Content for TS 23.434 Word version: 19.2.0
0…
4…
5
6…
6.4…
6.5…
6.5.3…
7…
8…
8.2.2…
9…
9.3…
9.3.2.21…
9.3.3…
9.3.6…
9.3.11…
9.3.13…
9.3.14…
9.4…
9.4.6…
9.5…
10…
10.3…
10.3.2.22…
10.3.3…
10.3.7…
10.3.10…
10.4…
11…
11.3…
11.3.3…
11.4…
12…
12.3…
13…
14…
14.2.2.2…
14.3…
14.3.2.20…
14.3.2.40…
14.3.3…
14.3.3.3…
14.3.4…
14.3.4.6
14.3.4.7…
14.3.4A…
14.3.4A.3…
14.3.4A.4…
14.3.4A.6…
14.3.4A.8…
14.3.4A.9…
14.3.4A.10…
14.3.5…
14.3.6…
14.3.9…
14.3.12…
14.4…
15…
16…
17…
18…
A
B…
9.3.14 Location profiling for supporting location service enablement
9.3.14.1 Location profiling
9.3.14.2 Procedure of Location profiling for location service
9.3.15 Location service registration procedure
9.3.16 Location information unsubscribe procedure
9.3.17 Monitor location unsubscribe procedure
9.3.18 Location service registration update procedure
9.3.19 Location service deregistration procedure
...
...
9.3.14 Location profiling for supporting location service enablement |R18| p. 82
9.3.14.1 Location profiling p. 82
The location management server enhanced with the Fuse Location Function(FLF) supports the creation of location profiles for location service at the application enablement layer and the mapping of location profiles to one or more vertical applications. Location profiling is based on the vertical driven hybrid positioning requirements and policies.
The example of attributes that can be used for the location profiles is specified in Annex D.
9.3.14.2 Procedure of Location profiling for location service p. 82
The procedure includes the translation of the vertical request to a location profile and the derivation of the requested location information report.
Pre-condition:
The Location Management Server has configured a set of location service profiles.
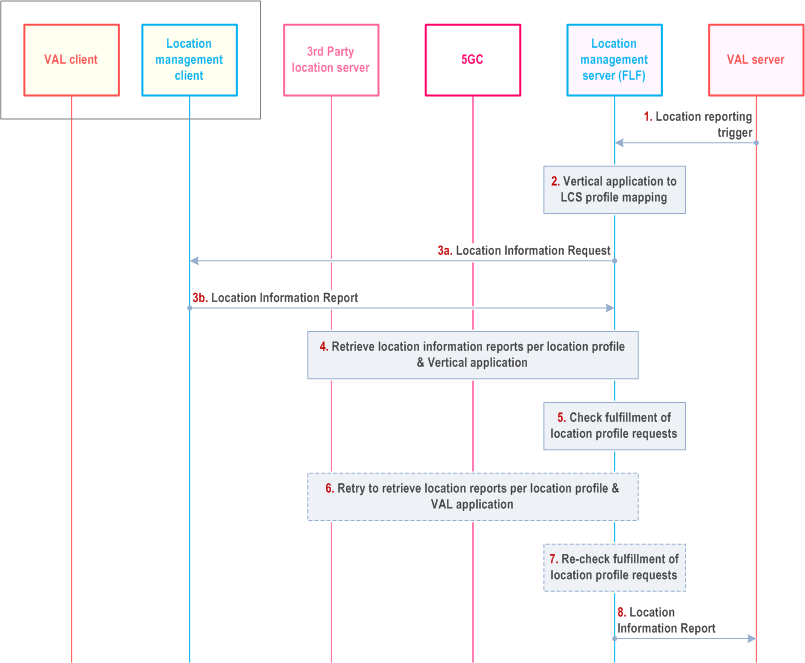
Step 1.
The LM Server receives a location reporting trigger from VAL server and activates a location reporting procedure as defined in clause 9.3.5.
Step 2.
The Fused Location Function determines a mapping of the vertical location services to a location service profile based on the location request information, the location profiles and the location capability of VAL UE which registered to the LM Server before.
Step 3a.
The LM Server requests from the LMC the location information of the target VAL UE optionally with the requested location information (the access type, positioning method) based on the determined location profiles in LM server obtained in step 2.
Step 3b.
The LM Client responds to the LM Server the location report based on the request.
Step 4.
The LM Server performs a location information request to one or more of the following (based on the location profile):
Step 5.
- to GMLC directly or via NEF (as defined in TS 23.273), acting as AF.
- to 3rd party location servers.
The Fused Location Function calculates the location information based on combined location reports from step 3~4 and checks whether the location reports fulfil the location profile requirements.
Step 6-7.
If the requirements are not fulfilled, the LM Server will repeat the step 3~5 iteratively to request location information and re-check whether the requirements are met or not.
