TS 31.102
Characteristics of the
Universal Subscriber Identity Module (USIM)
Application
V18.5.0 (PDF)
2024/06 … p.
V17.13.0
2024/06 … p.
V16.14.0
2024/03 336 p.
V15.12.0
2022/09 327 p.
V14.8.0
2019/06 298 p.
V13.9.1
2017/12 283 p.
V12.13.0
2017/12 264 p.
V11.12.0
2017/12 238 p.
V10.15.0
2017/12 235 p.
V9.19.0
2017/12 223 p.
V8.22.0
2017/12 216 p.
V7.17.0
2012/12 188 p.
V6.23.0
2012/12 181 p.
V5.15.0
2012/09 154 p.
V4.15.0
2005/06 156 p.
V3.18.0
2005/06 141 p.
- Rapporteur:
- Mr. Espi, Sergi
G+D MS
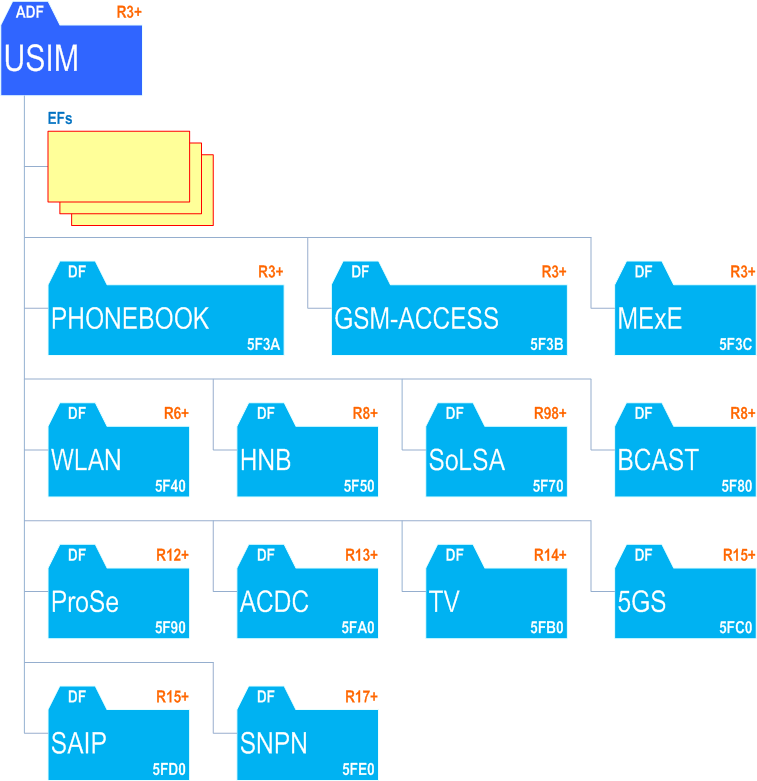
essential Table of Contents for TS 31.102 Word version: 18.4.0
each title, in the "available" or "not available yet" area, links to the equivalent title in the CONTENT