Content for TR 33.854 Word version: 17.1.0
6.5 Solution #5: UAV authentication and authorization and pairing authorization using API-based PDU secondary authentication
6.5.1 Solution overview
6.5.2 Solution details
6.5.3 Solution evaluation
...
...
6.5 Solution #5: UAV authentication and authorization and pairing authorization using API-based PDU secondary authentication p. 28
6.5.1 Solution overview p. 28
This solution addresses the following key issues:
- Key Issue#1 "UAS Authentication and Authorization".
- Key Issue#2 "Pairing authorization for UAV and UAVC".
- Key Issue#6 "Security protection of information in remote identification and between UAV/UAVC and UTM/USS".
- Key Issue#7 "Security of command and control (C2) communication".
6.5.2 Solution details p. 29
6.5.2.1 UAV authentication and authorization by USS/UTM p. 29
The procedure for UAV A&A by UTM using API-based PDU secondary authentication is depicted in Figure 6.5.2.1-1. The same procedure may be used with a networked UAV-C.
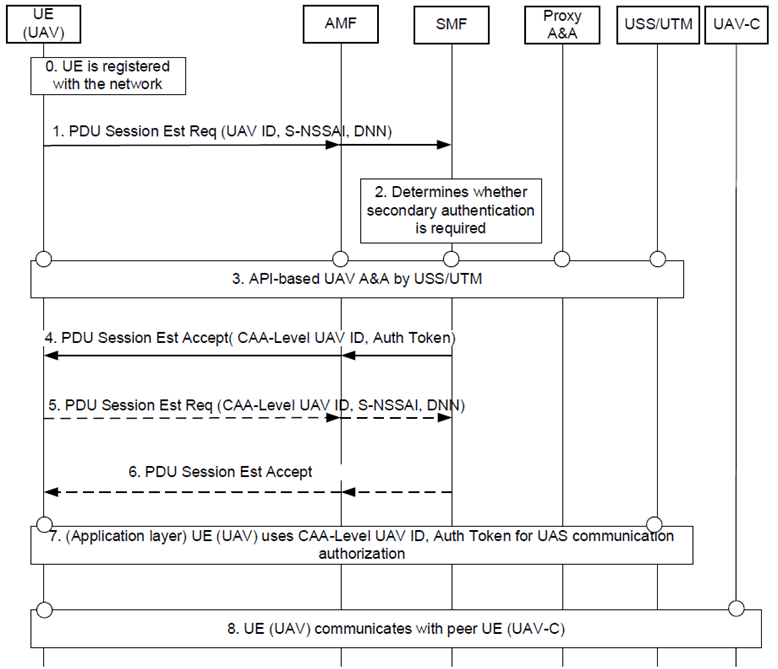
Figure 6.5.2.1-1: Procedure for UAV authentication and authorization with USS/UTM during PDU session establishment (API-based authentication)
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Step 0.
The UE has successfully completed a primary authentication and is registered with the network.
Step 1.
UE sends a PDU session establishment request message that may include the following parameters: a long-term UAV ID (CAA-level UAV ID), a DNN/S-NSSAI for communicating with USS/UTM. The UE may also provide a USS/UTM address. AMF selects SMF based on UE's subscription information and DNN/S-NSSAI values. S-NSSAI/DNN may be specifically used for UAS operations with well-known values or default values configured in the UE by the network. AMF sends corresponding request to SMF.
Step 2.
The SMF determines whether the UE is allowed for UAS operations based on subscription information and local policies.
Step 3.
The SMF triggers an API-based authentication procedure towards the USS/UTM. The SMF communicates with the USS/UTM via a Proxy A&A function (e.g. NEF) that provides an authentication API functionality. SMF or the Proxy A&A is responsible for resolving the address of the USS/UTM based on provided CAA-level UAV ID or USS/UTM address (if provided). The Proxy A&A function may authenticate USS/UTM using provisioned aviation domain certificates. The USS/UTM address may be obtained from a trusted resolution function that resolves the USS/UTM address based on the UE provided CAA Level UAV ID (if USS/UTM address was not provided by UE in step 1). During the procedure, the SMF/Proxy A&A provides the USS/UTM with a 3GPP UAV ID (e.g. GPSI as an External id) and receives from the USS/UTM a new assigned CAA-level UAV ID and authorization token and/or key material upon successful authentication and authorization. Multiple round-trips may be exchanged between the UAV and USS/UTM via SMF/Proxy A&A based on the authentication method supported by USS/UTM. During this procedure, the Proxy A&A obtains information about UAV connectivity (e.g. serving SMF ID, PDU Session ID, UAV IP address) to enable further updates of the PDU session that may be triggered by the USS/UTM (e.g. UAV authorization revocation triggered by USS/UTM as described in clause 6.5.2.2).
Step 4.
Upon successful authorization by USS/UTM, the SMF sends a PDU session establishment accept message that includes the new CAA-level UAV ID and authorization token and/or key material from USS/UTM.
Step 5.
