Content for TS 23.558 Word version: 19.2.0
0…
5…
6…
6.2a…
6.2b…
6.3…
6.4…
7…
8…
8.3…
8.3.3…
8.3.3.3…
8.4…
8.4.3…
8.4.4…
8.5…
8.6…
8.6.3…
8.6.4…
8.6.6…
8.7…
8.8…
8.8.2.5…
8.8.2A…
8.8.3…
8.8.4…
8.8.5…
8.9…
8.14…
8.14.3…
8.15…
8.17…
8.17.3…
8.17.4…
8.18…
8.19…
8.20…
9…
A…
A.4…
A.5…
B…
E…
8.6.4 AC information exposure API
8.6.4.1 General
8.6.4.2 Procedures
8.6.4.2.1 General
8.6.4.2.2 Subscribe
8.6.4.2.3 Notify
8.6.4.2.4 Subscription update
8.6.4.2.5 Unsubscribe
8.6.4.3 Information flows
8.6.4.3.1 General
8.6.4.3.2 AC information subscription request
8.6.4.3.3 AC information subscription response
8.6.4.3.4 AC information notification
8.6.4.3.5 AC information subscription update request
8.6.4.3.6 AC information subscription update response
8.6.4.3.7 AC information unsubscribe request
8.6.4.3.8 AC information unsubscribe response
8.6.4.4 APIs
8.6.4.4.1 General
8.6.4.4.2 Eees_AppClientInformation_Subscribe operation
8.6.4.4.3 Eees_AppClientInformation_Notify operation
8.6.4.4.4 Eees_AppClientInformation_UpdateSubscription operation
8.6.4.4.5 Eees_AppClientInformation_Unsubscribe operation
8.6.5 UE Identifier API
8.6.5.1 General
8.6.5.2 Procedure
8.6.5.3 Information flows
8.6.5.3.1 General
8.6.5.3.2 UE Identifier API request
8.6.5.3.3 UE Identifier API response
8.6.5.4 APIs
8.6.5.4.1 General
8.6.5.4.2 Eees_UEIdentifier_Get operation
...
...
8.6.4 AC information exposure API p. 133
8.6.4.1 General p. 133
AC information exposure enables EASs to obtain information about capabilities of ACs from the EESs. This information may facilitate communications between EASs and ACs, e.g. push notifications. The information shared is subject to access control as well as privacy and security mechanisms.
8.6.4.2 Procedures p. 133
8.6.4.2.1 General p. 133
Void
8.6.4.2.2 Subscribe p. 133
Figure 8.6.4.2.2-1 illustrates the AC information subscription procedure between the EAS and the EES.
Pre-conditions:
- The EAS is registered with the EES; and
- The AC Profiles of the ACs on the UE are available at the EEC on the UE.
Step 1.
The EAS sends an AC information subscription request to the EES. The request may contain filters to retrieve information about particular ACs e.g. AC profile parameters or parameter ranges to be matched, specific UE Identifiers, location ranges, etc.
Step 2.
Upon receiving the request from the EAS, the EES performs an authorization check to verify whether the EAS has authorization to perform the operation. The EES determines the matching AC information corresponding to the filter provided and composes a result. The EES stores the subscription information for future processing.
Step 3.
The EES sends an AC information subscription response to the EAS with the result composed in step 2.
8.6.4.2.3 Notify p. 134
Figure 8.6.4.2.3-1 illustrates the AC information notification procedure between the EES and the EAS.
Pre-conditions:
- The EAS subscribed for AC information at the EES.
Step 1.
The EES is triggered for AC information updates, e.g. it receives an EEC registration request, it determines if it matches the filter provided by the EAS, e.g. if the AC Geographical Service Area is included in the EAS provided Geographical Service Area.
Step 2.
The EES sends an AC information notification to the EAS.
8.6.4.2.4 Subscription update p. 134
Figure 8.6.4.2.4-1 illustrates the AC information subscription update procedure between the EAS and the EES.
Pre-conditions:
- The EAS has subscribed for AC information as described in clause 8.6.4.2.2.
Step 1.
