Content for TR 22.858 Word version: 18.2.0
5.15 Use case multicast service access control for legacy device(s) behind an eRG
5.16 Use case on the connection of 5G LAN with fixed IP VPN
5.17 Use case on loss of connectivity between eRG or PRAS and 5GC
5.18 Control of Customer Premises Network by Authorised Administrator
5.19 Use case: eRG supporting Multiple connectivity
5.20 Providing 5G Multicast-Broadcast Services (5MBS) for devices through eRG.
5.21 Identification, Authentication, and Authorization for Premises Radio Access Stations
5.22 Use Case for supporting external services behind eRG in CPN
...
...
5.15 Use case multicast service access control for legacy device(s) behind an eRG p. 32
5.15.1 Description p. 32
Multicast service access control is performed at 5GC, which is a mechanism to judge whether an UE is allowed to join a multicast group and receive the corresponding multicast service. When a UE requests to obtain multicast services, it sends an IGMP/MLD Join message to 5GC. When receiving the IGMP/MLD Join message, 5GC checks whether the UE is allowed to join the requested multicast group based on multicast service access control information. If the UE is allowed to join the requested multicast group, 5GC will transmit the corresponding multicast service to the UE. Otherwise, the UE is not allowed to receive the requested multicast service.
IPTV service, a kind of multicast service, is defined as multimedia services such as television/video/ audio/text/graphics/data delivered over IP-based networks managed to support the required level of QoS/QoE, security, interactivity and reliability. Set Top Box (STB) is a legacy device used to obtain IPTV service via an eRG, which is connected to 5GC as shown in Figure 5.15.1-1. Currently, the IPTV network access control granularity is RG level, which means that all STBs behind a RG will share the same access right. If network can perform a more granular multicast service access control when multiple devices connect to an eRG, users might have a better service experience.
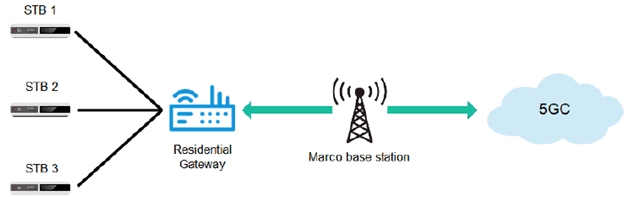
Figure 5.15.1-1: STB obtaining IPTV services via residential gateway
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
5.15.2 Pre-conditions p. 32
Mary would like to subscribe to IPTV service which is provided by IPTV network operated by IPTV operators. She needs to buy an eRG and a STB that are placed at home. The eRG is used to connect to the 5GC, while the STB is a legacy device used to obtain IPTV service via the eRG.
Mary has two children, who are Jack and David. Jack is a 5-year-old boy, while David is a 14-year-old teenager. Both of them have their own bedrooms.
5.15.3 Service Flows p. 33
Mary desires to place one STB in each bedroom so that she and her sons can enjoy IPTV services in their own bedrooms simultaneously. Moreover, she hopes that the STB in each bedroom can obtain different IPTV service according to their hobbies. Therefore, she bought another two STBs which are going to be placed in her sons' bedrooms.
For the STB placed in Jack's bedroom, Mary prefer to subscribe some cartoon IPTV channels because Jack loves watching cartoon. For the STB placed in David's bedroom, Mary prefer to subscribe some movie IPTV channels because David is a big fan of movie. As for Mary, she prefers to subscribe to news IPTV channels. Additionally, Mary wishes to restrict both Jack and David from watching IPTV channels with violent content.
Mary requests the customised IPTV network access control for her user account to IPTV network operator.
IPTV network operator updates the IPTV service access control information to 5GC according to the request from Mary so that 5GC can perform different IPTV service access control for each of the STB.
5.15.4 Post-conditions p. 33
Mary, Jack and David can enjoy their favourite IPTV channels simultaneously. Moreover, Mary does not need to worry that her sons are exposed to violent content.
5.15.5 Existing features partly or fully covering the use case functionality p. 33
Clauses 4.9.1 and 7.7.1 of TS 23.316 mention that:
- The support of IPTV services at 5GC: "The SMF controls the support of IPTV by the UPF acting as PSA using PDR, FAR, QER, URR";
- In the case of IPTV network access control based on the DHCP procedure, 5G-RG may be configured to retrieve via DHCP the IP address that it will use to access IPTV services.
