Content for TS 22.104 Word version: 19.2.0
0f…
4…
5…
5.3…
6…
A…
A.2.2…
A.2.2.4…
A.2.3…
A.4…
A.4.4…
A.4.4.3…
A.4.5…
A.4.8…
A.5…
A.6…
B…
C…
C.3
C.4…
C.5
D…
E…
A.4.8 Smart distribution transformer terminal
A.4.9 Distributed energy resources and micro-grids
A.4.10 Ensuring uninterrupted communication service availability during emergencies
...
...
A.4.8 Smart distribution transformer terminal |R18| p. 69
A smart distribution transformer terminal is usually deployed in a distribution transformer area. The terminal can support multiple energy applications simultaneously. Multiple kinds of energy data are collected by the terminal and then delivered to a energy application platform. Figure A.4.8-1 illustrates a workflow example for a smart distribution transformer terminal.
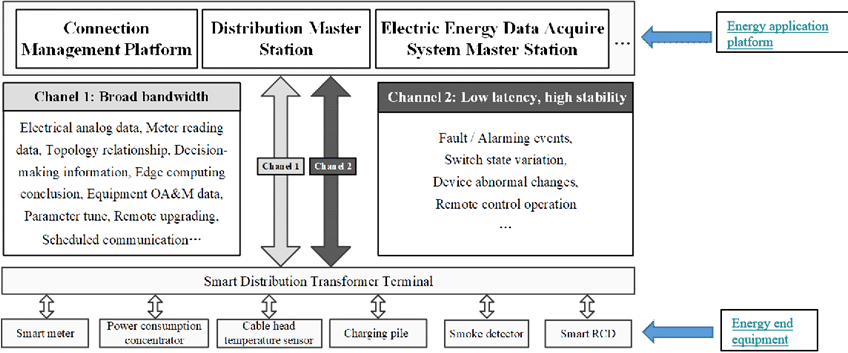
Figure A.4.8-1: Example of a smart distribution transformer terminal workflow
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
In general, the connections between the smart distribution transformer terminal and the energy application platform are provided by the 5G system. The connections between energy end equipment and smart distribution transformer terminal may be provided by 5G system. In this case, about 300 to 500 energy end devices are connected to one smart distribution transformer terminal. The average service bit rate between the smart distribution transformer terminal and an energy end device is more than 2 Mbit/s in uplink for each application. The related communication distance is between 100 m and 500 m. The associated KPI is provided in Table A.4.8-1.
| Use case # | Characteristic parameter | Influence quantity | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Communication service availability: target value | Communication service reliability: mean time between failures | End-to-end latency: maximum | Service bitrate: user experienced data rate | Message size [byte] | Transfer interval: target value | Survival time | UE speed | # of UEs | Service area | |
| 1 | >99.99% | – | 10 ms, 100 ms, 3 s (note 2) | > 2 Mbit/s (note 1) | – | – | – | – | 500 in the service area (note 3) | Communication distance is from 100 m to 500 m, (outdoor, indoor, and deep indoor) |
|
NOTE 1:
It is the smart metering application data rate between the Smart Distribution Transformer Terminal and energy end equipment. Once there are multiple smart grid applications, it is required more data rate.
NOTE 2:
It depends on different applications supported by the Smart Distribution Transformer Terminal. The less the latency is, the more applications can be supported.
NOTE 3:
The distribution area can be calculated as 3.14 x range2 and in general is between 0.031 km² and 0.79 km².
|
||||||||||
Use case#1:
smart distribution transformer terminal
A.4.9 Distributed energy resources and micro-grids |R18| p. 70
Distributed energy resources (DER) become increasingly important. The potentially large number of DERs will have an impact on security, stability, and operation efficiency of the energy grid.
The integration of DERs into the energy grid poses many challenges for the involved communication system. To incorporate more renewable and alternative energy sources, the communication infrastructure must have the ability to easily handle an increasing amount of data traffic or service requests and must provide a real-time monitoring and control operation for these distributed energy resources. A reliable communication between the DERs is crucial.
