TS 23.228
IP Multimedia Subsystem (IMS)
V18.6.0 (PDF)
2024/06 393 p.
V17.3.0
2021/12 355 p.
V16.7.0
2021/12 351 p.
V15.5.0
2021/12 333 p.
V14.7.0
2021/12 322 p.
V13.9.0
2021/12 315 p.
V12.11.0
2021/12 312 p.
V11.11.0
2015/06 292 p.
V10.9.0
2015/06 274 p.
V9.4.0
2010/09 255 p.
V8.12.0
2010/03 250 p.
V7.16.0
2009/12 225 p.
V6.16.0
2007/03 182 p.
V5.15.0
2006/06 133 p.
- Rapporteur:
- Mr. Towle, Thomas
Qualcomm Incorporated
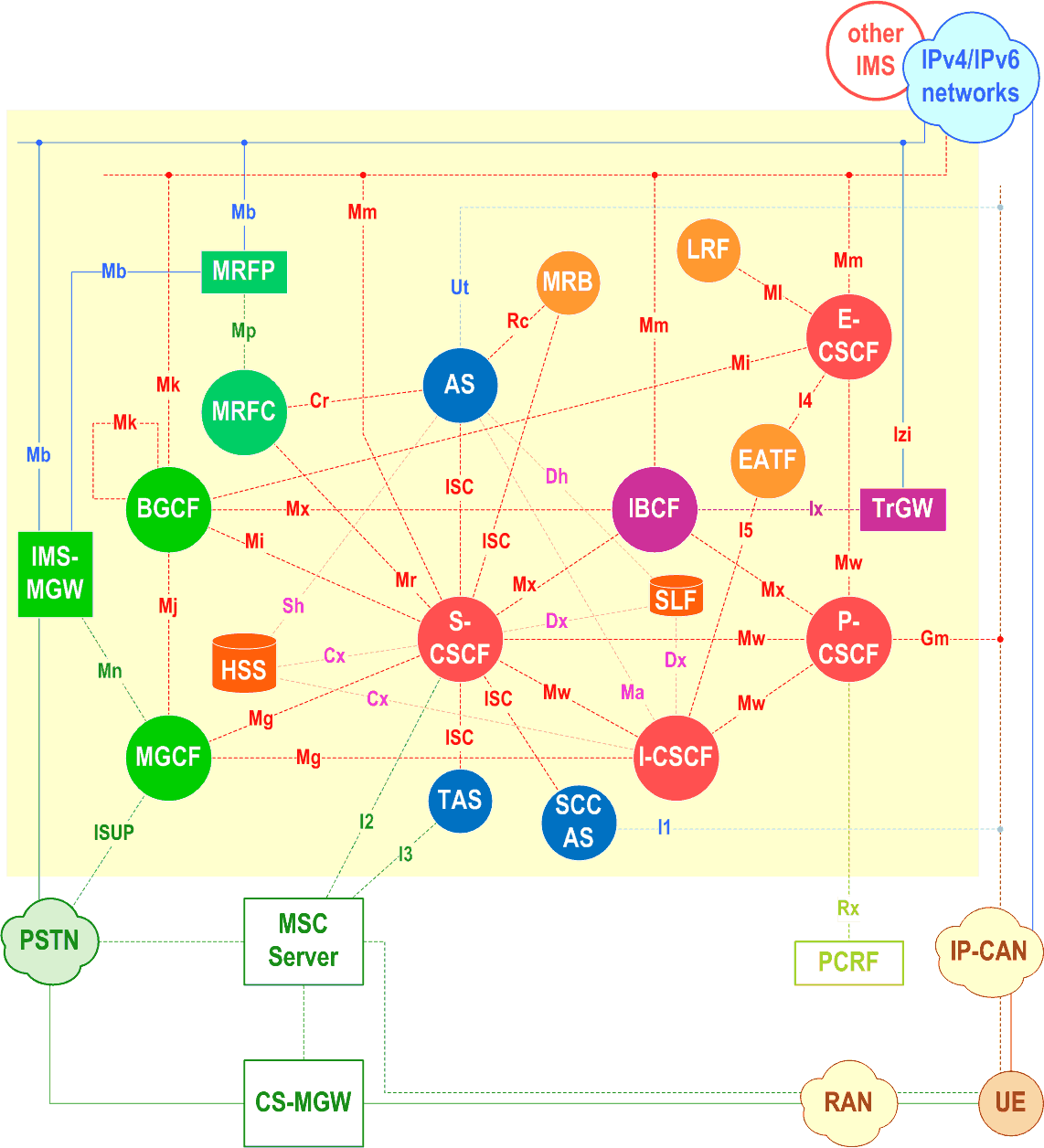
essential Table of Contents for TS 23.228 Word version: 18.6.0
each title, in the "available" or "not available yet" area, links to the equivalent title in the CONTENT