Content for TR 33.854 Word version: 17.1.0
6.7 Solution #7: UAS authentication, authorization and security aspects
6.7.1 Solution overview
6.7.2 Solution details
6.7.3 Solution evaluation
...
...
6.7 Solution #7: UAS authentication, authorization and security aspects p. 33
6.7.1 Solution overview p. 33
The solution address key issue #1 and #6.
This solution assumes the following based on clause 4.2 of TR 23.754, Architecture assumptions:
- A UAV is assigned, a CAA-level UAV Identity by functions in the aviation domain (e.g. USS) or by functions in the USS/UTM.
- The 3GPP CN is aware of the CAA-level UAV Identity. A mapping is possible in the mobile operator network and in the UAS application layer outside of 3GPP between the 3GPP UAV ID and the CAA-level UAV ID.
- Enables USS/UTM to authenticate and authorize the UAV(s) to access and use the USS/UTM services securely.
6.7.2 Solution details p. 34
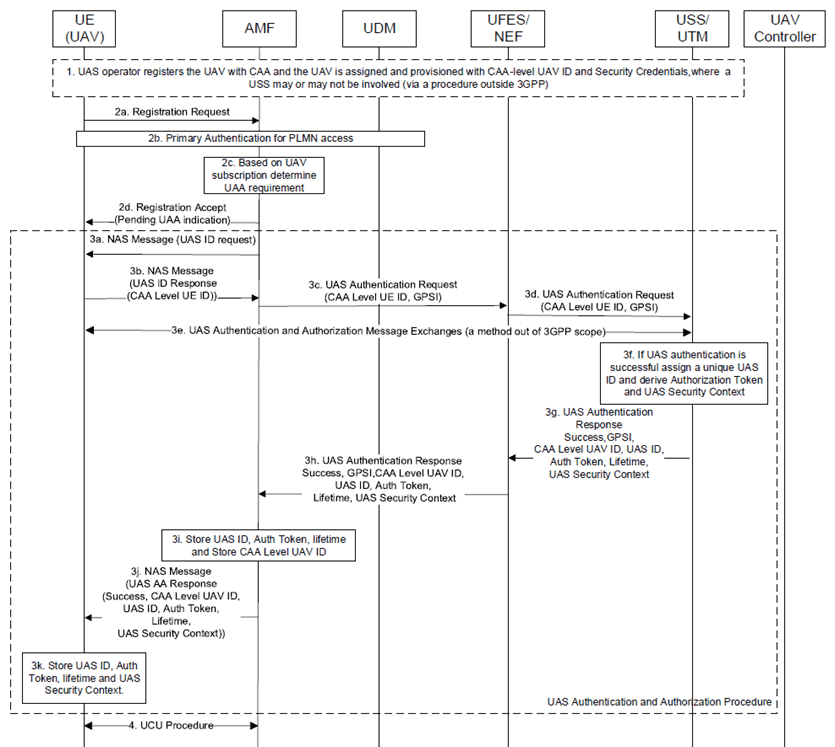
Figure 6.7.2-1: UAS authentication and authorization (UAA) procedure
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Step 1.
UAS Authentication and Authorization (UAA) Revocation:
As a precondition the UAV is registered with the USS/UTM by the UAS operator using any method outside the 3GPP scope. During this registration, the UAV is configured with the CAA-level UAV ID, the USS routing information (which may also be part of CAA-level UAV ID), and the required long-term credentials to enable UAS security. These are the credentials that are provisioned into the UAV to form the root of the UAS security. The credentials may include symmetric key(s) or public/private key pair (example. with certificates) depending on the implementation which is out of 3GPP scope.
Step 2a-b.
The UAV sends registration request to AMF and a primary authentication is performed as specified in TS 33.501.
Step 2c.
After a successful primary authentication, the AMF based on the UE (UAV) subscription information fetched from the UDM/UDR determines to trigger UAS authentication and authorization (UAA).
Step 2d.
AMF sends to UE (UAV) an UAS authentication Required Indicator or a pending UAA indication in the Registration Accept message.
Step 3a.
AMF may optionally send an UAS ID request to the UAV over the NAS transport.
Step 3b.
The UAV responds to AMF with a UAS ID response containing CAA-level UAV ID and optionally USS routing information (if routing information is not part of CAA-level UAV ID).
Step 3c.
Based on the USS routing Information, the AMF sends a UAS Authentication request message (i.e., over a service-based interface) to the UFES. The GPSI can be used for external identification of UAV. The routing to a UFES and USS/UTM and external ID usage need to be aligned with SA2 agreements during the normative work.
Step 3d.
The UFES forwards the received UAS authentication request message to the appropriate USS/UTM.
Step 3e.