- When the SMF receives the Uplink DHCP message, the SMF may be configured to insert the IPTV access control information as received in subscription data from UDM to the uplink DHCP message.
5.15.6 Potential New Requirements needed to support the use case p. 33
[PR. 5.15.6-001]
The 5G system shall support multicast service access control based on eRG subscription that enables eRG to forward authorized multicast services to multiple non-3GPP devices behind the eRG.
5.16 Use case on the connection of 5G LAN with fixed IP VPN p. 33
5.16.1 Description p. 33
This use case intends to make use of the 5G capabilities (e.g., high performance, long-distance access, mobility and security) to build a secure connection between the 5G LAN and the fixed IP VPN. For example, when people are working from home, they probably need to access the enterprise's intranet by using the devices connecting to the home 5G LAN. The connection of 5G LAN with fixed IP VPN aims to enable the devices within the 5G LAN to access the intranet through the fixed IP VPN.
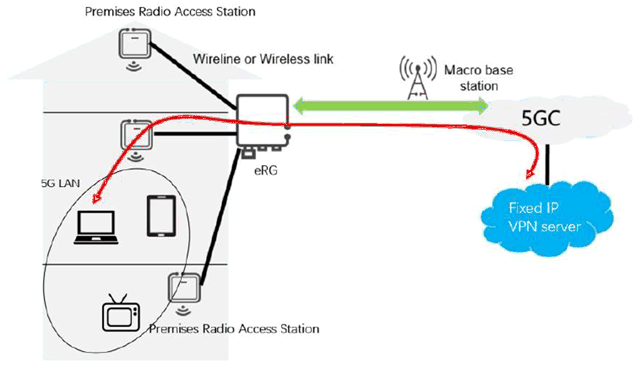
5.16.2 Pre-conditions p. 34
The following pre-conditions and assumptions apply to this use case:
- There are multiple 5G UEs within a 5G LAN-VN at home.
- There is a fixed IP VPN server deployed by the enterprise for intranet connection.
5.16.3 Service Flows p. 34
Step 1.
John works for company Tree and John is working from home.
Step 2.
John has a subscription to the 5G LAN services. John adds all the available devices (e.g., mobile phone, laptop, tablet, printer) in his house to the 5G LAN-VN.
Step 3.
John needs to access up-to-date data from his company's intranet and has an e-meeting with his colleagues.
Step 4.
John uses his laptop to build a connection to Tree's intranet through the fixed IP VPN.
Step 5.
John can access the intranet through the VPN server and he can also access the devices within the 5G LAN.
Step 6.
John sends a request to the VPN server for authorization for his mobile phone and tablet as trusted devices for intranet access through his laptop.
5.16.4 Post-conditions p. 34
While having the e-meeting with the colleagues using his phone, John can access the up-to-date data using his mobile phone or laptop or any other authorised devices connected to the home 5G LAN. John can also exchange files or data within the home 5G LAN.
5.16.5 Existing features partly or fully covering the use case functionality p. 34
The 5G system supports the interconnection of a UE with a fixed IP VPN.
3GPP TS 22.261 Section 6.26.2.2 "5G LAN-virtual network (5G LAN-VN) "
There are existing features that support the on-demand establishment of UE to UE, multicast, and broadcast private communication between members UEs of the same 5G LAN-VN. Multiple types of data communication shall be supported, at least IP and Ethernet.
A 5G system shall support 5G LAN-VNs with member UEs numbering between a few to tens of thousands.
5.16.6 Potential New Requirements needed to support the use case p. 35
[PR. 5.16.6-001]
The 5G system shall support interconnection of a 5G LAN-Virtual Network (5G LAN-VN) with a fixed IP VPN.
5.17 Use case on loss of connectivity between eRG or PRAS and 5GC p. 35
5.17.1 Description p. 35
When a UE under a PRAS coverage, whose communication path remains within the home, is either:
- using an application server on e.g. an eRG or a compute and storage resource in the home; or
- communicating with another UE or non-3GPP device within the home, as described in clauses 5.4 and 5.5.
