.3.
Step 6.
The UE shall send the EAP-Response/AKA'-Challenge message to the SEAF in a NAS message Auth-Resp message.
Step 7.
The SEAF shall transparently forward the EAP-Response/AKA'-Challenge message to the AUSF in Nausf_UEAuthentication_Authenticate Request message.
Step 8.
The AUSF shall verify the message by comparing the XRES and RES, and if the AUSF has successfully verified this message it shall continue as follows, otherwise it shall return an error to the SEAF. AUSF shall inform UDM about the authentication result (see subclause 6.1.4 of the present document for details on linking authentication confirmation).
Step 9.
The AUSF and the UE may exchange EAP-Request/AKA'-Notification and EAP-Response /AKA'-Notification messages via the SEAF. The SEAF shall transparently forward these messages.
Step 10.
The AUSF derives EMSK from CK' and IK' as described in RFC 5448 and Annex F. The AUSF uses the most significant 256 bits of EMSK as the KAUSF and then calculates KSEAF from KAUSF as described in clause A.6. The AUSF shall send an EAP Success message to the SEAF inside Nausf_UEAuthentication_Authenticate Response, which shall forward it transparently to the UE. Nausf_UEAuthentication_Authenticate Response message contains the KSEAF. If the AUSF received a SUCI from the SEAF when the authentication was initiated (see subclause 6.1.2 of the present document), then the AUSF shall also include the SUPI in the Nausf_UEAuthentication_Authenticate Response message. The AUSF stores the KAUSF based on the home network operator's policy according to clause 6.1.1.1.
Step 11.
The SEAF shall send the EAP Success message to the UE in the N1 message. This message shall also include the ngKSI and the ABBA parameter. The SEAF shall set the ABBA parameter as defined in Annex A.7.1.
The key received in the Nausf_UEAuthentication_Authenticate Response message shall become the anchor key, KSEAF in the sense of the key hierarchy in subclause 6.2 of the present document. The SEAF shall then derive the KAMF from the KSEAF, the ABBA parameter and the SUPI according to Annex A.7 and send it to the AMF. On receiving the EAP-Success message, the UE derives EMSK from CK' and IK' as described in RFC 5448 and Annex F. The ME uses the most significant 256 bits of the EMSK as the KAUSF and then calculates KSEAF in the same way as the AUSF. The UE shall derive the KAMF from the KSEAF, the ABBA parameter and the SUPI according to Annex A.7.
6.1.3.2 Authentication procedure for 5G AKA p. 51
6.1.3.2.0 5G AKA p. 51
5G AKA enhances EPS AKA [10] by providing the home network with proof of successful authentication of the UE from the visited network. The proof is sent by the visited network in an Authentication Confirmation message.
The selection of using 5G AKA is described in subclause 6.1.2 of the present document.
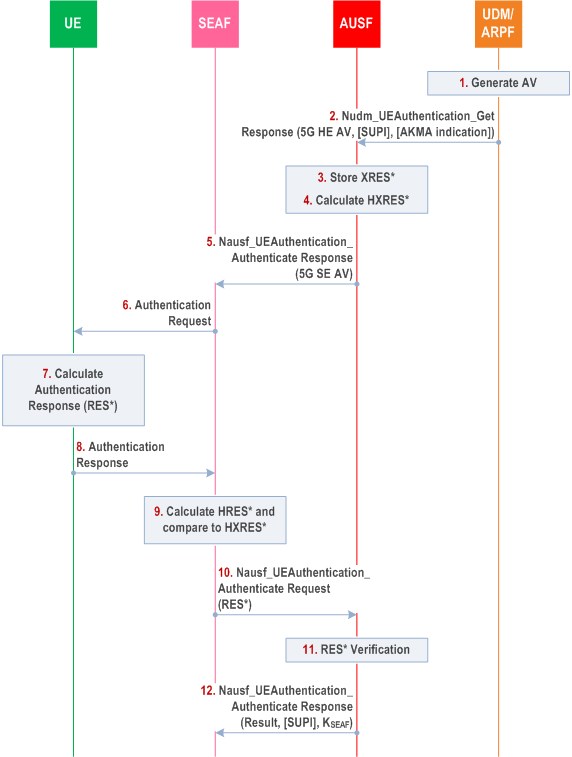
The authentication procedure for 5G AKA works as follows, cf. also Figure 6.1.3.2-1:
UEAuthentication_Authenticate Response message shall become the anchor key in the sense of the key hierarchy as specified in subclause 6.2 of the present document. Then the SEAF shall derive the KAMF from the KSEAF, the ABBA parameter and the SUPI according to Annex A.7. The SEAF shall provide the ngKSI and the KAMF to the AMF. If the AUSF indicates that the authentication was successful from the home network point of view, then the AMF shall initiate NAS security mode command procedure (see clause 6.7.2) with the UE, to take the newly generated partial native 5G NAS security context into use. Upon receiving the valid NAS Security Mode Command message from the AMF, the UE shall consider the performed primary authentication as successful.
