Content for TR 33.854 Word version: 17.1.0
5 Key issues
5.1 Key issue #1: UAS authentication and authorization
5.2 Key issue #2: Pairing authorization for UAV and UAVC
5.3 Key Issue #3: TPAE authentication and authorization
5.4 Key issue #4: Location information veracity and location tracking authorization
5.5 Key issue #5: Privacy protection of UAS identities
5.6 Key issue #6: Security protection of information in remote identification and between UAV/UAVC and UTM/USS
5.7 Key issue #7: Security of command and control (C2) communication
...
...
5 Key issues p. 9
5.1 Key issue #1: UAS authentication and authorization p. 9
5.1.1 Key issue details p. 9
Each UAS consists of one UAV Controller (i.e. UAVC) and one UAV.
As stated in Architectural Assumptions of TR 23.754, each UAV is assigned two types of IDs as follows, in addition to UE ID (e.g. SUPI) and Credentials used for registration in 3GPP networks:
- Civil Aviation Authority (CAA) level UAV ID assigned by USS/UTM and used for Remote Identification and Tracking.
- 3GPP UAV ID assigned by the 3GPP system and used by the 3GPP system to identify the UAV.
5.1.2 Threats p. 10
If UAS authentication is not performed, unauthorized UEs/UAVs may access the UAS services provided by 3GPP and consume resources meant for authorized UEs/UAVs. It is notable that the unauthorized UEs may be a regular UE or a UAV with 3GPP ID/credentials. They may be able to access 3GPP networks using 3GPP credentials, but do not have credentials for access UAS services.
If 5GC would not be notified of UAS authentication result, 5GS may allow access UAVs in their system that are not authorized.
If the UAS authentication process is not standardized there may be costly proprietary solutions which may result in potential security risks with respect to proprietary solutions.
If 3GPP system is not capable to receive revocation of UTM/USS authorization, UTM/USS might not be able to take appropriate measures to deal with misbehaving UAVs and they might cause accidents or become attack vectors.
A fake USS/UTM may allow unauthorized UAVs to operate.
5.1.3 Potential security requirements p. 10
A UAV or networked UAVC shall be authenticated and authorized in addition to Primary Authentication before being allowed to access UAS services provided by 3GPP systems.
The 3GPP system shall enable UAV or networked UAVC authentication and authorization by the UTM/USS utilizing the 3GPP system.
The 3GPP system shall enable revocation of UAV or networked UAVC authorization by the UTM/USS utilizing the 3GPP system.
The 3GPP system shall ensure that the USS/UTM is authorized to provide the authorization of the UAV or networked UAVC.
5.2 Key issue #2: Pairing authorization for UAV and UAVC p. 10
5.2.1 Key issue details p. 10
Each UAS consists of one UAV Controller (i.e. UAVC) and one UAV.
It is required in TR 23.754 that
- 3GPP system enables UTM to associate/pair the UAV and UAVC.
- Pairing is authorized by the USS/UTM and the result is made known to the PLMN
- Pairing between UAV and UAVC for the use of their connection may be at least authorized
5.2.2 Threats p. 11
If pairing authorization of UAV and UAVC is not performed securely before establishment of a connection between the UAV and UAVC, an unauthorized UAVC may be able to communicate with the UAV and perform an unauthorized flight which could cause tremendous risks to the security of UAS and public safety.
If 3GPP system is not capable to receive revocation of the connectivity pairing authorization from UTM/USS, then UTM/USS might not be able to take appropriate measures to deal with misbehaving UAVs and they might cause accidents or become attack vectors.
5.2.3 Potential security requirements p. 11
3GPP system shall support enabling authentication and authorization by the USS/UTM of a UAV and UAVC pairing before enabling a data connection between the UAV and UAVC
3GPP system shall provide means for the UTM/USS to revoke a UAV and UAVC pairing authorization in order to close the connection between the UAV and UAVC.
5.3 Key Issue #3: TPAE authentication and authorization p. 11
5.3.1 Key issue details p. 11
TPAE refers to the Third Party Authorized Entity. It has been introduced as part of the Reference Architecture in TR 23.754, as illustrated in the figure below.
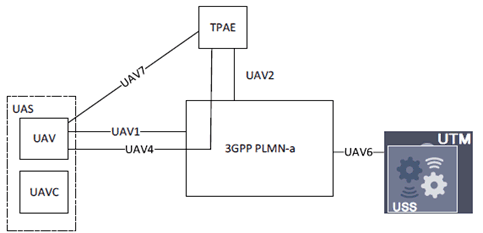
TPAE is one component of the Remote Identification framework, where TPAE can monitor UAVs, access and track UAV data, and make controls to UAVs, overruling UAVC if necessary. TPAE may be treated as a UE, NF, or third party entity, depending on application scenarios. The access based on 3GPP systems and interfaces to the 3GPP systems, e.g. so called UAV2, UAV4, and UAV 7 are being studied in TR 23.754 (UAV2 semantics are outside SA2 study, but UAV identification information is within the scope).