The USS/UTM performs authentication method specific message exchange with the UAV to enable mutual authentication. The authentication method used for UAA is up to USS/UTM and it is out of 3GPP scope.
Step 3f.
The USS/UTM on performing a successful UAS authentication, verifies the preconfigured CAA Level UAV ID based on the stored UAV subscription, if required assign a new CAA Level UAV ID to the UAV. Further the USS/UTM assigns a UAS ID to uniquely identify the UAS formed by the UAV and associated UAV-C information based on UAS subscription. The method of UAS-ID assignment is out of 3GPP scope. Further the USS/UTM sgenerate a UAS root security context (based on a method out of 3GPP scope) from the long-term credential available as part of UAS subscription information in the USS/UTM to enable UAS security and an UAS root security identifier (e.g. bound to the security context) is generated to uniquely identify the UAS root security context in the USS/UTM. To enable authorization of UAV for various UAS service following a UAS registration (example., flight authorization request, PDU session establishment for C2 and Pairing of UAV with UAV-C etc.), the USS/UTM generates an Authorization Token (Auth Token) (e.g. it can be bound to the UAS ID, UAV-CAA-Level ID, optional UAV-C ID). The USS/UTM also assigns a lifetime (a validity period or time duration) for the authorization token for it to be used by the 3GPP network to authorize the UAV for various subsequent UAS services. The USS/UTM after successful UAS authentication, locally stores the External ID of UAV (i.e., GPSI), CAA-level UAV ID, authentication status information, UAS ID, Auth Token, lifetime along with UAS Security Context and its identifier. The UAS root security context (e.g. a key) and its corresponding identifier forms the UAS security context. Optionally, if the UAV has no preconfigured UAV-C ID, the USS/UTM may also provide the UAV-C ID for the UAV along with the UAV authentication response.
Step 3g.
In response to the successful UAS authentication, the USS/UTM sends the UAS authentication response message to the UFES. The UAS authentication response message includes an authentication result with Success Indication, GPSI, CAA Level UAV ID, UAS ID, UAS security context, Auth Token and lifetime.
Step 3h.
The UFES receives the UAS authentication response message containing Success Indication, GPSI, CAA Level UAV ID, UAS ID, UAS security context, Auth Token and lifetime as part of the UAS information for the UAV. The UFES stores the received UAS information for the UAV and the parameters exactly stored at UFES will be defined during the normative phase. Further, the UFES forwards the received UAS authentication response message to the AMF.
Step 3i.
The AMF receives the UAS authentication response message and locally stores the received authentication result with Success Indication, CAA Level UAV ID, UAS ID, Auth Token and lifetime as part of the UAS information for the UAV to enable subsequent UAS service authorization at the 3GPP network.
Step 3j.
The AMF forwards the received UAS authentication response message to the UAV.
Step 3k.
The UAV receives the UAV authentication response message and on receiving a 'Success Indication', the UAV generates the UAS Security context (UAS root security context and identifier) similar to the USS/UTM from the long-term credential preconfigured in the UAV. If the locally generated UAS security context and received UAS security context matches, then the UAV considers the UAS authentication as successful and locally stores the received CAA Level UAV ID, UAS ID, Auth Token, lifetime, UAS root security context and its identifier along with the most recently derived KUAS as part of UAS Security Context. The UAV uses the UAS root security context identifier to uniquely identify the UAS root security context. The UAS root security context can be used by the UAV and USS/UTM to set up secure connection.
Step 4.
The AMF may trigger UE parameter update procedure as specified in TR 23.754.
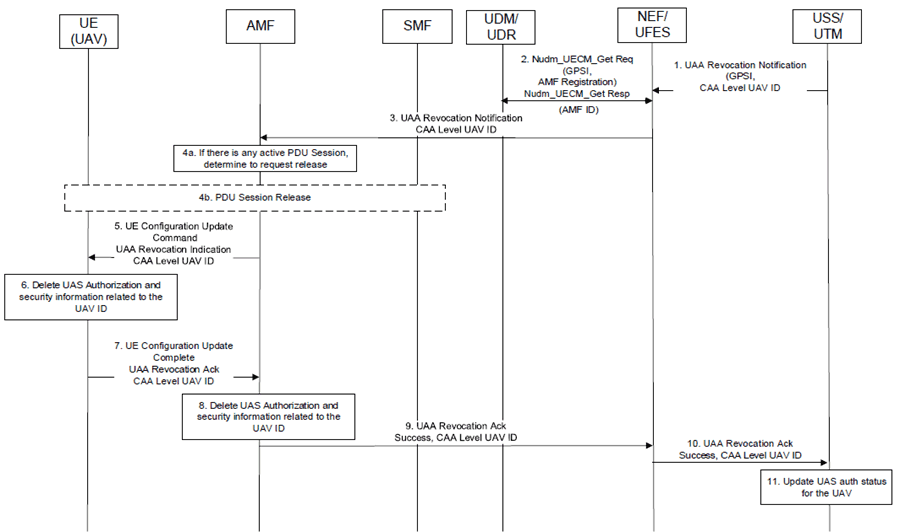
Figure 6.7.2-2: UAS authentication and authorization (UAA) Revocation procedure
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Step 1.