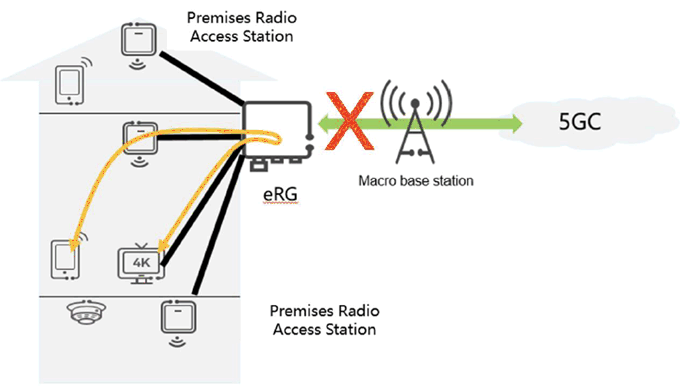
The use case considers what happens if the eRG or PRAS loses its connectivity with the 5GC.
5.17.2 Pre-conditions p. 35
- The user is using a client application on her UE.
- The UE is connected via a PRAS to an application server available on the eRG.
5.17.3 Service Flows p. 35
The connectivity between the eRG and the 5GC is lost, which is detected by the eRG.
5.17.4 Post-conditions p. 35
The user experiences no interruption with her application, as it is using an application server on the eRG. However, she can no longer use her UE for communications via 5GC.
5.17.5 Existing features partly or fully covering the use case functionality p. 36
There are existing features and requirements that cover a similar scenario to the case where the connectivity between eRG or PRAS and the 5GC is lost.
From a Home (e)Node B perspective, a requirement in clause 5.2 of TS 22.220 states:
If the connection between H(e)NB and the rest of the operator network is out of service, then it shall be possible within an operator's defined time period for the H(e)NB to deactivate the air-interface.
From an Isolated E-UTRAN operation for public safety (IOPS) perspective, TS 22.346 supports the scenario with no backhaul with a Fully Isolated E-UTRAN operation using local routing of UE-UE data traffic.
From clause 5.3.2 of TS 22.346:
An eNB supporting Isolated E-UTRAN operation shall be able to detect a loss of backhaul connection and shall be able to initiate Isolated E-UTRAN operation.
This feature is intended to be used for public safety purposes with public safety UEs.
Rel-16 IAB as defined in TS 38.331 can provide coverage even if connection to parent node is lost, as there are no mechanisms to disable IAB nodes from continuing to transmit if the connection to the parent node is lost. The latest agreement from RAN2#109bis is that IAB-DU behaviour after RLF declaration is left up to implementation. IAB-DU should be able to send RLF notification when RLF recovery fails.
For the detection of loss of connection between the CPN and the wider 5G network (core network), it is expected that this is based on the normal operation of the entities in the CPN that rely on co-ordination with the 5G network. Therefore, a new requirement is not needed to cover this case.
For the case where eRG is routing local communications within the CPN, if the connection between the CPN and the wider 5G network (core network) is lost, this requirement is covered within BBF specifications.
5.17.6 Potential New Requirements needed to support the use case p. 36
[PR. 5.17.6-001]
void
[PR. 5.17.6-002]
void
[PR. 5.17.6-003]
When the CPN has lost connectivity with the 5G network, the 5G system shall provide an operator-controlled mechanism to enable:
- in the default configuration, or under certain conditions configured by the operator, the PRAS radio interface shall be deactivated; and
- under certain other conditions configured by the operator, the CPN shall continue existing intra-CPN communication, as long as no interaction with the 5G network is needed (e.g. refreshing security keys).
5.18 Control of Customer Premises Network by Authorised Administrator p. 36
5.18.1 Description p. 36
The Customer Premises Network (CPN), including the eRG and PRAS, is at least owned, configured and managed by the customer of a public network operator. This implies that the public network operator is at least not fully in control of the configuration and management of the eRG, PRAS and CPN.
Some aspects of the eRG and PRAS can be under control of the public network operator. For example if the PRAS uses licensed frequencies the radio configuration will be under control of the PLMN. Another example could be network settings in the eRG for the interface to the 5G core network.
Other settings are configured / managed by the 'customer of the public network operator'. It is proposed to specify more clearly how this configuration and management by the 'customer of the public network operator' works. We are proposing to define the role of an Authorized Administrator. The Authorized Administrator may be authorized to configure / manage a specific node (e.g. a specific PRAS, eRG), or may be authorized to configure / manage a specific customer premises network (including one or more eRGs and/or PRASs).
