Content for TS 23.222 Word version: 19.3.0
0…
4…
5…
6…
6.3…
6.4…
7…
8…
8.5…
8.8…
8.9…
8.13…
8.17…
8.21…
8.25…
8.26…
8.28…
8.30…
9…
10…
10.4…
10.7…
11…
A
B…
B.2…
B.3…
C…
D…
8.9 Revoking subscription of the CAPIF events
8.9.1 General
8.9.2 Information flows
8.9.2.1 Subscription revoke notification
8.9.2.2 Subscription revoke notification acknowledgement
8.9.3 Procedure
8.10 Authentication between the API invoker and the CAPIF core function
8.10.1 General
8.10.2 Information flows
8.10.3 Procedure
8.11 API invoker obtaining authorization to access service API
8.11.1 General
8.11.2 Information flows
8.11.3 Procedure
8.12 AEF obtaining service API access control policy
8.12.1 General
8.12.2 Information flows
8.12.2.1 Obtain access control policy request
8.12.2.2 Obtain access control policy response
8.12.3 Procedure
...
...
8.9 Revoking subscription of the CAPIF events p. 58
8.9.1 General p. 58
The CAPIF core function allows to revoke subscription of CAPIF events for the subscribing entity related to the service API changes, such as availability events of service APIs, change in service API information, monitoring service API invocations, API invoker onboarding events, etc. This procedure is initiated by the CAPIF core function.
8.9.2 Information flows p. 59
This subclause describes the information flows for CAPIF event subscription revocation.
8.9.2.1 Subscription revoke notification p. 59
Table 8.9.2.1-1 describes the information flow for subscription revoke notification from the CAPIF core function to the subscribing entity.
| Information element | Status | Description |
|---|---|---|
| Identity information | M | The information to determine the identity of the subscribing entity |
| Subscription identifier | M | The unique identifier for the event subscription that was provided to the subscribing entity during the CAPIF event subscription operation. |
| Reason | O | Indicate the reason of subscription revocation |
8.9.2.2 Subscription revoke notification acknowledgement p. 59
Table 8.9.2.2-1 describes the information flow for subscription revoke notification acknowledgement from the subscribing entity to the CAPIF core function.
| Information element | Status | Description |
|---|---|---|
| Acknowledgement | M | The acknowledgement for the received notification. |
8.9.3 Procedure p. 59
Figure 8.9.3-1 illustrates the procedure for subscription revocation, triggered by the CAPIF core function.
Pre-condition:
- The subscribing entity has previously subscribed to CAPIF event(s) to the CAPIF core function.
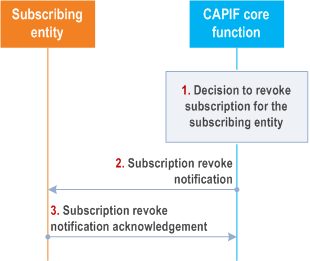
Step 1.
The CAPIF core function decides to revoke subscription of CAPIF event(s) for the subscribing entity.
Step 2.
The CAPIF core function sends subscription revoke notification to the subscribing entity.
Step 3.
The subscribing entity provides a subscription revoke notification acknowledgement to the CAPIF core function.
8.10 Authentication between the API invoker and the CAPIF core function p. 60
8.10.1 General p. 60
The procedure in this subclause corresponds to the architectural requirements for authentication between the API invoker and the CAPIF core function.
8.10.2 Information flows p. 60
8.10.3 Procedure p. 60
Figure 8.10.3-1 illustrates the procedure for authentication between the API invoker and the CAPIF core function.
Pre-condition:
- The API invoker is onboarded with the CAPIF core function and the API invoker profile is created.
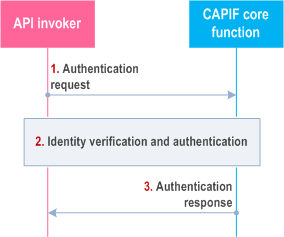
Step 1.
The API invoker triggers authentication to the CAPIF core function, including the identity confirmed after successful onboarding.
Step 2.
Upon receiving the authentication request, the CAPIF core function verifies the identity with the API invoker profile and authenticates the API invoker.
