Content for TS 33.503 Word version: 17.2.0
6.3.3.3 Security procedure over Control Plane
6.3.3.3.1 General
6.3.3.3.2 PC5 security establishment for 5G ProSe UE-to-Network relay communication over Control Plane
6.3.3.3.3 PC5 Key Hierarchy over Control Plane
6.3.3.4 Security for 5G ProSe Communication via Layer-3 UE-to-Network Relay with N3IWF support
...
...
6.3.3.3 Security procedure over Control Plane p. 33
6.3.3.3.1 General p. 33
This clause describes the security mechanisms for the 5G ProSe Layer-3 UE-to-Network Relay authentication, authorization and key management using the 5G ProSe Remote UE specific authentication for PC5 keys establishment. EAP-AKA', as specified in RFC 9048 shall be used for 5G ProSe Remote UE authentication. The EAP-AKA' implementations shall comply with the EAP-AKA' profile specified in Annex F of TS 33.501. Network entities AMF, AUSF and UDM are involved for key derivation and distribution of keys used for 5G ProSe UE-to-Network Relay communication. The UE shall be provisioned with necessary policies and parameters to use 5G ProSe services, as part of the UE ProSe Policy information as defined in clause 4.2.2 of TS 23.503. PCF shall provision the authorization policy and parameters for 5G ProSe UE-to-Network Relay discovery and communication as specified in clause 5.1.4 of TS 23.304.
6.3.3.3.2 PC5 security establishment for 5G ProSe UE-to-Network relay communication over Control Plane p. 34
This clause describes the procedure for establishing a PC5 link between the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay. The procedure includes how the 5G ProSe Remote UE is authenticated by the AUSF of the 5G ProSe Remote UE via the 5G ProSe UE-to-Network Relay and the AMF of the 5G ProSe UE-to-Network Relay during 5G ProSe PC5 establishment. This mechanism can be used when the 5G ProSe Remote UE is out of coverage.
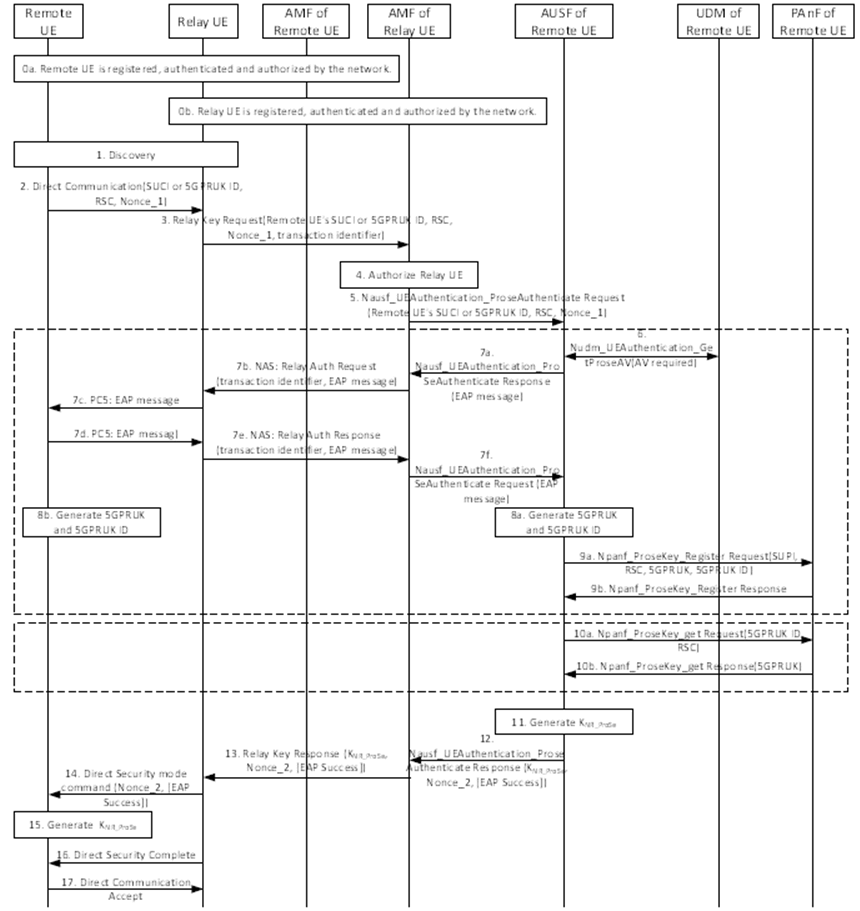
Figure 6.3.3.3.2-1: PC5 security establishment procedure for 5G ProSe UE-to-Network relay communication over Control Plane
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
Step 0.
