Content for TR 33.854 Word version: 17.1.0
6.4 Solution #4: UAV authentication and authorization using EAP-based PDU secondary authentication
6.4.1 Solution overview
6.4.2 Solution details
6.4.3 Solution evaluation
...
...
6.4 Solution #4: UAV authentication and authorization using EAP-based PDU secondary authentication p. 26
6.4.1 Solution overview p. 26
This solution addresses Key Issue#1 "UAS Authentication and Authorization".
This solution is applicable to 5GS and EPS for both UAV and networked UAV-C.
This solution enables a secondary authentication with a USS/UTM, reusing existing mechanisms defined for the PDU secondary authentication by an external DN-AAA procedure. An EAP-based secondary authentication is triggered by SMF during a PDU Session establishment procedure based on the UE subscription information and local policies. The authentication and authorization (A&A) by the USS/UTM procedure is performed using non-3GPP credentials (e.g. CAA-level UAV ID, certificate). The SMF acts as the EAP authenticator while the USS/UTM acts as the DN-AAA server. The same procedure can be supported in EPC by UE providing the UAV ID in a PCO and with the PGWc enhanced to support PDU secondary authentication by a DN-AAA feature (as per solutions in TR 23.754).
The USS/UTM may initiate UAV authorization revocation at any time after successful completion of authorization procedure.
6.4.2 Solution details p. 26
6.4.2.1 UAV authentication and authorization by USS/UTM p. 26
The procedure for UAV A&A by USS/UTM based on PDU secondary authentication is depicted in Figure 6.4.2.1-1. The same procedure may be used with a networked UAV-C.
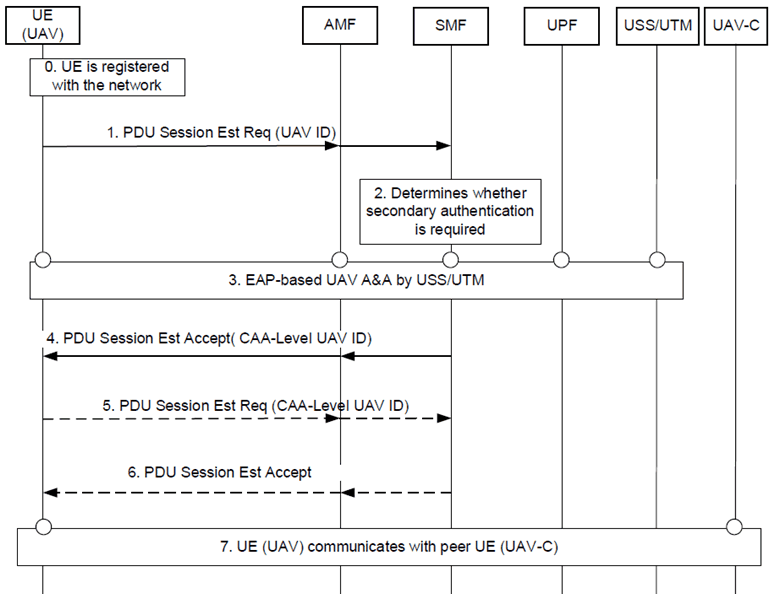
Figure 6.4.2.1-1: Procedure for UAV authentication and authorization with USS/UTM PDU Session establishment
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Step 0.
The UE has successfully completed a primary authentication and is registered with the network.
Step 1.
UE sends a PDU session establishment request message that may include the following parameters: a long-term UAV ID (CAA-level UAV ID) that is communicated to the USS/UTM. The UE may also provide a USS/UTM address. AMF sends corresponding request to SMF.
Step 2.
The SMF determines whether the UE is allowed for UAS operations based on subscription information and local policies.
Step 3.
The SMF triggers an EAP-based authentication procedure towards the USS/UTM. SMF resolves the address of the USS/UTM based on provided CAA-level UAV ID or USS/UTM address (if provided). During the procedure, the SMF provides the USS/UTM with a 3GPP UAV ID (e.g. GPSI as External id) and receives from the USS/UTM a new assigned CAA-level UAV ID (e.g. a temporary Session id) upon successful authentication and authorization.
Step 4.
Upon successful authorization by USS/UTM, the SMF sends a PDU session establishment accept message that includes the new CAA-level UAV ID. The SMF provides the USS/UTM with IP address allocated for the PDU Session as specified for PDU secondary authentication by an external DN-AAA procedure (as per clause 4.3.2.3 of TS 23.502). The SMF maintains the session with the USS/UTM for further updates of the PDU session that may be triggered by the USS/UTM (e.g. UAV authorization revocation triggered by USS/UTM as described in clause 6.3.2.2).
Step 5.
The UE may additionally establish a separate PDU Session dedicated for UAS communications. A separate PDU session is necessary if a separate DNN from the one used to communicate with USS/UTM is used for communication with a UAV-C (e.g. while the first PDU session is being used for network Remote ID and tracking functionality). The UE provides the CAA-level UAV ID obtained from successful authorization by USS/UTM.
Step 6.
The UE receives a PDU Session Establishment Accept message authorizing UAS communications.
Step 7.
The UE exchanges UAS traffic with peer UAV-C.
6.4.2.2 USS/UTM triggered UAV authorization revocation p. 28
Pre-condition:
UAV has been previously authorized by USS/UTM according to procedure 6.4.2.1. The SMF serving the UAV for UAS communications is maintaining a session with the USS/UTM.
The procedure for USS/UTM triggered authorization revocation is similar to authorization revocation by DN-AAA server for a PDU session subject to secondary authentication and authorization by a DN-AAA server.
The USS/UTM may decide to revoke the authorization for a PDU session used for UAS communications. The USS/UTM sends an authorization revocation request message to the SMF providing the 3GPP UAV ID and the IP address of the UE allocated to the PDU session.
The SMF releases the PDU session and sends an authorization revocation response to the USS/UTM message providing the 3GPP UAV ID and CAA level UAV ID for the specified UAV.
6.4.3 Solution evaluation p. 28
This solution has not been evaluated.