Content for TS 33.501 Word version: 18.6.0
1…
4…
5…
5.3…
5.9…
5.10…
6…
6.1.3…
6.1.4…
6.2…
6.2.2…
6.3…
6.4…
6.5…
6.6…
6.7…
6.8…
6.9…
6.10…
6.11
6.12…
6.13
6.14…
6.15…
6.16…
7…
7A…
7A.2.3…
7B…
8…
9…
10…
11…
12…
13…
13.2.2…
13.2.4…
13.3…
13.4…
14…
15…
16…
A…
B…
C…
D…
E…
F…
G…
I…
I.9…
J…
K…
M…
N…
O…
P…
R
S…
T…
U…
V…
W…
X…
Y…
Z…
13 Service Based Interfaces (SBI)
13.1 Protection at the network or transport layer
13.1.0 General
13.1.1 TLS protection between NF and SEPP
13.1.1.0 General
13.1.1.1 TLS protection based on telescopic FQDN and wildcard certificate
13.1.1.2 TLS protection based on 3gpp-Sbi-Target-apiRoot HTTP header
13.1.2 Protection between SEPPs
13.2 Application layer security on the N32 interface
13.2.1 General
...
...
13 Service Based Interfaces (SBI) p. 170
13.1 Protection at the network or transport layer p. 170
13.1.0 General |R16| p. 170
All network functions shall support mutually authenticated TLS and HTTPS as specified in RFC 9113 and RFC 9110. The identities in the end entity certificates shall be used for authentication and policy checks. Network functions shall support both server-side and client-side certificates. TLS client and server certificates shall be compliant with the SBA certificate profile specified in clause 6.1.3c of TS 33.310.
The TLS profile shall follow the profile given in clause 6.2 of TS 33.210 with the restriction that it shall be compliant with the profile given by HTTP/2 as defined in RFC 9113. TLS clients shall include the SNI extension as specified in RFC 9113.
TLS shall be used for transport protection within a PLMN unless network security is provided by other means.
13.1.1 TLS protection between NF and SEPP |R16| p. 170
13.1.1.0 General p. 170
To allow for TLS protection between the SEPP and Network Functions or SCPs within a PLMN, the SEPP shall support:
- TLS wildcard certificate for its domain name and generation of telescopic FQDN based on an FQDN obtained from the received N32-f message as specified in clause 13.1.1.1.
- using the custom HTTP header 3gpp-Sbi-Target-apiRoot, defined in clause 5.2.3.2.4 of TS 29.500, in the HTTP request originated by the NF within the SEPP's PLMN, to forward the protected HTTP Request message towards the remote PLMN as specified in clause 13.1.1.2.
13.1.1.1 TLS protection based on telescopic FQDN and wildcard certificate p. 171
A telescopic FQDN is an FQDN with a single label as the first element and the SEPP's domain as the trailer component. The label uniquely represents the original FQDN.
The SEPP shall generate a telescopic FQDN for the following messages received over N32-f:
-
a. Nnrf_
- When the SEPP receives one of the messages identified in a-c above, it shall rewrite the FQDN from the received message with a telescopic FQDN and it forwards the modified HTTP message to the target Network Function or SCP inside the PLMN.
- When the Network Function or SCP that received the telescopic FQDN in step 1 is ready to communicate with the target Network Function or SCP in another PLMN, it uses the telescopic FQDN in the Request URI of the HTTP Request. When communication between the Network Function or SCP and the SEPP that generated the telescopic FQDN is based on using the 3gpp-Sbi-Target-apiRoot custom HTTP header as specified in clause 5.2.3.2.4 of TS 29.500, the Network Function or SCP uses the telescopic FQDN in the 3gpp-Sbi-Target-apiRoot custom HTTP header of the HTTP Request. During TLS setup between the Network Function and the SEPP, the SEPP shall authenticate towards the Network Function or SCP using the wildcard certificate.
- When the SEPP receives a HTTP request from the Network Function or SCP, the SEPP shall rewrite the telescopic FQDN with the original FQDN by replacing the unique delimiter in the label with the period character and removing its own suffix part.
13.1.1.2 TLS protection based on 3gpp-Sbi-Target-apiRoot HTTP header p. 171
The NF uses the 3gpp-Sbi-Target-apiRoot HTTP header in the HTTP Request to convey the target FQDN to the SEPPs.
If PRINS is used on the N32-f interface, the following applies: The sending SEPP shall use the 3gpp-Sbi-Target-apiRoot header to obtain the apiRoot to be used in the request URI of the protected HTTP Request. It removes the 3gpp-Sbi-Target-apiRoot header before forwarding the protected HTTP Request on the N32-f interface.
If TLS is used on the N32 interface, the following applies: The sending SEPP shall replace the authority header in the HTTP Request with the FQDN of the receiving SEPP before forwarding the protected HTTP Request on the N32 interface. The sending SEPP shall not change the 3gpp-Sbi-Target-apiRoot header.
13.1.2 Protection between SEPPs |R16| p. 171
TLS shall be used for N32-c connections between the SEPPs.
The SEPP shall maintain a set of trust anchors, each consisting of a list of trusted root certificates and a list of corresponding PLMN-IDs. Any given PLMN-ID shall appear in at most one trust anchor. During N32-c connection setup, the SEPP shall map the PLMN-ID of the remote SEPP leaf (server or client) certificate to the associated trust anchor for the purposes of certificate chain verification. Only the root certificates in the associated list shall be treated as trusted during certificate chain verification. If the remote SEPP certificate contains multiple PLMN-IDs that are mapped to different trust anchors, then that certificate shall be rejected.