If a SUCI was used for this authentication, then the SEAF shall only provide ngKSI and KAMF to the AMF after it has received the Nausf_UEAuthentication_Authenticate Response message containing KSEAF and SUPI; no communication services will be provided to the UE until the SUPI is known to the serving network.
The further steps taken by the AUSF after the authentication procedure are described in subclause 6.1.4 of the present document.
Step 1.
If the authentication was successful, the key KSEAF received in the Nausf_
For each Nudm_UEAuthentication_Get Request, the UDM/ARPF shall create a 5G HE AV. The UDM/ARPF does this by generating an AV with the Authentication Management Field (AMF) separation bit set to "1" as defined in TS 33.102. The UDM/ARPF shall then derive KAUSF (as per Annex A.2) and calculate XRES* (as per Annex A.4). Finally, the UDM/ARPF shall create a 5G HE AV from RAND, AUTN, XRES*, and KAUSF.
Step 2.
The UDM shall then return the 5G HE AV to the AUSF together with an indication that the 5G HE AV is to be used for 5G AKA in a Nudm_UEAuthentication_Get Response. In case SUCI was included in the Nudm_UEAuthentication_Get Request, UDM will include the SUPI in the Nudm_UEAuthentication_Get Response after deconcealment of SUCI by SIDF.
If a subscriber has an AKMA subscription, the UDM shall include the AKMA indication and Routing indicator in the Nudm_UEAuthentication_Get Response.
Step 3.
The AUSF shall store the XRES* temporarily together with the received SUCI or SUPI.
Step 4.
The AUSF shall then generate the 5G AV from the 5G HE AV received from the UDM/ARPF by computing the HXRES* from XRES* (according to Annex A.5) and KSEAF from KAUSF (according to Annex A.6), and replacing the XRES* with the HXRES* and KAUSF with KSEAF in the 5G HE AV.
Step 5.
The AUSF shall then remove the KSEAF and return the 5G SE AV (RAND, AUTN, HXRES*) to the SEAF in a Nausf_UEAuthentication_UEAuthentication Response.
Step 6.
The SEAF shall send RAND, AUTN to the UE in a NAS message Authentication Request. This message shall also include the ngKSI that will be used by the UE and AMF to identify the KAMF and the partial native security context that is created if the authentication is successful. This message shall also include the ABBA parameter. The SEAF shall set the ABBA parameter as defined in Annex A.7.1. The ME shall forward the RAND and AUTN received in NAS message Authentication Request to the USIM.
Step 7.
At receipt of the RAND and AUTN, the USIM shall verify the freshness of the received values by checking whether AUTN can be accepted as described in TS 33.102. If so, the USIM computes a response RES. The USIM shall return RES, CK, IK to the ME. If the USIM computes a Kc (i.e. GPRS Kc) from CK and IK using conversion function c3 as described in TS 33.102, and sends it to the ME, then the ME shall ignore such GPRS Kc and not store the GPRS Kc on USIM or in ME. The ME then shall compute RES* from RES according to Annex A.4. The ME shall calculate KAUSF from CK||IK according to clause A.2. The ME shall calculate KSEAF from KAUSF according to clause A.6. An ME accessing 5G shall check during authentication that the "separation bit" in the AMF field of AUTN is set to 1. The "separation bit" is bit 0 of the AMF field of AUTN.
Step 8.
The UE shall return RES* to the SEAF in a NAS message Authentication Response.
Step 9.
The SEAF shall then compute HRES* from RES* according to Annex A.5, and the SEAF shall compare HRES* and HXRES*. If they coincide, the SEAF shall consider the authentication successful from the serving network point of view. If not, the SEAF proceed as described in subclause 6.1.3.2.2. If the UE is not reached, and the RES* is never received by the SEAF, the SEAF shall consider authentication as failed, and indicate a failure to the AUSF.
Step 10.
The SEAF shall send RES*, as received from the UE, in a Nausf_UEAuthentication_Authenticate Request message to the AUSF.
Step 11.