5.18.2 Pre-conditions p. 37
None
5.18.3 Service Flows p. 37
Joe is installing a new Customer Premises Network in his home.
First thing, Joe installs is the eRG, in this case a wireline eRG. He has obtained the eRG from the operator and now connects it to the fixed access line.
The fixed operator has arranged that various setting in the eRG are automatically configured (e.g. using TR-069 management).
The eRG also enables Joe to configure a username / password combination that Joe can use for configuration / management of settings that are not under operator control from any device within the CPN. With this username / password, Joe is now Authorized Administrator for the eRG.
The public network operator also provides a service where Joe as Authorized Administrator can manage his eRG via a webpage (Ut interface) provided by the operator. Great aspect of this webpage is that the operator provides help with configuration. Joe is not exactly a network expert. Additionally, Joe can also manage his PRAS via a local webpage, on which some default configuration (e.g. password for the visitor accessing network via the PRAS) can be configured.
Joe now connects more devices (e.g. media server, home controller, printer, etc) to the eRG. Within the Customer Premises Network, devices can automatically discover what services other devices may provide (e.g. printer) using existing service discovery mechanisms (UPnP, zero config). Joe wants some of these services to be available also to devices that are connected to the PLMN. As Authorized Administrator of his 5GLAN service Joe can add his eRG to his 5GLAN VN group. Joe now configures which of the services from the devices on the CPN should be exposed to UEs on the PLMN. A specific service that Joe configures to be available for UEs on his 5GLAN is the configuration of his eRG.
Now Joe connects a PRAS to the eRG. Joe has obtained credentials for the PRAS from the PLMN. During installation the PRAS connects to the PLMN to obtain the settings under control of the operator (e.g. radio settings).
Joe can also log on to the PRAS using credentials (e.g. username / password) that were supplied with the PRAS. Using these credentials, Joe can configure settings of the PRAS via devices on the CPN. An example is that Joe can set whether visitor access network via his PRAS is allowed (allowing all or no visitors, or allowing specific visitors only). Joe can also use a webpage provided by his PLMN to configure his PRAS.
5.18.4 Post-conditions p. 37
Joe is Authorised Administrator of his Customer Premises Network, including PRAS and eRG. Joe can configure and manage the devices and services on his CPN from anywhere in the CPN and also from UEs that are connected to his 5GLAN VN Group.
5.18.5 Existing features partly or fully covering the use case functionality p. 37
Configuring nodes such as an eRG or PRAS is widely supported functionality.
Service discovery within a Customer Premises Network (e.g. UPnP, zero config, or proprietary protocols) is existing functionality.
Management of fixed eRG settings by an operator are specified by BBF in TR-069.
5.18.6 Potential New Requirements needed to support the use case p. 38
[PR 5.18.6-001]
The 5G system shall enable configuration and management of an eRG by both the operator of the public (mobile) network the eRG is connected to and, within the boundaries defined by the operator, by an Authorised Administrator.
[PR 5.18.6-002]
The 5G System shall support PRAS that use licensed spectrum, use unlicensed spectrum, or can use both unlicensed and licensed spectrum.
[PR 5.18.6-003]
The 5G system shall enable configuration and management of a PRAS by a PLMN and, within the boundaries defined by the operator, by an Authorised Administrator. Specifically the PLMN shall be able to configure:
- radio settings pertaining to licensed spectrum shall be configured by the PLMN that owns the spectrum. Specifically the Authorised Administrator shall be able to configure:
- Whether visitor access network via the PRAS is allowed (allowing all or no visitors, or allowing specific visitors only)
5.19 Use case: eRG supporting Multiple connectivity p. 38
5.19.1 Description p. 38
This use case is depicted in Figure 5.19.1-1. It shows the scenario where an eRG can support both wireline connection and 5G NR wireless connection simultaneously.