When it comes to communications architecture, IEC 61850 is a widely used standard for automation and equipment of power utilities and DER, specifically for defining protocols for IEDs (Intelligent electronic devices) at electrical substations The IEC 61850 standard specifies the timing constraints for messages typically used in substations. GOOSE (Generic Object Oriented Substation Events) and SV (Sampled Values) messages are assumed as time critical messages. They have the tightest deadlines (maximum allowed transfer time) among all IEC 61850 messages, corresponding to 3 ms. While GOOSE is typically used for transfering information related to monitoring and control functions (circuit breaker status etc.), SV is used for transfering measurement samples of current and voltage signals. The SV protocol works on a periodic information transmission model, sending messages at a fixed rate. For protection purposes, the default rate is 4000 or 4800 messages per second for 50 and 60 Hz power systems, respectively. On the other hand, the GOOSE protocol operates in a sporadic information transmission model, where a continuous flow of data is maintained to increase communication reliability. The typical sizes of GOOSE and SV messages are160 and 140 bytes, respectively. GOOSE messages are transmitted in two different modes: (1) safe operation: 1 message per second (service bit rate = 1.28 kbit/s); (2) emergency operation: 32 messages per second (service bit rate = 41.0 kbit/s). SV messages are transmitted at much higher rate, namely 4800 messages per second (service bit rate = 5.4 Mbit/s). The associated KPIs are provided in Table A.4.9-1.
| Use case # | Characteristic parameter | Influence quantity | ||||||
|---|---|---|---|---|---|---|---|---|
| Communication service availability: target value | Communication service reliability: mean time between failures | End-to-end latency: maximum | Service bitrate: user experienced data rate | Message size [byte] | Transfer interval: target value | Survival time | UE speed | |
| 1 | 99,9999 % | - | < 3 ms | 4.5 Mbit/s | 140 | ≤ 1 ms | transfer interval | stationary |
| 2 | 99,9999 % | - | < 3 ms | 5.4 Mbit/s | 140 | ≤ 1 ms | transfer interval | stationary |
| 3 | > 99.9999 % | - | < 3 ms | - | 160 | - | - | stationary |
|
NOTE:
UE to UE communication is assumed.
|
||||||||
Use case#1: Distributed energy resources and micro-grids: using SV(sample value) message with 50Hz
Use case#2: Distributed energy resources and micro-grids: using SV(sample value) message with 60Hz
Use case#3: Distributed energy resources and micro-grids: using GOOSE message
A.4.10 Ensuring uninterrupted communication service availability during emergencies |R18| p. 72
During emergencies, public mobile land networks (PLMNs) may restrict network access, which may lead to a prohibitevly low communication service availability for machine-type communication (MTC) for Smart Grid applications. An example is communication for microgrids. Microgrids are separate parts of a power grid that can be controlled and operated individually in a so-called island mode, or together with other parts of the power grid. The idea is to prioritise Smart Grid-related communication in order to ensure reliable and available communication for selected devices during emergency conditions. Existing features of a mobile network can be used to differentiate MTC of devices in a microgrid from other kind of MTC traffic or human-to-human communication. These features can help these microgrid devices to have communication service during emergencies. The communication among the microgrid devices enables co-ordination of DERs, which help the DERs can autarkically implement recovery of an islanded microgrid.
The associated KPI is provided in Table A.4.10-1.
| Characteristic parameter | Influence quantity | |||||||
|---|---|---|---|---|---|---|---|---|
| Communication service availability: target value | Communication service reliability: mean time between failures | Max Allowed End-to-end latency (note 1, note 2) | Service bitrate: user experienced data rate (note 2) | Message size [byte] | Survival time | UE speed | # of UEs | Service area |
| 99.999 9 % | - | 100 ms | < 1 kbit/s per DER | - | - | Stationary | - | - |
|
NOTE 1:
Unless otherwise specified, all communication includes 1 wireless link (UE to network node or network node to UE) rather than two wireless links (UE to UE).
NOTE 2:
It applies to both UL and DL unless stated otherwise.
|
||||||||