Further communication between the 5G ProSe Remote UE and the Network takes place securely via the 5G ProSe UE-to-Network Relay.
When the 5G ProSe Layer-3 UE-to-Network Relay sends a Remote UE Report to the SMF as specified in TS 23.304, the 5G ProSe Layer-3 UE-to-Network Relay shall include Remote User ID (i.e. the CP-PRUK ID received in step 13) in the message .
If the 5G ProSe Remote UE receives from the 5G ProSe UE-to-Network Relay a Direct Connection Reject due to CP-PRUK ID not found in the network, the 5G ProSe Remote UE shall not attempt to reconnect with the 5G ProSe UE-to-Network Relay using the CP-PRUK ID. The 5G ProSe Remote UE may attempt to connect with the 5G ProSe UE-to-Network Relay using its SUCI.
The 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay shall be registered with the network. The 5G ProSe UE-to-Network Relay shall be authenticated and authorized by the network to provide UE-to-Network Relay service. The 5G ProSe Remote UE shall be authenticated and authorized by the network to receive UE-to-Network Relay service. PC5 security policies are provisioned to the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay respectively during this authorization and information provisioning procedure.
Step 1.
The 5G ProSe Remote UE or Relay UE shall initiate discovery procedure using any of Model A or Model B method as specified in clause 6.3.1.2 or 6.3.1.3 of TS 23.304 respectively.
Step 2.
After the discovery of the 5G ProSe UE-to-Network Relay, the 5G ProSe Remote UE shall send a Direct Communication Request to the 5G ProSe UE-to-Network Relay for establishing secure PC5 unicast link. The 5G ProSe Remote UE shall include its security capabilities and PC5 signalling security policy in the DCR message as specified in TS 33.536. The message shall also include Relay Service Code, Nonce_1.
If the 5G ProSe Remote UE does not have a valid 5G Prose Remote User Key (CP-PRUK), the 5G ProSe Remote UE shall include SUCI in the DCR to trigger 5G ProSe Remote UE specific authentication and establish a CP-PRUK.
If the 5G ProSe Remote UE already has a valid CP-PRUK for Relay Service Code, the 5G ProSe Remote UE shall include associated the CP-PRUK ID in the DCR to indicate that the 5G ProSe Remote UE wants to get relay connectivity using the CP-PRUK. The privacy and integrity protection of DCR are described in clause 6.3.5
Step 3.
Upon receiving the DCR message, the 5G ProSe UE-to-Network Relay shall send the Relay Key Request to the AMF of the 5G ProSe UE-to-Network Relay, including SUCI or CP-PRUK ID, RSC and Nonce_1 received in the DCR message. The 5G ProSe UE-to-Network Relay shall also include in the message a transaction identifier that identifies the 5G ProSe Remote UE for the subsequent messages over 5G ProSe UE-to-Network Relay's NAS messages.
Step 4.
The AMF of the 5G ProSe UE-to-Network Relay shall verify with the UDM whether the 5G ProSe UE-to-Network Relay is authorized to provide the UE-to-Network Relay service.
Step 5.
