Content for TS 31.102 Word version: 18.4.0
0…
3…
4…
4.2.9…
4.2.17…
4.2.26…
4.2.34…
4.2.44…
4.2.52…
4.2.60…
4.2.68…
4.2.76…
4.2.85…
4.2.93…
4.2.101…
4.2.107…
4.3…
4.4.2…
4.4.2.4…
4.4.3…
4.4.4…
4.4.5…
4.4.6…
4.4.8…
4.4.8.7…
4.4.9…
4.4.11…
4.4.11.7…
4.4.11.17…
4.4.12…
4.5…
4.6…
4.6.5…
4.6.6…
4.7
5…
5.2…
5.3…
5.4…
5.9…
6…
7…
7.1.2…
7.3…
A
B…
D
E…
G
H…
I…
L…
M…
I USIM Application Session Activation/Termination
J Example of MMS coding
J.1 Coding example for MMS User Preferences
J.2 Coding Example for MMS Issuer/User Connectivity Parameters
K Examples of VService_Id coding
...
...
I USIM Application Session Activation/Termination p. 377
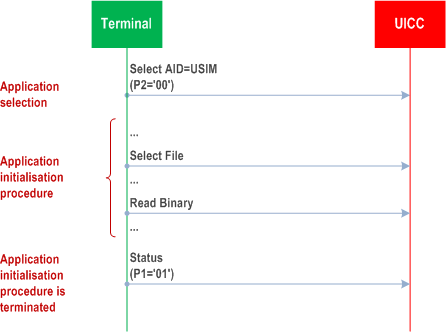
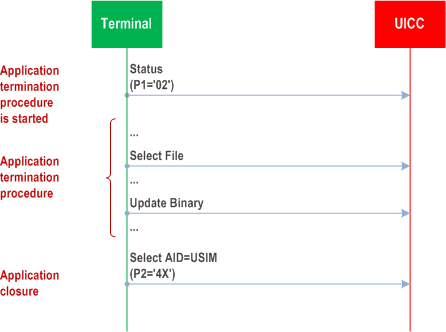
The purpose of this Annex is to illustrate the different Application Session procedures.
J Example of MMS coding |R4| p. 378
This Annex gives an example for the coding of MMS User Preferences, while the MMS User Information Preference parameters are coded according to the WAP implementation of MMS.
J.1 Coding example for MMS User Preferences p. 378
0x80 MMS Implementation Tag
0x81 MMS User Preference Profile Name Tag
0x82 MMS User Information Preference Information Tag
0x01 (Length = "1")
0x01 (MMS implementation information = "(WAP")
0x81 MMS User Preference Profile Name Tag
0x0E (Length = "14")
43 68 72 69 73 74 6D 61 73 20 43 61 72 64
(profile name = "Christmas Card"; 14 characters, 14 Bytes)
0x82 MMS User Information Preference Information Tag
0x19 (Length = "25")
0x14 0x80 (visibility: = "hide"; 2 Bytes)
0x06 0x80 (delivery report: = "yes"; 2 Bytes)
0x10 0x80 (read-reply: = "yes"; 2 Bytes)
0x0F 0x81 (priority: = "normal"; 2 Bytes)
0x07 0x07 0x80 0x05 0x11 0x22 0x33 0x44 0x55
(Delivery-Time-Tag, Value-Length, Absolute-Token-Tag, Date-Value-Length, Date-Value; 9 Bytes)
0x08 0x06 0x81 0x04 0x55 0x22 0x33 0x44
(Expiry Tag, Value-Length, Relative-Token-Tag, Delta-Second-Value-Length, Delta-Second-Value; 8 Bytes)
J.2 Coding Example for MMS Issuer/User Connectivity Parameters p. 378
0xAB MMS Connectivity Parameters Tag
0x80 MMS Implementation Tag
0x81 MMS Relay/Server Tag
0x82 Interface to Core Network and Bearer Tag
0x83 Gateway Tag
0x81 0x88 (Length = "136") (Length bytes greater than 127 are coded onto 2 bytes according to ISO/IEC 8825-1 [35])
0x80 MMS Implementation Tag