The EAS sends an AC information subscription update request to the EES. The request may contain updated filters to retrieve information about particular ACs e.g. AC profile parameters or parameter ranges to be matched, specific UE Identifiers, location ranges, etc.
Step 2.
Upon receiving the request from the EAS, the EES performs an authorization check to verify whether the EAS has authorization to perform the operation. If authorized, the EES updates the stored subscription information.
Step 3.
The EES sends an AC information subscription update response to the EAS.
8.6.4.2.5 Unsubscribe p. 135
Figure 8.6.4.2.5-1 illustrates the AC information unsubscribe procedure between the EAS and the EES.
Pre-conditions:
- The EAS has subscribed for AC information as described in clause 8.6.4.2.2.
Step 1.
The EAS sends an AC information unsubscribe request to the EES.
Step 2.
Upon receiving the request from the EAS, the EES performs an authorization check to verify whether the EAS has authorization to perform the operation. If authorized, the EES cancels the subscription as requested in step 1.
Step 3.
The EES sends an AC information unsubscribe response to the EAS.
8.6.4.3 Information flows p. 135
8.6.4.3.1 General p. 135
Void
8.6.4.3.2 AC information subscription request p. 135
Table 8.6.4.3.2-1 describes the information flow for an AC information subscription request from the EAS to the EES.
| Information element | Status | Description |
|---|---|---|
| EASID | M | The identifier of the EAS. |
| Security credentials | M | Security credentials of the EAS. |
| Subscription type | M | Choice of "One time" or "Event based" determining the type of processing requested. |
| Notification Target Address | M | The Notification Target Address (e.g. URL) where the notifications destined for the EAS should be sent to. |
| Filters | O | List of characteristics for discovery purposes, as detailed in Table 8.6.4.3.2-2. |
| Event conditions | O | Parameters indicating notification event conditions e.g. number of notifications instances, subscription timeout, etc. |
| Trigger parameters | O | Parameters indicating notification triggering conditions e.g. EEC registration, EAS discovery. |
| Information element | Status | Description |
|---|---|---|
| ACID(s) | O | List of identities of AC(s) to be matched |
| UE ID(s) | O | List of UE identifiers to be matched |
| AC Type(s) | O | List of categories or types of ACs (e.g. V2X) to be matched |
| ECSP ID(s) | O | Identifier(s) for the ECSP associated with the EEC. |
| Operation Schedule | O | EAS operation schedule (e.g. time windows) to be matched |
| Geographical Service Area | O | EAS service area for identifying UEs with matching expected geographical location(s) (e.g. route). This geographic information can express a geographic point, polygon, route, signalling map, or waypoint set. |
| Topological Service Area | O | EAS service area for identifying UEs with matching expected topological location(s). See possible formats in Table 8.2.7-1. |
| Maximum AC Service KPIs (NOTE) | O | Maximum value for identifying the ACs to be matched. Both Minimum required AC Service KPIs and Expected AC Service KPIs from the AC Profiles provided during registration (Table 8.4.2.3.2-1) and/or discovery subscription (Table 8.5.3.4-1) need to be lower than this value. |
| Min AC Service KPIs (NOTE) | O | Minimum value for identifying the ACs to be matched. Both Minimum required AC Service KPIs and Expected AC Service KPIs from the AC Profiles provided during registration (Table 8.4.2.3.2-1) and/or discovery subscription (Table 8.5.3.4-1) need to be greater than this value. |
| UE location(s) | O | List of locations (e.g. routes) of the UE(s) for which the request applies |
| EAS bundle indication | O | Indicator for identifying ACs which include EAS bundle information in the AC Profile and the EAS bundle includes the requesting EAS. If Bundle ID or EAS bundle requirements filters are not included, the presence of this IE signifies that all ACs which include EAS bundle information in the AC Profile match. |
| > Bundle ID | O | A bundle ID as described in clause 7.2.10 for identifying ACs with EAS bundle information in the AC Profile and with matching bundle EAS identification information. |
| > Bundle type | O | Type of the EAS bundle as described in clause 7.2.10. |
| > EAS bundle requirements | O | Bundle requirements (as described in clause 8.2.10) for identifying ACs with EAS bundle information in the AC Profile and with matching bundle requirements. |
| > Partial EAS bundle determination | O | Indicator for identifying ACs which include EAS bundle information in the AC Profile but for which only an EAS subset has been determined by EES. |
|
NOTE:
Maximum and minimum AC Service KPIs values may be provided for any IEs from Table 8.2.3-1.