Operator Group Roaming Hubs SEPPs are equivalent to a network operator SEPP when they are in the same security domain and are not considered Roaming Intermediaries as detailed in this clause. The communication between a group network operator's SBA network border element and the Operator Group Roaming Hub SEPP is out of scope of the present document.
If there are no Roaming Intermediaries between the SEPPs, TLS shall be used for N32-f connections between the SEPPs. Different TLS connections are used for N32-c and N32-f. If there are Roaming Intermediaries which only offer IP routing service between SEPPs, either TLS or PRINS (application layer security) shall be used for protection of N32-f connections between the SEPPs. PRINS is specified in clause 5.9.3 (requirements) and clause 13.2 (procedures).
If TLS is selected, the SEPP shall correlate the N32-f TLS connection with the N32-c connection. If the peer network is a PLMN, the SEPP compares the PLMN-IDs contained in the SEPP TLS certificates used to establish the N32-c and N32-f connections. Specifically, if the certificate used for N32-f contains one or more PLMN-IDs that are not contained in the TLS certificate used for the corresponding N32-c, the N32-f certificate shall be rejected. If the peer network is an SNPN, the SEPP compares the SNPN-ID contained in the SEPP TLS certificates used to establish the N32-c and N32-f connections.
If there are Roaming Intermediaries which, in addition to IP routing, offer other services that require modification or observation of the information and/or additions to the information sent between the SEPPs, PRINS shall be used for protection of N32-f connections between the SEPPs.
If PRINS is used on the N32-f interface, one of the following additional transport protection methods should be applied between SEPP and Roaming Intermediary or between two Roaming Intermediaries for confidentiality and integrity protection:
- NDS/IP as specified in TS 33.210 and TS 33.310, or
- TLS VPN with mutual authentication following the profile given in clause 6.2 of TS 33.210 and clause clause 6.1.3a of TS 33.310. The identities in the end entity certificates shall be used for authentication and policy checks, with the restriction that it shall be compliant with the profile given by HTTP/2 as defined in RFC 9113.
13.2 Application layer security on the N32 interface p. 172
13.2.1 General p. 172
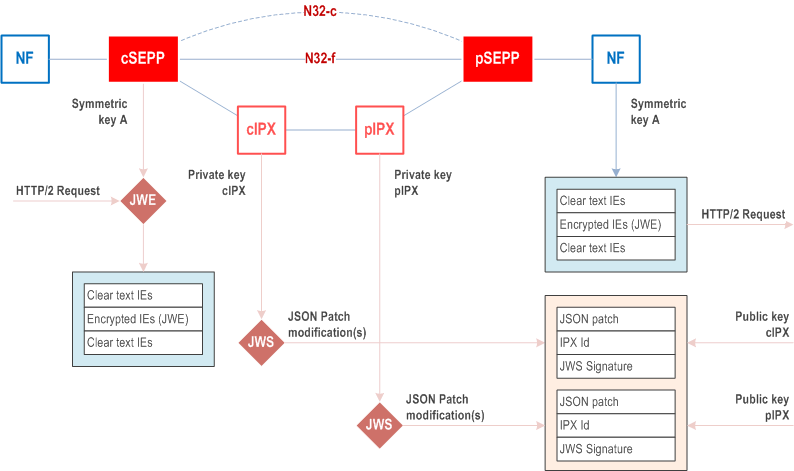
The internetwork interconnect allows secure communication between service-consuming and a service-producing NFs in different PLMNs. Security is enabled by the Security Edge Protection Proxies of both networks, henceforth called cSEPP and pSEPP respectively. The SEPPs enforce protection policies regarding application layer security thereby ensuring integrity and confidentiality protection for those elements to be protected.
It is assumed that there are interconnect providers between cSEPP and pSEPP. The interconnect provider with which the cSEPP's operator has a business relationship with is called cIPX, while the interconnect provider with which the pSEPP's operator has a business relationship with is called pIPX. There could be further interconnect providers in between cIPX and pIPX, but they are assumed to be transparent and simply forward the communication.
The SEPPs use JSON Web Encryption (JWE, specified in RFC 7516) for protecting messages on the N32-f interface, and the Roaming Intermediaries use JSON Web Signatures (JWS, specified in RFC 7515) for signing their modifications needed for their mediation services.
For illustration, consider the case where a service-consuming NF sends a message to a service-producing NF. If this communication is across PLMN operators over the N32-f interface, as shown in Figure 13.2.1-1 below, the cSEPP receives the message and applies symmetric key based application layer protection, as defined in clause 13.2 of the present document. The resulting JWE object is forwarded to roaming intermediaries. The Roaming Intermediaries (e.g., pIPX and cIPX as shown in Figure 13.2.1-1) can offer services that require modifications of the messages transported over the interconnect (N32) interface. These modifications are appended to the message as digitally signed JWS objects which contain the desired changes. The pSEPP, which receives the message from the Roaming Intermediary, validates the JWE object, extracts the original message sent by the NF, validates the signature in the JWS object and applies patches corresponding to the modifications by roaming intermediaries. The pSEPP then forwards the message to the destination NF.
The N32 interface consists of:
- N32-c connection, for management of the N32 interface, and
- N32-f connection, for sending of JWE and JWS protected messages between the SEPPs.