Applicability to EPS:
The UAS Authentication and Authorization procedure and revocation procedure described in this section can be applicable to EPS, with the adaptation of MME, SMF+PGW-C, UPF+PGW-U and HSS+UDM respectively as described in the steps below. UFES can act as a UAS NF or UAS control function in the 3GPP network which can be a standalone network function, or a service offered by the SCEF in the EPS instead of NEF in the 5GS. For the UAA revocation procedure, the MME, S-GW+PGW-C and HSS will be involved in EPS. The message name used in EPS procedure can be aligned with SA2 where required during the normative work. The steps related to UAA for an UAV in EPS scenario is described as follows:
The USS/UTM determines to revoke UAS authentication and authorization corresponding to an UAV identified with CAA Level UAV-ID and sends an UAA Revocation Notification with GPSI and CAA Level UAV ID to the corresponding UFES using a service operation message.
Step 2.
The UFES fetches the serving AMF ID corresponding to the GPSI of the UAV from the UDM by invoking Nudm_UECM_Get Request/Response message based on clause 5.2.3.2.4 of TS 23.502.
Step 3.
The UFES sends the received UAA Revocation Notification message to the AMF with the CAA level UAV ID.
Step 4a-b.
The AMF on receiving the UAA Revocation Notification, if there is any related active PDU session corresponding to the UAV, initiates a PDU Session release based on clause 4.3.4 of TS 23.502.
Step 5.
The AMF further enables the UAA revocation with the UE using the UE Configuration update procedure. The AMF sends CAA Level UAV ID along with the UAA Revocation indication to the UAV in the UE Configuration update command.
Step 6.
The UAV on receiving the UAA Revocation indication, deletes all the UAS authorization and security information locally stored corresponding to its CAA Level UAV ID.
Step 7.
The UAV further sends to AMF, a UE Configuration update complete message with a UAA Revocation acknowledgement along with the CAA Level UAV ID.
Step 8.
The AMF on receiving the UAA Revocation acknowledgement and CAA Level UAV ID, deletes locally stored UAS authorization and security information corresponding to the UAV ID.
Step 9a.
The AMF further sends an UAA Revocation acknowledgement message with Success Indication, GPSI and CAA Level UAV ID to the UFES.
Step 9b.
The UFES removes UAV related information (if any) locally stored related to the UAV.
Step 10.
The UFES further sends the received UAA Revocation acknowledgement message with the received Success Indication, GPSI and CAA Level UAV ID to the USS/UTM.
Step 11.
The USS/UTM on receiving the UAA Revocation acknowledgement message with Success Indication, GPSI and CAA Level UAV ID, updates the UAS authentication status and related information locally stored for the UAV.
Step 1.
The UAA revocation in EPS for any UAV can be performed as follows:
The precondition is applicable as described for 5GS case.
Step 2.
The UAV sends Attach request to MME and an authentication and key agreement is performed. The UAV can send a CAA level UAV ID with USS Routing information, Flight path data and target UAV-C information if any during the attach request or after authentication in a NAS message.
Step 3.
The MME, based on the subscription information, selects the Default APN for connectivity with the USS/UTM based on 23.754 [3]. The MME can send to SMF+PGW-C via SGW, a create session request which contains the CAA level UAV ID and flight path data and target UAV-C information if any and 3GPP UAV ID (i.e., an external identifier). The MME receives a create session response form SMG+PGW-C and an attach accept is provided to the UAV.
Step 4.
The SMF+PGW-C sends a UAV authentication request to the UFES (or a UAS NF as mentioned in 23.754 [3]) with CAA level UAV ID and flight path data and target UAV-C information if any and 3GPP UAV ID.
Step 5.
The UFES forwards the received UAS authentication request message to the appropriate USS/UTM.
Step 6.
The USS/UTM performs authentication method specific message exchange with the UAV to enable mutual authentication. The authentication method used for UAA is up to USS/UTM and it is out of 3GPP scope. Then Step 3f and 3g (Figure 6.7.2-1) is similar as described for 5GS.
Step 7.