Step 3.
The CAPIF core function returns the result of the API invoker identity verification in the authentication response.
8.11 API invoker obtaining authorization to access service API p. 61
8.11.1 General p. 61
The API invoker requires to execute this procedure when it needs to obtain or re-obtain (e.g. upon expiry of the authorization information) the authorization to access the service API. Once the API invoker receives the authorization to access the service API, the API invoker can perform one or multiple service API invocations as per the permission limit. This procedure may be performed during the API invoker onboarding process.
8.11.2 Information flows p. 61
8.11.3 Procedure p. 61
Figure 8.11.3-1 illustrates the procedure for obtaining authorization to access the service API.
Pre-condition:
- The API invoker is onboarded and has received an API invoker identity.
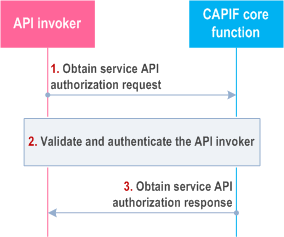
Step 1.
The API invoker sends an obtain service API authorization request to the CAPIF core function for obtaining permission to access the service API by including the API invoker identity information and any information required for authentication of the API invoker. The request may include desired Network Slice Info of the service API.
Step 2.
The CAPIF core function validates the authentication of the API invoker (using authentication information) and checks whether the API invoker is permitted to access the requested service API. The CAPIF core function may additionally verify the Network Slice Info, e.g., check that the desired Network Slice Info by the API invoker is included in the supported Network Slice Info for the indicated service API.
Step 3.
Based on the API invoker's subscription information the authorization information to access the service APIs is sent to the API invoker in the obtain service API authorization response.
8.12 AEF obtaining service API access control policy p. 62
8.12.1 General p. 62
The CAPIF core function is the central repository of all the policies related to service APIs. The AEF executes this procedure when it needs to obtain the policy to perform access control on the service API invocations (e.g. when policy for performing access control on service API is unavailable at the AEF). The AEF can be within PLMN trust domain or within 3rd party trust domain.
8.12.2 Information flows p. 62
8.12.2.1 Obtain access control policy request p. 62
Table 8.12.2.1-1 describes the information flow obtain access control policy request from the AEF to the CAPIF core function.
| Information element | Status | Description |
|---|---|---|
| Identity information | M | Identity information of the entity requesting the access control policy |
| Service API identification | M | The identification information of the service API for which the access control policy is being requested. |
8.12.2.2 Obtain access control policy response p. 62
Table 8.12.2.2-1 describes the information flow obtain access control policy response from the CAPIF core function to the AEF.
| Information element | Status | Description |
|---|---|---|
| Result | M | Indicates the success or failure of the obtain access control policy operation |
| Access control policy information | O
(see NOTE) | The access control policy information corresponding to the requested service API. (See Table E-1). |
|
NOTE:
Shall be present if the Result information element indicates that the obtain access control policy operation is successful. Otherwise access control policy information shall not be present.
|
||
8.12.3 Procedure p. 62
Figure 8.12.3-1 illustrates the procedure for obtaining policy to perform access control on the service API invocations.
Pre-conditions:
- The AEF is hosting the service API but the policy to perform access control is not available with AEF.
- The CAPIF core function is configured with the access control policies corresponding to one or more service APIs.
- Authorization details of the AEF are available with the CAPIF core function.
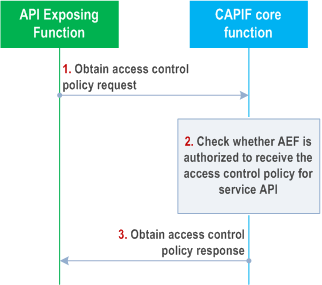
Step 1.
The AEF sends an obtain access control policy request to the CAPIF core function for obtaining the policy to perform the access control on service API invocations by including the details of the hosted service API.
Step 2.
The CAPIF core function checks whether the AEF is authorized to receive the access control policy corresponding to the service APIs requested.
Step 3.
If authorization check is successful, the AEF is provided the access control policy for the service API via an obtain access control policy response. If authorization check is not successful, the AEF is provided with a failure indication via a obtain access control policy response.