When the AUSF receives as authentication confirmation the Nausf_UEAuthentication_Authenticate Request message including a RES* it may verify whether the 5G AV has expired. If the 5G AV has expired, the AUSF may consider the authentication as unsuccessful from the home network point of view. Upon successful authentication, the AUSF stores the KAUSF based on the home network operator's policy according to clause 6.1.1.1. AUSF shall compare the received RES* with the stored XRES*. If the RES* and XRES* are equal, the AUSF shall consider the authentication as successful from the home network point of view. AUSF shall inform UDM about the authentication result (see sub-clause 6.1.4 of the present document for linking with the authentication confirmation).
Step 12.
The AUSF shall indicate to the SEAF in the Nausf_UEAuthentication_Authenticate Response whether the authentication was successful or not from the home network point of view. If the authentication was successful, the KSEAF shall be sent to the SEAF in the Nausf_UEAuthentication_Authenticate Response. In case the AUSF received a SUCI from the SEAF in the authentication request (see subclause 6.1.2 of the present document), and if the authentication was successful, then the AUSF shall also include the SUPI in the Nausf_UEAuthentication_Authenticate Response message.
6.1.3.2.1 Void
6.1.3.2.2 RES* verification failure in SEAF or AUSF or both p. 53
This clause describes how RES* verification failure in the SEAF or in the AUSF shall be handled.
In step 9 in Figure 6.1.3.2-1, the SEAF shall compute HRES* from RES* according to Annex A.5, and the SEAF shall compare HRES* and HXRES*. If they don't coincide, then the SEAF shall consider the authentication as unsuccessful.
The SEAF shall proceed with step 10 in Figure 6.1.3.2-1 and after receiving the Nausf_UEAuthentication_Authenticate Response message from the AUSF in step 12 in Figure 6.1.3.2-1, proceed as described below:
UEAuthentication_Authenticate Response message from the AUSF as expected, then the SEAF shall either reject the authentication to the UE or initiate an Identification procedure with the UE.
-
If the AUSF has indicated in the Nausf_
UEAuthentication_ Response message to the SEAF that the verification of the RES* was not successful in the AUSF, orAuthenticate - if the verification of the RES* was not successful in the SEAF,
6.1.3.3 Synchronization failure or MAC failure p. 53
6.1.3.3.1 Synchronization failure or MAC failure in USIM p. 53
This clause describes synchronisation failure or MAC failure in USIM.
In step 7 in Figure 6.1.3.2-1 when 5G AKA is used; or in step 5 in Figure 6.1.3.1-1 when EAP-AKA' is used, at the receipt of the RAND and AUTN, if the verification of the AUTN fails, then the USIM indicates to the ME the reason for failure and in the case of a synchronisation failure passes the AUTS parameter (see TS 33.102) to the ME.
If 5G AKA is used: The ME shall respond with NAS message Authentication Failure with a CAUSE value indicating the reason for failure. In case of a synchronisation failure of AUTN (as described in TS 33.102), the UE also includes AUTS that was provided by the USIM. Upon receipt of an authentication failure message, the AMF/SEAF may initiate new authentication towards the UE. (see TS 24.501).
If EAP-AKA' is used: The ME shall proceed as described in RFC 4187 and RFC 5448 for EAP-AKA'.
6.1.3.3.2 Synchronization failure recovery in Home Network p. 54
Upon receiving an authentication failure message with synchronisation failure (AUTS) from the UE, the SEAF sends an Nausf_UEAuthentication_Authenticate Request message with a "synchronisation failure indication" to the AUSF and the AUSF sends an Nudm_UEAuthentication_Get Request message to the UDM/ARPF, together with the following parameters:
UEAuthentication_Authenticate Request message with a "synchronisation failure indication" from the AUSF (or before it is timed out).
When the UDM/ARPF receives an Nudm_UEAuthentication_Get Request message with a "synchronisation failure indication" it acts as described in clause 6.3.5 of TS 33.102 where ARPF is mapped to HE/AuC. The UDM/ARPF sends an Nudm_UEAuthentication_Get Response message with a new authentication vector for either EAP-AKA' or 5G-AKA depending on the authentication method applicable for the user to the AUSF. The AUSF runs a new authentication procedure with the UE according to clause 6.1.3.1 or clause 6.1.3.2 depending on the authentication method applicable for the user.
- RAND sent to the UE in the preceding Authentication Request, and
- AUTS received by the SEAF in the response from the UE to that request, as described in subclause 6.1.3.2.0 and subclause 6.1.3.3.1.