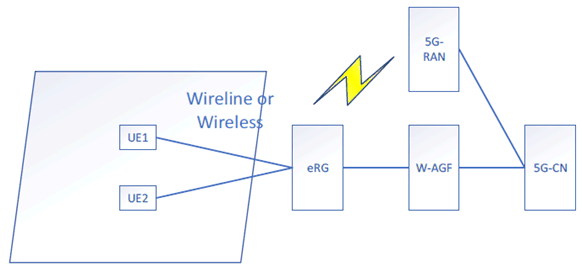
Figure 5.19.1-1: eRG supporting both wireline connection and 5G wireless connectivity
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
5.19.2 Pre-conditions p. 38
Lily moved into her new home and got IPTV service combined with internet. The IPTV providers offers 2 eRG solutions, just cable or cable with wireless. Cable provides an order magnitude higher speed but Lily has heard sometimes lot of people use the internet in the evenings and it crashes so she chooses for the one with cable access and the additional wireless capability as the wireless service can both compliment the cable and either can act as a backup in case one fails. The IPTV provider also supports the download of a media server onto the eRG to enable localized access to popular contents that Lily and her family watches often but at different times. The contents have an expiration for when it will be removed from the media server, but Lisa has the option to extend the expiration. The media server also supports streaming live high definition pay-per-view events and is able to utilize both wireless and cable accesses to meet the required QoS. Lily also has a home security alarm system. She is able to configure the eRG so the security alarm system can use the cable access as the primary access and the wireless access as the backup access. In addition, she also has IoT devices such as cameras, window and door sensors, humidity and temperature sensors, etc. Some of the IoT devices do not have subscription for cellular access and the wireless operator can configure the eRG to block traffic from those devices from being routed onto the cellular access.
Lily's friend Lisa owns a small business and also employs an eRG that supports both cable and wireless access connectivity. The eRG not only provides communication path redundancy for the business but also network management services for the devices behind the eRG. Lisa is able to configure the eRG so that the security system uses the cable access as the primary access and the wireless access as the backup access. In addition, Lisa has requested from the wireless operator a firewall function that runs on the eRG to provide network security for the business. Both Lisa and the wireless operator are able to configure the firewall for different aspects of the firewall operations. Lisa is able to configure firewall rules while the wireless operator is able to configure and manage the orchestration and update of the firewall software in the eRG.
5.19.3 Service Flows p. 39
Home eRG:
- Lily was watching TV at home, wherein the eRG used wireline connection for service.
- there was an accident in the building, the wireline was destroyed or partially destroyed. There is a lot of commotion outside with people complaining they have no service.
- eRG detects that the wireline was out of service or the data rate of wireline connection become very low.
- eRG turns on the wireless work mode and optional may provide an indication on TV screen that now cable works in multiple connection mode.
- The IPTV provider automatically downloads popular content Lily and her family watches to the media server when new content becomes available.
- Lily and her family watch the contents at different times without any service interruption.
- Lilly's husband and son like to watch professional wrestling and enjoy the live stream of pay-per-view events in high definition.
- The wireline network experiences a temporary failure where no connectivity is available for the eRG.
- The security system sends a normal communication to the cloud server to the eRG.
- The eRG detects the wireline access is not available and forwards the security system communication to the wireless access.
- The firewall function monitors all traffic entering the eRG through the wireless and wireline accesses.
- Lisa is unable to perform a download from a certain site that she knows is trustworthy and discovers the firewall function is blocking the download. Lisa configures the firewall to allow the download for this one instance only and the downloads proceeds.
- Meanwhile, a security patch for the firewall software is available and the wireless operator informs Lisa of its availability.
- Lisa schedules the update for a time when the business is close to minimize interruptions.
5.19.4 Post-conditions p. 39
Lily could continue to watch TV while the people in the same building lose IPTV service combined with internet.
Lily's husband and son enjoys live stream of professional wrestling without interruption since the media server is able to use both wireless and cable accesses.
The eRG is configured to not send unauthorize traffic onto the cellular access.
Lisa is able to protect her business network by configuring rules for the firewall while leaving the maintenance of the firewall software to the wireless operator.
5.19.5 Existing features partly or fully covering the use case functionality p. 40
Clause 6.3.2.4 of TS 22.261 Fixed broadband access
The 5G system shall support use of a relay UE that supports multiple access types (e.g. 5G RAT, WLAN access, fixed broadband access).
The 5G system shall support use of a home base station that supports multiple access types (e.g. 5G RAT, WLAN access, fixed broadband access).
3GPP TS 23.316 may include support for the hybrid access by RG.