The UE may additionally establish a separate PDU Session dedicated for UAS communications or modify/reuse existing PDU Session used for UAV A&A with USS/UTM. A separate PDU session is necessary if a separate DNN from the one used to communicate with USS/UTM is used for communication with a UAV-C (e.g. while the first PDU session is being used from network Remote ID functionality). The UE provides the CAA-level UAV ID obtained following the successful authorization by USS/UTM. If a UAV-C identity is known to the UAV, it may provide it during the procedure (i.e., PDU Session establishment or modification) to request pairing authorization from USS/UTM. USS/UTM notifies of pairing authorization outcome (e.g. with authorized UAV-C IP address) to the SMF (e.g. via Proxy A&A function/UAS-NF). SMF performs the configuration of the PDU Session accordingly (e.g. ACL for enforcement of pairing with UAV-C authorization).
Step 6.
The UE receives a PDU Session Establishment Accept message authorizing UAS communications. The UE may receive a new CAA-level UAV ID and optionally key material from the USS/UTM as part of a successful pairing authorization. The security parameters above (token and/or key material) when provided by the USS/UTM to the UAV are transported in transparent containers (i.e., not processed by the intermediate entities).
Step 7.
The UE establishes a secure application layer communication with the USS/UTM using the authorization token and/or key material obtained previously to further obtain UAS communication configuration from USS/UTM or perform network Remote ID reporting. The USS/UTM checks the validity of the presented authorization token.
Step 8.
The UE exchanges UAS traffic with peer UAV-C. The UAV and UAV-C may setup a secure connection based on key material received from USS/UTM as described in above steps.
6.5.2.2 UAV authorization revocation p. 30
The procedure for UAV authorization revocation by USS/UTM is depicted in Figure 6.5.2.2-1.
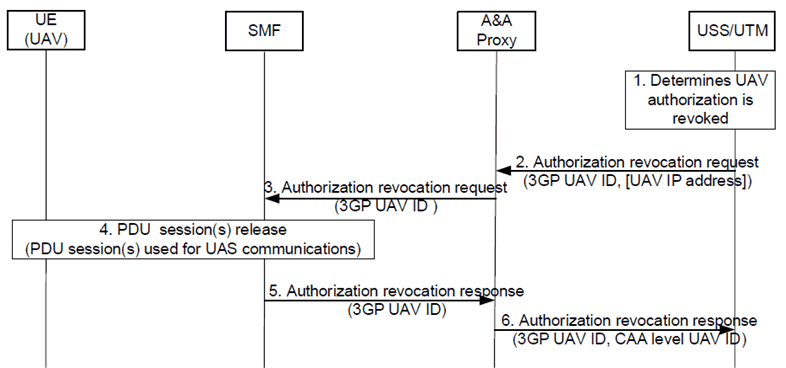
Figure 6.5.2.2-1: Procedure for USS/UTM triggered UAV authorization revocation
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Pre-condition:
UAV has been previously authorized by USS/UTM according to procedure 6.5.2.1.
Step 1.
The USS/UTM determines that the UAV authorization is to be revoked.
Step 2.
The USS/UTM sends an Authorization revocation request to the A&A Proxy providing the 3GPP UAV ID and IP address of the PDU session allocated for the target UAV.
Step 3.
The Proxy A&A determines the SMF serving the UAV based on information maintained from procedure 6.5.2.1 and forwards the request to the SMF.
Step 4.
The SMF initiates a PDU session release procedure for the applicable PDU sessions.
Step 5.
The SMF sends an Authorization revocation response to the A&A Proxy confirming revocation of UAV authorization.
Step 6.
The A&A Proxy forwards the Authorization revocation response to the USS/UTM providing the 3GPP UAV ID and CAA-level UAV ID confirming revocation of authorization for the specified UAV.
6.5.3 Solution evaluation p. 31
This solution is aligned with TR 23.754 conclusions for UUAA and pairing authorization using a PDU Session establishment/modification procedure, including the usage of a generic (API based) procedure via a UAS NF.
This solution fully addresses all requirements of Key Issue #1:
- The solution uses a generic (i.e., API based) procedure for secondary authentication of UAV by USS/UTM during PDU Session establishment (i.e., in addition to primary authentication). The UE provides its CAA-level UAV ID in the PDU Session establishment request to indicate it wants to access UAS services. The SMF triggers UUAA via a Proxy A&A (UAS NF), if the UE has a valid Aerial subscription. The authentication method and authentication messages content used during UUAA are in not in 3GPP scope.
- The solution enables the revocation of UAV authorization by the USS/UTM function via the UAS NF. The revocation may trigger a corresponding PDU Session release.
- Authentication of USS/UTM is handled by the Proxy A&A function by means of provisioned aviation domain certificates. USS/UTM address may be obtained from the UE or from a trusted resolution function which provides a USS/UTM address based on a CAA-level UAV ID.
- The solution enables UAV and UAV-C pairing authorization by USS/UTM. The pairing authorization is requested from USS/UTM during a PDU Session establishment/modification procedure. When pairing authorization is granted by USS/UTM, the SMF configures the PDU Session to allow C2 communication based on UAV-C peer connectivity authorization information provided by USS/UTM.
- Revocation of pairing follows similar principles as for UAV authorization revocation.
- The solution enables the transport of security information (e.g. token, key material) from the USS/UTM to the UE to secure communications between UAV and USS/UTM. The transport of the security information is enabled during a PDU Session establishment procedure (with UUAA). The content of the security information is not in 3GPP scope.
- The solution enables the transport of security information (token, key material) from the USS/UTM to the UE to secure C2 communications with UAV-C or USS/UTM. The transport of the security information is enabled during a PDU Session establishment/modification procedure (with UUAA and/or pairing authorization). The content of the security information is not in 3GPP scope.