0x01 (Length = "1")
0x01 (MMS implementation information = "WAP"; 1 Byte)
0x81 MMS Relay/Server Tag
0x17 (Length = "23")
0x68 0x74 0x74 0x70 0x3A 0x2F 0x2F 0x6D 0x6D 0x73 0x2D 0x6F 0x70 0x65 0x72 0x61 0x74 0x6F 0x72 0x2E 0x63 0x6F 0x6D
(MMS Relay/Server information = "http://mms-operator.com "; 23 characters; 23 Bytes)
0x82 Interface to Core Network and Bearer Tag
0x32 (Length = "50")
0x10 0xAA (bearer = "GSM-CSD"; 2 Bytes)
0x08 0x2B 0x34 0x39 0x35 0x33 0x34 0x31 0x39 0x30 0x36 0x00
(address = "+495341906", 12 Bytes)
0x09 0x87 (type of address = "E164"; 2 Bytes)
0x25 0xC5 (speed = "autobauding"; 2 Bytes)
0x0A 0x90 (call type = "ANALOG_MODEM"; 2 Bytes)
0x0C 0x9A (authentication type = "PAP"; 2 Bytes)
0x0D 0x64 0x75 0x6D 0x6D 0x79 0x11 0x6E 0x61 0x6D 0x65 0x00
(authentication id = "dummy_name"; 12 Bytes)
0x0E 0x64 0x75 0x6D 0x6D 0x79 0x11 0x70 0x61 0x73 0x73 0x77 0x6F 0x72 0x64 0x00
(authentication pw = "dummy_password"; 16 Bytes)
0x83 Gateway Tag
0x36 (Length = "54")
0x20 0x31 0x37 0x30 0x2E 0x31 0x38 0x37 0x2E 0x35 0x31 0x2E 0x33 0x00
(address = "170.187.51.3"; 14 Bytes)
0x21 0x85 (type of address = "IPv4"; 2 Bytes)
0x23 0x39 0x32 0x30 0x33 0x00 (port = "9203"; 6 Bytes)
0x24 0xCB (service = "CO-WSP"; 2 Bytes)
0x19 0x9C (authentication type = "HTTP BASIC"; 2 Bytes)
0x1A 0x64 0x75 0x6D 0x6D 0x79 0x11 0x6E 0x61 0x6D 0x65 0x00
(authentication id = "dummy_name"; 12 Bytes)
0x1B 0x64 0x75 0x6D 0x6D 0x79 0x11 0x70 0x61 0x73 0x73 0x77 0x6F 0x72 0x64 0x00
(authentication pw = "dummy_password"; 16 Bytes)
K Examples of VService_Id coding |R6| p. 380
This Annex gives examples for the coding of VService_Id,
It is assumed that:
- acknowledgement flag bit is set to 0;
- the call priority bits are set to 0.
| GroupId | Content of EFVBS or EFVGCS | VService_Id(vbs) | VService_Id(vgcs) |
|---|---|---|---|
| 00000000 | F0FFFFFF | 00000000 | 00000010 |
| 00000001 | F1FFFFFF | 00000020 | 00000030 |
| 00000012 | 21FFFFFF | 00000180 | 00000190 |
| 00000123 | 21F3FFFF | 00000F60 | 00000F70 |
| 00001234 | 2143FFFF | 00009A40 | 00009A50 |
| 00012345 | 2143F5FF | 00060720 | 00060730 |
| 00123456 | 214365FF | 003C4800 | 003C4810 |
| 01234567 | 214365F7 | 025AD0E0 | 025AD0F0 |
| 12345678 | 21436587 | 178C29C0 | 178C29D0 |
| 99999999 | 99999999 | BEBC1FE0 | BEBC1FF0 |
| 13452670 | 31546207 | 19A8AFC0 | 19A8AFD0 |