Content for TR 22.867 Word version: 18.2.0
1…
5…
5.2…
5.3…
5.4…
5.5…
5.7…
5.8…
5.10…
5.12…
5.13…
5.15…
5.16…
5.17…
5.18…
5.20…
5.22…
5.23…
6…
8…
5.15 Distributed Energy Resources and Microgrids
5.15.1 Description
5.15.2 Pre-condition
5.15.3 Service flow
5.15.4 Post-condition
5.15.5 Existing features partly or fully covering the use case functionality
5.15.6 Potential New Requirements needed to support the use case
...
...
5.15 Distributed Energy Resources and Microgrids p. 59
5.15.1 Description p. 59
Distributed energy resources (DER) become more and more important because of its close proximity to the user side and the convenience of complementary energy forms. The potentially large number of DERs have a direct impact on the operation and power trading of the power system, affecting the security, stability and operation efficiency of the system. The concept of microgrid was introduced to aggregate and optimise DER thus reduce the negative impact on power grids. As defined in [31], a microgrid is a self-sufficient energy system that serves a discrete geographic footprint, such as a university campus, a hospital complex, a business centre, or a residential area. Within microgrids there are one or more kinds of distributed energy (solar panels, wind turbines, combined heat & power, generators) that produce its power. In addition, many newer microgrids contain energy storage, typically from batteries. Some also now have electric vehicle charging stations.
The integration of DERs into the energy system cause many challenges into the communication field. The operational conditions of a microgrid may vary rapidly due to DER contribution with low inertia of nonrotating elements and rapid changes in weather conditions (wind and solar radiation) [32]. To incorporate more renewable and alternative energy sources, the communication infrastructure must have the ability to easily handle an increasing amount of data traffic or service requests and must provide a real-time monitoring and control operation of all these nodes. A reliable communication between the system elements is crucial. In fact, any type of communication dependent electrical protection scheme requires robustness, a virtually full-time availability, and strictly bounded latency.
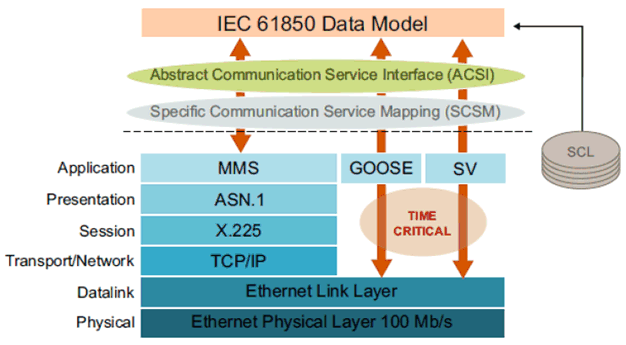
When it comes to communications architecture, IEC61850 is a widely accepted standard for automation and equipment of power utilities and DER, specifically for defining protocols for IEDs (Intelligent electronic devices) at electrical substations. IEC 61850 standard specifies the timing constraints for messages typically used in substations (Table 5.15.1-1). GOOSE (Generic Object Oriented Substation Events) and SV (Sampled Values) messages are assumed as time critical messages, having the tightest deadlines (maximum allowed transfer time) among all IEC 61850 messages, corresponding to 3 ms. While GOOSE is typically used to transfer information closely related to monitoring and control functions (circuit breaker status etc.), SV is used to transfer numerical samples of current and voltage signals. The SV protocol works on a periodic information transmission model, regularly sending messages at a fixed rate. For protection purposes, the default rate is 4000 or 4800 messages per second for, respectively, 50 or 60 Hz power systems. On the other hand, the GOOSE protocol operates in a sporadic information transmission model, where a continuous flow of data is maintained to increase communication reliability. The typical sizes of GOOSE and SV messages are, respectively, 160 and 140 bytes. GOOSE messages are transmitted at two different modes: 1) Safe operation: 1 message / second (with the bitrate of 1.28 kbit/s); 2) Emergency operation: 32 message / second (with the bitrate of 40.96 kbit/s). SV messages are transmitted at much high rate 4800 message / second (with the bitrate of 5.376 Mbit/s).
| Message Type | Example Application | Time Constraint |
|---|---|---|
| 1A-Fast messages, trip | Circuit breaker commands and states (GOOSE) | ≤3 ms |
| 1B-Fast messages, other | The same as above | ≤20 ms |
| 2-Medium speed messages | RMS values calculated from type 4 messages | ≤100 ms |
| 3-Low speed messages | Alarms, non-electrical measurements, configurations | ≤500 ms |
| 4-Raw data messages | Digital representation of electrical measurement (SV) | ≤3 ms |
| 5-File transfer functions | Files of data for recording settings | ≤1000 ms |
| 6-Time synchronization messages | IED internal clock synchronization | none |
In addition, the increasing number of renewable energy sources and micro-generators as well as the integration of a large amount of DER units in the microgrid has an impact on the scalability and the stability of the communication system. A certain level of redundancy is required in the system, e.g., backup channels, software components and devices, etc. Critical functionalities in a smart microgrid demand high reliability (99.999%) and stringent availability requirement (99.9999%).