|
||
8.6.4.3.3 AC information subscription response p. 137
Table 8.6.4.3.3-1 describes the information flow for the AC information subscription response from EAS to the EES.
| Information element | Status | Description |
|---|---|---|
| Successful response | O | Indicates that the subscription request was successful. |
| > Subscription ID | M | Subscription identifier corresponding to the subscription. |
| Failure response | O | Indicates that the subscription request failed. |
| > Cause | O | Indicates the cause of subscription request failure |
8.6.4.3.4 AC information notification p. 138
Table 8.6.4.3.4-1 describes the information flow for an AC information notification from the EES to the EAS.
| Information element | Status | Description |
|---|---|---|
| Subscription Identifier | M | Subscription identifier for which the notification is generated. |
| List of clients | O | List of clients matched based on the given filtering criteria, with elements listed below |
| >AC Profile(s) | M | Profiles of ACs as described in Table 8.2.2-1. |
| >UE ID(s) | O | UE identifier for the UE hosting the AC |
| >UE location(s) | O | UE location for the UE hosting the AC |
8.6.4.3.5 AC information subscription update request p. 138
Table 8.6.4.3.5-1 describes the information flow for an AC information subscription update request from the EAS to the EES.
| Information element | Status | Description |
|---|---|---|
| Security credentials | M | Security credentials of the EAS. |
| Subscription ID | M | Subscription identifier corresponding to the subscription. |
| Filter | O | List of characteristics for discovery purposes, as detailed in Table 8.6.4.3.2-2. |
| Event conditions | O | Parameters indicating notification event conditions e.g. number of notifications instances, subscription timeout, etc. |
| Trigger parameters | O | Parameters indicating notification triggering conditions e.g. EEC registration, EAS discovery. |
8.6.4.3.6 AC information subscription update response p. 138
Table 8.6.4.3.6-1 describes the information flow for the AC information subscription update response from EAS to the EES.
| Information element | Status | Description |
|---|---|---|
| Successful response | O | Indicates that the subscription update request was successful. |
| Failure response | O | Indicates that the subscription update request failed. |
| > Cause | O | Indicates the cause of subscription update request failure |
8.6.4.3.7 AC information unsubscribe request p. 139
Table 8.6.4.3.7-1 describes the information flow for an AC information unsubscribe request from the EAS to the EES.
| Information element | Status | Description |
|---|---|---|
| Security credentials | M | Security credentials of the EAS |
| Subscription Identifier | M | Subscription identifier for the corresponding subscription request. |
8.6.4.3.8 AC information unsubscribe response p. 139
Table 8.6.4.3.8-1 describes the information flow for the AC information unsubscribe response from EAS to the EES.
| Information element | Status | Description |
|---|---|---|
| Successful response | O | Indicates that the unsubscribe request was successful. |
| Failure response | O | Indicates that the unsubscribe request failed. |
| > Cause | O | Indicates the cause of unsubscribe request failure |
8.6.4.4 APIs p. 139
8.6.4.4.1 General p. 139
Table 8.6.4.4.1-1 illustrates the API for AC information exposure.
| API Name | API Operations | Operation Semantics | Consumer(s) |
|---|---|---|---|
|
Eees_ | Subscribe | Subscribe/ Notify | EAS |
| Notify | |||
| UpdateSubscription | |||
| Unsubscribe |
8.6.4.4.2 Eees_AppClientInformation_Subscribe operation p. 139
API operation name:
Eees_AppClientInformation_subscribe
Description:
The consumer subscribes to receive an AC information.
Inputs:
See clause 8.6.4.3.2.
Outputs:
See clause 8.6.4.3.3.
See clause 8.6.4.2.2 for details of usage of this operation.
8.6.4.4.3 Eees_AppClientInformation_Notify operation p. 139
API operation name:
Eees_AppClientInformation_Notify
Description:
The consumer is notified of an event by the EES.
