Content for TS 33.501 Word version: 19.0.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
6.13 Signalling procedure for PDCP COUNT check p. 116
The following procedure is used optionally by the gNB to periodically perform a local authentication. At the same time, the amount of data sent during the AS connection is periodically checked by the gNB and the UE for both up and down streams. If UE receives the Counter Check request, it shall respond with Counter Check Response message.
The gNB is monitoring the PDCP COUNT values associated to each radio bearer. The procedure is triggered whenever any of these values reaches a critical checking value. The granularity of these checking values and the values themselves are defined by the visited network. All messages in the procedure are integrity protected.
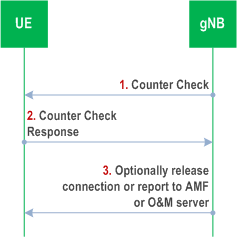
Step 1.
When a checking value is reached (e.g. the value in some fixed bit position in the hyperframe number is changed), a Counter Check message is sent by the gNB. The Counter Check message contains the most significant parts of the PDCP COUNT values (which reflect amount of data sent and received) from each active radio bearer.
Step 2.
The UE compares the PDCP COUNT values received in the Counter Check message with the values of its radio bearers. Different UE PDCP COUNT values are included within the Counter Check Response message.
Step 3.
If the gNB receives a counter check response message that does not contain any PDCP COUNT values, the procedure ends. If the gNB receives a counter check response that contains one or several PDCP COUNT values, the gNB may release the connection or report the difference of the PDCP COUNT values for the serving AMF or O&M server for further traffic analysis for e.g. detecting the attacker.