5.19.6 Potential New Requirements needed to support the use case p. 40
[PR 5.19.6-001]
The 5G system shall support use of an eRG that is connected to the 5G Core Network over 5G fixed wireless access, fixed broadband access or hybrid access.
[PR 5.19.6-002]
The 5G system shall support a mechanism for the network operator to provide policies to the eRG on which transport (e.g. wireless, cable, etc.) is best suited for different services.
5.20 Providing 5G Multicast-Broadcast Services (5MBS) for devices through eRG. p. 40
5.20.1 Description p. 40
Broadcast/Multicast services in 5GC (5MBS) are available, potentially limited by a given service area.
A user can receive such a service either outdoor or at home.
The MNO wants to keep the benefits of multicast/broadcast distribution for in-home access. When at home, the user device (Smartphone, TV set, STB, PC, tablet…) can receive the service through the eRG. The device may be a 3GPP UE connected via a PRAS or the CPN access (e.g. Wi-Fi), or a non-3GPP device connected via the CPN access.
5.20.2 Pre-conditions p. 40
To enable this use case, following pre-conditions should be met:
- The eRG is 5G multicast/broadcast capable.
- The user is at home.
- The user device is able to connect to the eRG.
5.20.3 Service Flows p. 40
- The device connects to the eRG.
- The eRG discovers the available 5G multicast/broadcast services (if not yet discovered).
- The user selects one of the available 5G multicast/broadcast services.
- The eRG connects to the 5GC to be provisioned with the selected broadcast/multicast service.
- The eRG serves the received broadcast/multicast content to the device through the Customer Premise Network.
5.20.4 Post-conditions p. 41
The user is able to consume the selected broadcast/multicast service at home through the connection to the eRG.
5.20.5 Existing features partly or fully covering the use case functionality p. 41
Features described in TS 22.146 are all relevant for devices behind the residential gateway. However, this specific configuration is not explicitly considered, with the exception of clause 4.2.1 of TS 22.146:
- 3b) As an alternative, the Home Environment can join the user to the selected multicast group on behalf of the user, that has previously subscribed to this multicast group.
- For optimization and resource efficiency, the 5G system will select the most appropriate 3GPP or non-3GPP access technology for a service,
- Based on operator policy, the 5G system shall enable the UE to select, manage, and efficiently provision services over the 3GPP or non-3GPP access.
- The 5G system shall be able to efficiently support connectivity using fixed broadband access.
- The 5G system shall support use of a relay UE that supports multiple access types (e.g. 5G RAT, WLAN access, fixed broadband access).
- The 5G system shall support use of a home base station that supports multiple access types (e.g. 5G RAT, WLAN access, fixed broadband access).
- The UE (remote UE) can connect to the network directly (direct network connection), connect using another UE as a relay UE (indirect network connection), or connect using both direct and indirect connections. Relay UEs can be used in many different scenarios and verticals (inHome, SmartFarming, SmartFactories, Public Safety and others). In these cases, the use of relays UEs can be used to improve the energy efficiency and coverage of the system.
- The user should be able to receive MBMS user services via generic IP access systems.
5.20.6 Potential New Requirements needed to support the use case p. 41
[PR.5.20.6-001]
The 5G system shall provide means to deliver 5G multicast/broadcast services to an eRG.
[PR.5.20.6-002]
Under operator control, an eRG shall be able to receive multicast/broadcast services from its access network.
[PR.5.20.6-003]
Under operator control, an eRG, shall be able to efficiently deliver 5G multicast/broadcast services to authorized UEs and non-3GPP devices in the CPN.
5.21 Identification, Authentication, and Authorization for Premises Radio Access Stations p. 42
5.21.1 Description p. 42
To ensure providing the secure connectivity for UEs connected to 5G network via Premises Radio Access Stations (PRAS) behind eRG, this use case illustrates the need to have 5G system support for identification, authentication, and authorization of a PRAS which is not provided by the operators and has not previously been provided with credentials.
The use case is to ensure that there is 3GPP mechanism to protect the weak-link between these (assuming untrusted) PRAS(es) not provided by the operators and the eRG.
5.21.2 Pre-conditions p. 42
Alicia purchased a promotion deal from her smartphone's operator Wallowa to upgrade her home network with a bundle package including one eRG and one PRAS-A. When receiving both devices, Alicia installed the eRG and PRAS-A in the second floor and connected both via wireline. Alicia powered on both devices. Both devices register to the 5G network and are provisioned with configuration of operation settings and authorizations from the 5G network. Both eRG and the PRAS-A are up and running well to provide 5G coverage in Alicia's home.