Step 8.
If the requirements are fulfilled, the LM Server sends the location information report to the VAL server.
9.3.15 Location service registration procedure |R18| p. 83
Before the Location Management Server requesting the location information for the target UE, the Location Management Client may register the available location services to the LM Server to report the UE's location capabilities.
Figure 9.3.15-1 illustrates the procedure of client-triggered location service registration.
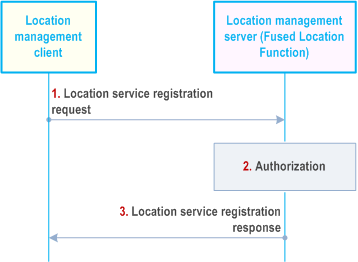
Step 1.
The LM Client of a VAL UE sends location service registration request to the LM Server, with the identifier of the UE (e.g. GPSI) and UE-based location capabilities.
Step 2.
The LM Server checks authorization for the VAL UE's registration request.
Step 3.
After successful authorization, LM Server sends location service registration response to the LM Client and stores the UE identifier information and location capabilities.
9.3.16 Location information unsubscribe procedure |R18| p. 83
Figure 9.3.16-1 illustrates the high level procedure of location information unsubscribe request. The same procedure can be applied for the location management client and other entities that would like to unsubscribe to the VAL UE's location information.
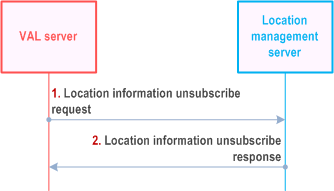
Step 1.
The VAL server sends location information unsubscribe request to the location management server to unsubscribe the subscription to the VAL UE's location information.
Step 2.
The location management server replies with location information unsubscribe response indicating the unsubscribe status.
9.3.17 Monitor location unsubscribe procedure |R18| p. 84
Figure 9.3.17-1 illustrates the high level procedure of location monitoring unsubscribe request. The same procedure can be applied for other entities that would like to unsubscribe the subscription to monitor the VAL UE's location in a given area of interest.
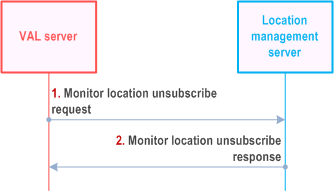
Step 1.
The VAL server sends Monitor location unsubscribe request to the location management server to unsubscribe the subscription to monitor the VAL UE's location in a given area of interest.
Step 2.
The location management server replies with Monitor location unsubscribe response indicating the unsubscribe status.
9.3.18 Location service registration update procedure |R18| p. 84
Figure 9.3.18-1 illustrates the procedure of client-triggered location service registration update. The Location Management Client may update its supported location capabilities (e.g. location access type, position methods) which has registered to the Location Management Server before.
Pre-condition:
The Location Management Client has registered to the Location Management Server.
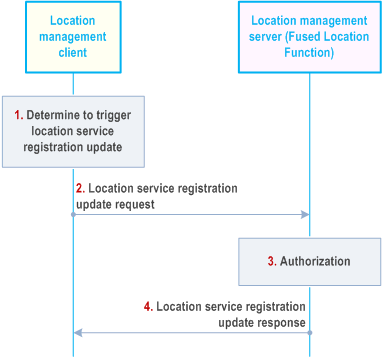
Step 1.
The LM Client decides to trigger the registration update request to LM Server to update the location capabilities which have registered to the LM Server before.
Step 2.
The LM Client sends location service registration update request to the LM Server with the identifier of the VAL UE, the VAL service ID and updated location capabilities.
Step 3.
The LM server checks the authorization for the VAL UE's registration update request. If the authorization is successful, the LM server will update the UE's location capabilities received in step 2.
Step 4.
The LM Server sends location service registration update response to the LM Client.
9.3.19 Location service deregistration procedure |R18| p. 85
Figure 9.3.19-1 illustrates the procedure of client-triggered location service deregistration. By deresgistration, the Location Management Client may deregister the available location services which have registered to the Location Management Server before.
Pre-condition:
The Location Management Client has registered to the Location Management Server.
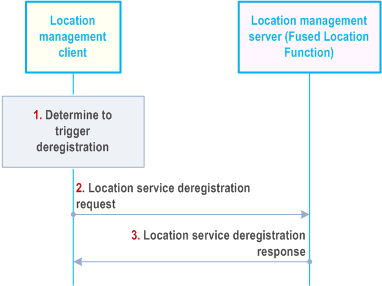
Step 1.
The LM Client decides to trigger the deresgistration request to LM Server to deregister the location services which have registered to the LM Server before.
Step 2.
The LM Client sends location service deregistration request to the LM Server with the identifier of the UE.
Step 3.
The LM Server sends location service deregistration response to the LM Client and removes all registration information of the UE.