In response to the successful UAS authentication, the USS/UTM sends the UAS authentication response message to the UFES. The UAS authentication response message includes an authentication result with Success Indication, 3GPP UAV ID, CAA Level UAV ID, UAS ID, UAS security context, Auth Token and lifetime.
Step 8.
The UFES receives the UAS authentication response message and may store any received UAS information for the UAV. Further, the UFES forwards the received UAS authentication response message to the SMF+PGW-C.
Step 9.
The SMF+PGW-C sends update bearer request with the information received in UAS authentication response message to the MME.
Step 10.
The MME forwards the received UAS authentication response message to the UAV in a NAS message. The UAV receives the UAV authentication response message and then the process in UAV is same as described in step 3k (Figure 6.7.2-1) for 5GS and sends a response to MME.
Step 11.
The MME further confirms to SMF+PGW-C with update bearer response. The MME/SMF+PGW-C locally stores the received authentication result with Success Indication, CAA Level UAV ID, UAS ID, Auth Token and lifetime as part of the UAS information for the UAV to enable subsequent UAS service authorization at the 3GPP network. The SMF+PGW-C can set the traffic filters to allow traffic between UAV and USS/UTM based on the authentication result
Step 1.
The USS/UTM determines to revoke UAS authentication and authorization corresponding to an UAV identified with CAA Level UAV-ID and sends an UAA Revocation Notification with 3GPP UAV ID (i.e., external identifier) and CAA Level UAV ID to the corresponding UFES.
Step 2.
The UFES sends the received UAA Revocation Notification message to the SMF+PGW-C (the serving PGW can be identified based on TR 23.754).
Step 3.
The SMF+PGW-C on receiving the UAA Revocation Notification, initiates a PDN connection release and during the PDN connection release procedure, it provides to UAV via the SGW and MME, the CAA level UAV ID and UAA Revocation indication based on the received UAA Revocation Notification message.
Step 4.
The UAV on receiving the UAA Revocation indication, can delete all the UAS authorization and security information locally stored corresponding to its CAA Level UAV ID.
Step 5.
The UAV further responds to MME, with a UAA Revocation acknowledgement along with the CAA Level UAV ID.
Step 6.
The MME sends the received UAA Revocation acknowledgement and CAA Level UAV ID, to SMF+PGW-C, which can delete the locally stored UAV information.
Step 7.
The SMF+PGW-C send the UAA Revocation acknowledgement along with the CAA Level UAV ID to the UFES.
Step 8.
The UFES removes UAV related information (if any) locally stored related to the UAV. The UFES further sends the received UAA Revocation acknowledgement message with the received Success Indication, GPSI and CAA Level UAV ID to the USS/UTM.
Step 9.
The USS/UTM on receiving the UAA Revocation acknowledgement message with Success Indication, GPSI and CAA Level UAV ID, updates the UAS authentication status and related information locally stored for the UAV.
6.7.3 Solution evaluation p. 38
The solution allows USS/UTM (post successful UAA) to send the UAS security context (a security information and identifier), UAS ID, Auth Token and lifetime to the UAV. Following a successful UAA, the solution requires generation of authorization information (i.e., Auth Token) by USS/UTM to allow authorization information to be provided to the UAV to enable further UAS service authorization. The UAS security context can be used to set up secure connection between UAV and USS/UTM. As TR 23.754 allows sending new CAA level UAV ID to UAV, a dedicated identifier is most crucial to be provided by the USS/UTM to identify the security context provided to the UAV. The Auth Token can be used to enable authorization of UAV for subsequent UAS service. The UAS ID can allow identification of an UAS formed by the UAV, USS/UTM and UAV-C as applicable (UAS ID generation is up to USS/UTM and it is outside the scope of 3GPP).
AMF in 5GS and SMF+PGW-C in EPS: On a successful UAA, store information such as authentication result (i.e., success) along with information received in UAS authentication response (i.e., CAA level UAV ID, UAS ID, Auth Token and lifetime. Optionally UAVC ID if received), which can enable subsequent UAS service authorization.
On a UAA Revocation Notified by USS/UTM, release PDU session/PDN Connection by indicating UAA Revocation Indication and CAA Level UAV ID to UAV. Delete any UAV related information locally stored related to CAA level UAV ID.
UE: On a successful UAA, store information such as authentication result (i.e., success) along with information received in UAS authentication response (i.e., CAA level UAV ID, UAS Security Context, UAS ID, Auth Token and lifetime. Optionally UAVC ID if received), which can enable subsequent UAS service authorization and security set up.
On receiving UAA Revocation Indication and CAA Level UAV ID, delete all information related to UAA such as UAS Security Context, UAS ID, Auth Token, lifetime, and any CAA level UAV ID (if meant for temporary use).
Credentials used by UAV and UTM/USS are out of 3GPP scope.