Inputs:
See clause 8.6.4.3.4.
Outputs:
None.
See clause 8.6.4.2.3 for details of usage of this operation.
8.6.4.4.4 Eees_AppClientInformation_UpdateSubscription operation p. 140
API operation name:
Eees_AppClientInformation_UpdateSubscription
Description:
The consumer updates an existing subscription for AC information.
Inputs:
See clause 8.6.4.3.5.
Outputs:
See clause 8.6.4.3.6.
See clause 8.6.4.2.4 for details of usage of this operation.
8.6.4.4.5 Eees_AppClientInformation_Unsubscribe operation p. 140
API operation name:
Eees_AppClientInformation_Unsubscribe
Description:
The consumer unsubscribes for the previously subscribed events.
Inputs:
See clause 8.6.4.3.7.
Outputs:
See clause 8.6.4.3.8.
See clause 8.6.4.2.5 for details of usage of this operation.
8.6.5 UE Identifier API p. 140
8.6.5.1 General p. 140
EES exposes UE Identifier API to the EAS and EEC in order to provide an identifier uniquely identifying a UE. This API is used by an EAS or EEC to obtain the identifier of the UE if the EAS or EEC does not have it (e.g. hasn't already cached). This identifier, called UE ID and defined in clause 7.2.6, is used by the EAS to invoke capability APIs specific to UEs over EDGE-3 and/or EDGE-7 depending on the UE ID type.
The EAS's direct invocation of the UE Identifier API of the EES may result in UE ID not found response (e.g. if the NATed UE's public IPv4 address can't be resolved by the core network). Under such circumstances, the EAS may choose to signal its AC to trigger the UE ID query onto the EEC over EDGE-5 (see clause 8.14.2.6). In turn, the EEC would invoke the EES's UE Identifier API using the UE's CN assigned IP addresses (i.e. IPv4 and/or IPv6) which should result in return of the UE ID to the EEC and from thereon to the AC and the EAS.
8.6.5.2 Procedure p. 140
Figure 8.6.5.2-1 illustrates the interactions between the EES and the EAS or EEC.
Pre-conditions:
- The EAS or EEC is authorized to discover and to use UE Identifier API provided by the EES.
- When the EEC is used to invoke the UE Identifier API with the UE IPv6 address as the input parameter, the UE IPv6 address may or may not be NATed. If NATed however, the IPv6 may not be reused (i.e. assigned to more than one UE simultaneously). If the EEC already has the UE ID (GPSI as per clause 7.2.6), and it needs the Edge UE ID to share with an AC/EAS, this procedure can still be used to retrieve Edge UE ID.
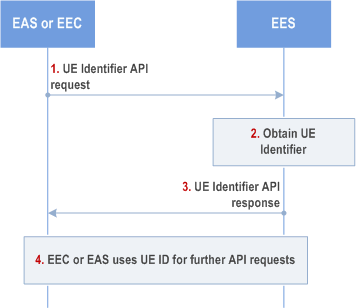
Step 1.
The EAS or EEC invokes UE Identifier API exposed by the EES. If it is the EAS invoking the API and it recognizes that the UE's IP address is a public IP address, i.e., the UE is behind a NAT, the Port Number and associated IP address should be included in user information.
Step 2.
The EES uses the received user information in the step 1 (e.g. IP address) and obtains the UE identifier by interacting with NEF as specified in clause 4.15.10 of TS 23.502. If it is the EEC invoking the API with only UE IP address, it shall be interpreted by EES that EEC is requesting the UE ID for interaction with EES (hence EES shall use its own AF Identifier towards NEF and consequently the UE ID is EES specific). When the EES needs to interact with the NEF's Nnef_UEId_Get (seeclause 4.15.10 of TS 23.502 "AF specific UE ID retrieval") as per EAS request, the EES may use either its own AF Identifier or EASID as AF Identifier instead of its own AF Identifier.
Step 3.