The integration of networking and communication technologies in microgrids may cause vulnerabilities of cyber-attacks. In addition, due to the increasing number of distributed energy resources in the grid, the attack targets are also rising, producing more access points to disrupt the grid. Thus, a microgrid needs to be robust against security attacks. Table 5.15.1-2 summarizes the [34].
| Security requirements | Communication services | Security protocols | ||||||
|---|---|---|---|---|---|---|---|---|
| MMS | GOOSE | SVs | E2E PTP | P2P PTP | TLS | IPsec | MACsec | |
| Source authentication | MUST | MUST | MUST | MUST | - | x | x | - |
| Group authentication | - | - | - | MUST | MUST | - | - | x |
| Hop-by-hop integrity | - | MAY | MAY | MUST | MUST | - | - | x |
| End-to-end integrity | MUST | MUST | MUST | MUST | - | x | x | - |
| Confidentiality | MUST | - | - | - | - | x | x | x |
| Unicast key management | MUST | - | - | SHOULD | - | x | x | - |
| Multicast key management | - | MUST | MUST | SHOULD | SHOULD | - | - | x |
5.15.2 Pre-condition p. 60
The central controller(s) and IEDs have been mounted, connected, and configured during commissioning and deployment.
All devices are connected to the 5G network, and the communication is enabled using IEC 61850 standards.
5.15.3 Service flow p. 60
Communications are enabled via 5G network among the controller devices and IEDs.
SV messages are used to transfer numerical samples of current and voltage signals from Current/Voltage Transformers (CTs/VTs) to IEDs. The SV protocol works on a periodic information transmission model, regularly sending messages at a fixed rate. For protection purposes, the default rate is 4000 or 4800 messages per second for, respectively, 50 or 60 Hz power systems.
GOOSE is typically used to transfer information closely related to monitoring and control functions (circuit breaker status etc.), and GOOSE messages generally transmit binary data such as indications, alarms and tripping signals. For instance, a protection function issuing a trip command requires transfer times below 3 ms and hence, information is directly mapped into a GOOSE message. The GOOSE protocol operates in a sporadic information transmission model, where each message in a GOOSE transmission sequence has an attribute called Time allowed To Live (TTL) that informs the receiver about the maximum time to wait for the next transmission.
For such time critical applications, data is directly mapped to the Ethernet data link layer as GOOSE messages or SVs transmission using connectionless multicast addressing of frames.
5.15.4 Post-condition p. 61
5G communication runs and the "health" of the microgrid is maintained.
5.15.5 Existing features partly or fully covering the use case functionality p. 61
There is no specific description of the described use case in the existing SA1 TR/TS, and the KPI requirements are not captured yet. The use case "Distributed automated switching for isolation and service restoration" has been captured in TS 22.104 Annex A.4.4.1, while the corresponding performance requirements have been specified in Table 5.2-1 "Periodic deterministic communication service performance requirements":
As to the security requirements, there are existing requirements in clause 8.9 of TS 22.261 "Data security and privacy":
The 5G system shall support data integrity protection and confidentiality methods that serve URLLC, high data rates and energy constrained devices.
The 5G system shall support a mechanism to verify the integrity of a message as well as the authenticity of the sender of the message.
The 5G system shall support encryption for URLLC services within the requested end-to-end latency.
5.15.6 Potential New Requirements needed to support the use case p. 61
[PR.5.15-001]
The 5G system shall be able to provide periodic deterministic communication with the service performance requirements reported in the Tables below.
| Characteristic parameter | Influence quantity | Remarks | ||||||
|---|---|---|---|---|---|---|---|---|
| Communication service availability: target value | Communication service reliability: mean time between failures | End-to-end latency: maximum | Service bit rate: user experienced data rate | Message size [byte] | Transfer interval: target value | Survival time | UE speed | |
| 99.9999 % | - | < 3 ms | 4.5 Mbit/s | 140 | ≤ 1 ms | transfer interval | stationary | 50Hz power system |
| 99.9999 % | - | < 3 ms | 5.4 Mbit/s | 140 | ≤ 1 ms | transfer interval | stationary | 60Hz power system |
|
NOTE:
UE to UE communication is assumed.
|
||||||||
[PR 5.15-002]
The 5G system shall be able to provide a periodic deterministic communication with the service performance requirements reported in the Tables below.
| Communication service availability | Max Allowed End-to-end latency | Message size [byte] | UE speed | # of UEs | Service Area |
|---|---|---|---|---|---|
| > 99.9999 % | < 3 ms | 160 | Stationary | - | - |
|
NOTE:
UE to UE communication is assumed.
|
|||||