Later, Alicia found there were still some coverage holes in the corner of the first floor so she decided to purchase one PRAS-B which is not provided by the operator and has not previously provided with credentials which thus considered as untrusted devices for the operator's network.
When returning home, Alicia logs on to her account on Operator Wallowa's portal to upgrade the eRG subscription for allowing connecting this PRAS-B and then add this PRAS-B by configuring the device settings manually or via scanning QR code of the PRAS-B and associating it to the trusted 3GPP device, eRG, which it will be connected with tethering connection. Alicia may e.g. use an application on her smartphone to assist in selecting the correct eRG to connect to and/or to set up the initial connection between the PRAS and the eRG, to avoid the PRAS to connect to the neighbor's eRG and to make it easier to perform the initial setup.
Alicia installed the PRAS-B in the first floor and connected the PRAS-B to 5G network via operator's eRG.
5.21.3 Service Flows p. 42
Step 1.
Alicia turns on the PRAS-B and connects the PRAS-B to the eRG. The PRAS-B connects to 5G network via the eRG. The 5G system detects that PRAS-B has not previously been provided with credentials and then provision a credential to the PRAS-B which may be based on eRG subscription or PRAS subscription if available. Operator Wallowa's 5G network identifies, authenticates, and authorizes the PRAS-B based on the credentials provided to the PRAS.
Step 2.
The 5G network provisions configurations, e.g. PRAS operation authorization, operator's settings, etc., to the PRAS via eRG.
Step 3.
When the PRAS-B completes installation, it reconnects to Operator Wallowa's 5G network via eRG based on provisioned PRAS-B configuration.
Step 4.
The Operator Wallowa's 5G network can identify PRAS-B, authenticate its identity, and authorize the PRAS-B operation based on the provisioned credentials and configuration of the PRAS-B.
Step 5.
Once this process is complete, the PRAS-B is successfully authenticated, authorized, configured, and connected to Operator Wallowa's network via eRG and are now fully operational.
5.21.4 Post-conditions p. 42
The 5G network ensures that the E2E connection from the 5G core network to the UE connected to the operator's PRAS-A and the PRAS-B behind eRG are secure because both PRAS(es) connected via operator's eRG are authenticated, authorized, and managed by the operator.
Alicia can now connect her UEs to both PRAS(es). She is happy that she can speak to the phone when walking around the house with good 5G service coverage.
5.21.5 Existing features partly or fully covering the use case functionality p. 43
The following service requirement in clause 26a of TS 22.101 provide the principle for user centric identifiers and authentication and authorization by the 3GPP system:
The 3GPP System shall support operators to act as User Identity provider and to authenticate users for accessing operator and non-operator deployed (i.e. external non-3GPP) services.
In clause 26a of TS 22.101 the 5G network operator can act as an identity provider for Users, e.g. an individual human user, using a UE with a certain subscription, or an application running on or connecting to a UE, or a device ("thing") behind a gateway UE. These Users are associated to the 3GPP devices (UE or gateway UE) which are 5G subscribers of the operator's network. The 5G network can identify and authenticate a User Identity based on the authenticated 3GPP device that is associated to the user. In the context of CPN, the 5G network can also enable support for identifying and authenticating an PRAS which is not provided by the operator and does not have 3GPP credentials based on the authenticated 3GPP device (eRG) that provides tethering connection.
5.21.6 Potential New Requirements needed to support the use case p. 43
[PR 5.21.6-001]
[PR 5.21.6-004]
The 5G system shall provide support for a network operator to authenticate a PRAS.
[PR 5.21.6-002]
The 5G system shall provide support for a network operator to authorize a PRAS for its use in a CPN.
[PR 5.21.6-003]
The 5G system shall support a secure mechanism for a network operator to provision a PRAS with an associated subscription and authentication credentials, and to identify a PRAS (e.g. for management purposes or to provide backhaul connectivity to the PRAS).
The 5G system shall provide mechanisms for the network operator to provision an authenticated PRAS with operation settings, e.g. carrier frequencies.