The EES provides the UE identifier to the EAS or to EEC (i.e. whichever invoked the API). The UE identifier returned in the response which is referred to as UE ID may be the 3GPP Core Network assigned UE ID (aka AF-specific UE ID; see clause 4.15.10 of TS 23.502) or the EES-generated Edge UE ID as defined in clause 7.2.9. If UE ID (GPSI as per clause 7.2.6) is included in the request received from EEC, the EES can provide the Edge UE ID based on the received UE ID and step 2 can be skipped. For EEC requesting the UE ID for interaction with EES, the EES returns its 3GPP Core Network assigned UE ID (aka AF specific UE ID, which is a GPSI in the form of an External ID as per clause 7.2.6) to the EEC.
Step 4.
The EAS uses the UE ID received in step 3 to invoke capability exposure API(s) provided by the EES over EDGE-3 and/or EDGE-7 depending on the UE ID type. The EEC can use the UE ID which is EES specific received in step 3 to invoke API(s) provided by the EES over EDGE-1 reference point.
8.6.5.3 Information flows p. 141
8.6.5.3.1 General p. 141
The following information flows are specified for UE Identifier API:
- UE Identifier request and response.
8.6.5.3.2 UE Identifier API request p. 141
Table 8.6.5.3.2-1 describes information elements for the UE Identifier API request from the EAS or EEC to the EES.
| Information element | Status | Description |
|---|---|---|
| Requestor Identifier (NOTE 4) | O | Identifier of the requestor (i.e. EASID or EECID). |
| User information (NOTE 1) (NOTE 3) | O | Information about the User or UE available in the EAS or EEC, e.g. IP address. |
| UE ID (NOTE 2) (NOTE 3) | O | UE ID in the form of GPSI as per clause 7.2.6. |
| EAS ID list (NOTE 4) | O | Identifier of the EAS(s) for which the UE IDs are requested for by EAS or EEC given the User information (e.g. IP address). |
| EAS Provider ID | O | Identifier of the ASP that provides the EAS. |
| Application Port ID (NOTE 5) | O | Application Port ID, as defined in TS 23.502, associated with the EAS. |
| Security Credentials | M | Security credentials of the EAS or EEC. |
|
NOTE 1:
This IE is Mandatory when EAS invoke the UE ID API. When EEC invokes the API, if available, this IE contains both UE's private IPv6 address (due to the existence of NAT66) and UE's private IPv4 address. When EAS invokes the API, it may recognize the UE IP address is a public IP address different from the actual UE IP address (private IP address), i.e., the UE is behind a NAT, and should therefore include the Port Number and associated IP address as part of the User information.
NOTE 2:
This IE is used when invoked by the EEC and if the EEC have the UE ID already in a form not desired to be shared with the EAS.
NOTE 3:
At least one of them shall be present.
NOTE 4:
This IE is Mandatory when EAS invoke the UE ID API.
NOTE 5:
This IE may only be present when EAS invoke the UE ID API.
|
||
8.6.5.3.3 UE Identifier API response p. 142
| Information element | Status | Description |
|---|---|---|
| Successful response | O | Indicates that the UE identifier request was successful. |
| > UE ID list | M | List of all the UE IDs Identifier uniquely identifying the UE(s). |
| >> UE ID | M | AF-specific UE ID or Edge UE ID. |
| >> UE ID type | M | Indication whether the UE ID is CN assigned AF-specific UE ID or Edge UE ID. |
| >> EAS ID | O | It is present if the EAS ID was provided in the request (see EAS ID list in Table 8.6.5.3.2-1). |
| Failure response | O | Indicates that the UE identifier request failed. |
| > Cause | O | Indicates the cause of UE identifier request failure |
8.6.5.4 APIs p. 142
8.6.5.4.1 General p. 142
Table 8.6.5.4.1-1 illustrates the APIs for UE Identifier.
| API Name | API Operations | Operation Semantics | Consumer(s) |
|---|---|---|---|
| Eees_ | Get | Request/ Response | EAS, EEC |
8.6.5.4.2 Eees_UEIdentifier_Get operation p. 142
API operation name:
Eees_UEIdentifier_Get
Description:
The consumer requests identifier of a UE.
Inputs:
See clause 8.6.5.3.2.
Outputs:
See clause 8.6.5.3.3.
See clause 8.6.5.2 for details of usage of this operation.