Since TPAE may take control of UAVs and potentially overrules UAVC, it is authenticated and authorized differently from a normal UAVC, UAV, or UE.
5.3.2 Threats p. 11
Without authentication and authorization, potential attackers may hijack a UAV through 3GPP networks.
5.3.3 Potential security requirements p. 11
The TPAE shall be authorized and authenticated by 3GPP systems
The TPAE shall be authorized and authenticated by USS/UTM.
5.4 Key issue #4: Location information veracity and location tracking authorization p. 12
5.4.1 Key issue details p. 12
The UAV can report to USS/UTM various types of location information including absolute positioning, e.g. GNSS coordinates and/or relative positioning, such as Cell, tracking area based coordinates nearby UAVs at the particular time instance. The USS/UTM may make decisions based on the reported location information.
When reporting location information to the USS/UTM via application layer mechanisms such as Networked Remote ID, a UAV may report false location information to the USS/UTM which could results in the UTM/USS making an incorrect decision.
5.4.2 Threats p. 12
The Location Information that is reported by the UAV to the USS/UTM may be spoofed and forged by the following ways:
- Externally, e.g. false location information derived from spoofed GNSS transmitter, spoofed neighbour Cell IDs is reported to the USS/UTM.
- Internally, e.g. a compromised UAV reports forged Location Information regardless of received e.g. GNSS signals or neighbour Cell IDs.
- Hybrid attack, i.e., both, externally and internally.
5.4.3 Potential security requirements p. 12
3GPP system shall provide means to mitigate against UAVs or networked UAV controller location spoofing.
3GPP system shall support to authorize a USS/UTM to request UAV location information.
5.5 Key issue #5: Privacy protection of UAS identities p. 12
5.5.1 Key issue details p. 12
3GPP system will enable UAV and UAV-C to transmit identities and other potentially sensitive information (e.g. UE capability of the UAV controller, position, owner identity, owner address, owner contact details, owner certification, UAV operator identity, UAV operator license, UAV operator certification, UAV pilot identity, UAV pilot license, UAV pilot certification and flight plan). The 3GPP system will enable UAV or UAV controller to preserve the privacy of UAS identities when transmitted over broadcast or towards USS/UTM.
Clause 5.1 of TR 22.125, General has the following requirements:
[R-5.1-002]
Clause 5.2.2 of TS 22.125, Decentralized UAS traffic management, has the following requirement:
The 3GPP system shall be able to provide UTM with the identity/identities of a UAS.
[R-5.1-003]
The 3GPP system shall enable a UAS to send UTM the UAV data which can contain: unique identity (this may be a 3GPP identity), UE capability of the UAV, make & model, serial number, take-off weight, position, owner identity, owner address, owner contact details, owner certification, take-off location, mission type, route data, operating status.
[R-5.1-004]
The 3GPP system shall enable a UAS to send UTM the UAV controller data which can contain: unique identity (this may be a 3GPP identity), UE capability of the UAV controller, position, owner identity, owner address, owner contact details, owner certification, UAV operator identity, UAV operator license, UAV operator certification, UAV pilot identity, UAV pilot license, UAV pilot certification and flight plan.
[R-5.1-007]
Based on regulations and security protection, the 3GPP system shall enable a UAS to send UTM the identifiers which can be: IMEI, MSISDN, or IMSI, or IP address.
[R-5.1-008]
The 3GPP system shall enable a UE in a UAS to send the following identifiers to a UTM: IMEI, MSISDN, or IMSI, or IP address
[R-5.2.2-003]
Clause 5.4 of TS 22.125, Security, has the following requirement:
The 3GPP system shall enable UAV to preserve the privacy of the owner of the UAV, UAV pilot, and the UAV operator in its broadcast of identity information.
[R-5.4-005]
With support of a 3GPP system studied and reported in TR23.754 [3], the following identities are being defined with respect to UAS Remote Identification:
The 3GPP system shall support confidentiality protection of identities related to the UAS and personally identifiable information.
CAA-level UAV ID assigned by USS/UTM and used for Remote Identification and Tracking.
3GPP UAV ID assigned and used by the 3GPP system to identify the UAV
This key issue studies whether security solutions for 3GPP systems are required to protect the CAA-Level UAV ID, 3GPP UAV ID, and/or other information (e.g. locations etc.) for privacy.
5.5.2 Threats p. 13
If an attacker can glean the UAV and UAV-C identities and other information while transmitted, such attacker can maliciously employ the knowledge of UAV and UAV-C identities to mount privacy attacks on UAV and UAV-C (e.g. tracking attack). For example, an attacker may be able to collect and analyse flight information of a particular UAS operations revealing sensitive business practices, such as the flight profile of an individual UAS over time (see FAA's proposed rule on Remote Identification of Unmanned Aircraft Systems [6]).