5.22 Use Case for supporting external services behind eRG in CPN p. 43
5.22.1 Description p. 43
According to clause 26a of TS 22.101, the 3GPP system can support an operator to act as identity provider and enable auto-log-in and single-sign-on to operator and non-operator services. This use case is extended from the use case 5.2, Identity provisioning to external services, in TR 22.904 which considers the applications are hosted in the cloud.
In support of external services provided behind an eRG in CPN, this use case describes the enhancement of functionalities and provides the potential service requirements in addition to those described in [11].
5.22.2 Pre-conditions p. 43
Dora is a subscriber of network operator Cannon-Beach where she has a user account and subscriptions for her UE and the eRG in the CPN. Based on the subscriptions for the eRG, operator Cannon-Beach enables a strong user authentication mechanism at the 5G system to ensure that the users accessing to the eRG in the CPN are authenticated and authorized.
Dora installs a local cloud with the application platform on a device connected to the eRG in the CPN in her home. The local cloud provides storage services for files, video, and photo album, etc. Dora configures applications/services information and registers to these applications with her user account of the network operator Cannon-Beach for the local cloud storage services hosted on the device behind the eRG in the CPN, by which each application/service is associated to a User Identity and corresponding User Profiles.
When enabling these applications/services in her user account, these services/applications can use strong user authentication from the 5G system to the applications running on the device behind the eRG in the CPN. As such, auto-log-in and single-sign-on is enabled for the applications.
5.22.3 Service Flows p. 44
Step 1.
Dora logged in her user account using her UE and her User Identity has been authenticated over the 5G system using a strong authentication mechanism for the connection to the eRG.
Step 2.
Dora opens a book on the bookshelf application hosted by the local cloud on the device behind the eRG for which the bookshelf application has been configured to require strong user authentication by the 5G system.
Step 3.
The bookshelf application accepts her request to access without further needs for Dora to provide additional credentials for the application. Since her UE has been authenticated by the 5G system and she has already been authenticated for the connection to the eRG, there is a high level of confidence regarding her identity. This level of confidence is increased based on Dora's location and the elapse time from the last authentication of her identity.
Step 4.
In the meantime, the application client of photo album on her UE automatically synchronize her photos to the photo album application on the local cloud in the CPN. Since Dora also enabled the strong user authentication by the 5G system for this photo album application, her UE can automatically sign in and upload the photos to the photo album application on the local cloud.
Step 5.
The 5G system may request her strong re-authentication so as to ensure that she is still the actual authorized user behind the UE, which is achieved by having Dora re-authenticated by operator Cannon-Beach, e.g. over the biotech sensors (e.g. for face, fingerprint, voice) of the UE.
5.22.4 Post-conditions p. 44
Because of operator's supports for non-operator services on the local cloud in the CPN and the support of strong user authentication by the 5G system, Dora is worries free to install more applications hosted by the local cloud on the devices connected to the eRG in the CPN in her home.
5.22.5 Existing features partly or fully covering the use case functionality p. 44
The following service requirement in clause 26a of TS 22.101 provide the principle for user centric identifiers and authentication and authorization by the 3GPP system:
The 3GPP System shall support operators to act as User Identity provider and to authenticate users for accessing operator and non-operator deployed (i.e. external non-3GPP) services.
26a.2.1 User Identifiers and user authentication
The 3GPP system shall be able to assess the level of confidence in the User Identity by taking into account information regarding the used mechanism for obtaining that User Identity (e.g. algorithms, key-length, time since last authentication), information from the network (e.g. UE or device in use, access technology, location).
26a.2.5 Privacy requirements
The 3GPP system shall protect the privacy of the user by transferring to a service only User Identity information that is necessary to provide the service and for which the user has consented to when registering for the service.
The use case considers that the external services are provided as a local cloud application platform behind an eRG in CPN and proposes to enable 5G system support for identity provisioning to external services behind eRG in CPN.
5.22.6 Potential Requirements p. 44
[PR 5.22.6-001]
The 5G system should support "User Identity" requirements (as defined in clause 26a of TS 22.101) for a user (human) using a CPN authorized UE to access external non-3GPP applications/services hosted in a CPN (behind a eRG).
[PR 5.22.6-002]
The 5G system shall support to allow a CPN authorized UE or non-3GPP device accessing to a CPN based on successful User Identity authentication.