5.5.3 Potential security requirements p. 13
The 3GPP system shall provide means for mitigating linkability and trackability attacks on UAV and UAV controller identities during communications with USS/UTM.
The 3GPP system shall provide means for mitigating linkability and trackability attacks on UAV and UAV controller identities during C2 communications.
The 3GPP system shall enable UAV and UAV controller to preserve the privacy of UAS owner/operator/pilot, including associated PII.
5.6 Key issue #6: Security protection of information in remote identification and between UAV/UAVC and UTM/USS p. 14
5.6.1 Key issue details p. 14
In TR 23.754, UAV remote identification (Remote ID) procedure is discussed. In this procedure, the UAVs send the messages with flight information (e.g. height, direction, speed, time of flight, etc.) to the receiving party (i.e. UTM/USS, a TPAE or another UAV). The information may be sent in broadcast or unicast. Upon receiving the UAV flight information, a receiving party verifies the validity of the Flight Information and may use such information for e.g. collision avoidance.
Apart from protecting the Remote ID between UAS and UTM/USS, TS 22.125 gives several security-related requirements for protecting other exchanged information between UAS and UTM/USS (e.g. UE capability of the UAV controller, position, owner identity, owner address, owner contact details, owner certification, UAV operator identity, UAV operator license, UAV operator certification, UAV pilot identity, UAV pilot license, UAV pilot certification and flight plan) and user identity. Clause 5.4 of TS 22.125 specifies the security requirement to protect data transport between UAS and UTM (R-5.4-001), and clause 5.1 of TS 22.125 has the requirements (R-5.1-002 to R-5.1-004, R-5.1-007 to R-5.1-008 and R-5.1-017) of UAS identity protection.
To sum up, 3GPP system needs to secure the information exchange (e.g. flight information, user identity, etc) between UAV/UAVC and the receiving party (i.e. UTM/USS, TPAE and other UAV) within the scope of 3GPP, this involves the Remote ID and general information exchanging procedures.
5.6.2 Threats p. 14
If the messages with flight information are modified or replayed by attackers, the received party (i.e. a TPAE or UTM/USS) may be spoofed to believe the UAV appear to perform other than what they actually did. In the worst case, a collision may happen between different UAVs.
If an attacker can glean and modify the UAV and UAV-C identities and other information during its transport from the 3GPP system to the UTM/USS entity, such attacker can maliciously use the knowledge of and the ability to modify UAV and UAV-C identities to mount attacks on UAV and UAV-C identities' confidentiality and integrity (e.g. subscription fraud, impersonation attacks, and hiding problematic/misbehaving UAS).
An attack on integrity or confidentiality of the information exchanged between UAV or UAV-C and USS/UTM may lead to catastrophic loss of overall UAS integrity (e.g. with potential risks to public safety).
5.6.3 Potential security requirements p. 14
The 5G System shall provide the means for the USS/UTM to transport security information to the UE to secure communication between UAV and TPAE/UTM/USS.
5.7 Key issue #7: Security of command and control (C2) communication p. 14
5.7.1 Key issue details p. 14
The TS 22.125 describes about the UAS reference model where an UAS is composed of one UAV controller and one UAV. A UAV can be controlled by a UAV controller connected via the 3GPP mobile network to perform the desired UAV operations through the command and control (C2) signalling which is an application data. Further TR 23.754 clarifies in the architectural assumptions that Connectivity for Command and control of a UAV may be between the UAV and, mutually exclusively, an UAV controller (UAV-C), or a Third Party Authorized Entity (TPAE), or the UAS Service Supplier/UAS Traffic Management (USS/UTM). Therefore, C2 to a UAV may be either over UAV3 or, UAV4 or UAV9 interface. The Command and control traffic exchanged with UAV over various interfaces if not protected (Confidentiality, and integrity) will give way for the attackers to take control of the UAV operations leading to more critical outcomes such as hijacking of UAVs, tracking of UAVs, potential misoperation and accidents. The protection of C2 traffic over the UAV radio link alone may be insufficient since the peer UAV controller may be connected via a different PLMN or a different access technology, using a different security policy for User Plane traffic (e.g. with no integrity and/or no confidentiality protection). In general, the security of the UAV controller connection may be outside the control of the MNO who provides the service to the UAV.
5.7.2 Threats p. 15
The lack of C2 communication security between UAV and other parties such as UAV-C, TPAE and USS/UTM over UAV3, UAV4 and UAV9 may let the attackers to eavesdrop and control the UAV operations thereby leading to UAV hijack and misoperations.
As the UAV controller could be connected via a different PLMN or using a different access technology with a different security policy (e.g. with no integrity and/or no confidentiality protection) the C2 communication security with the UAV may be compromised via the UAV controller connection.
5.7.3 Potential security requirements p. 15
The 3GPP system shall provide means for the USS/UTM to transport security information to the UE to secure C2 Communication as part of the UAS Security.