The AMF of the 5G ProSe UE-to-Network Relay shall select an AUSF based on SUCI or CP-PRUK ID and forward the parameters received in Relay Key Request to the AUSF in Nausf_UEAuthentication_ProseAuthenticate Request message. The Nausf_UEAuthentication_ProseAuthenticate Request message shall contain the 5G ProSe Remote UE's SUCI or CP-PRUK ID, Relay Service Code, Nonce_1. If CP-PRUK ID is received from AMF of the 5G ProSe UE-to-Network Relay, the AUSF of the 5G ProSe Remote temporarily stores Nonce_1 and UE skips steps 6-9. If the 5G ProSe Remote UE's SUCI is received from AMF of the 5G ProSe UE-to-Network Relay, the AUSF of the 5G ProSe Remote UE temporarily stores Nonce_1 and Relay Service Code and skips step 10.
Step 6.
The AUSF shall initiate a 5G ProSe Remote UE specific authentication using the ProSe specific parameters received (i.e. RSC, etc.). The serving network name handling is the same as defined in TS 33.501.
The AUSF of the 5G ProSe Remote UE shall retrieve the Authentication Vectors and the Routing Indicator of the 5G ProSe Remote UE from the UDM via Nudm_UEAuthentication_GetProseAv Request message. Upon reception of the Nudm_UEAuthentication_GetProSeAv Request, the UDM shall invoke SIDF de-conceal SUCI to gain SUPI before UDM can process the request. The UDM checks whether the UE is authorized to use a ProSe UE-to-Network Relay service based on authorization information in UE's Subscription data. If the UE is authorized, the UDM shall choose the EAP-AKA' authentication method based on the received Nudm_UEAuthentication_GetProseAv Request.
Step 7a.
The AUSF shall temporarily store XRES, Routing indicator and SUPI. The AUSF of the 5G ProSe Remote UE shall trigger authentication of the 5G ProSe Remote UE based on EAP-AKA'. The AUSF of the 5G ProSe Remote UE generates the EAP-Request/AKA'-Challenge message defined in clause 6.1.3.1 of TS 33.501 and send EAP-Request/AKA'-Challenge message to the AMF of the 5G ProSe UE-to-Network Relay in a Nausf_UEAuthentication_ProSeAuthenticate Response message.
Step 7b.
The AMF of the 5G ProSe UE-to-Network Relay shall forward the Relay Authentication Request (including the EAP-Request/AKA'-Challenge) to the 5G ProSe UE-to-Network Relay over NAS message, including transaction identifier of the 5G ProSe Remote UE in the message. The NAS message is protected using the NAS security context created for the 5G ProSe UE-to-Network Relay.
Step 7c.
Based on the transaction identifier, the 5G ProSe UE-to-Network Relay shall forwards the EAP-Request/AKA'-Challenge to the 5G ProSe Remote UE over PC5 messages.
The USIM in the 5G ProSe Remote UE verifies the freshness of the received values by checking whether AUTN can be accepted as described in TS 33.102.
For EAP-AKA', the USIM computes a response RES. The USIM shall return RES, CK, IK to the ME. The ME shall derive CK' and IK' according to clause A.3 in TS 33.501.
Step 7d.
The 5G ProSe Remote UE shall return EAP-Response/AKA'-Challenge to the 5G ProSe UE-to-Network Relay over PC5 messages.
Step 7e.
The 5G ProSe UE-to-Network Relay forwards the EAP-Response/AKA'-Challenge together with the transaction identifier of the 5G ProSe Remote UE to the AMF of the 5G ProSe UE-to-Network Relay in a NAS message Relay Authentication Response.
Step 7f.
The AMF of the 5G ProSe UE-to-Network Relay forwards EAP-Response/AKA'-Challenge to the AUSF of the 5G ProSe Remote UE via Nausf_UEAuthentication_ProSeAuthenticate Request.
The AUSF of the 5G ProSe Remote UE performs the UE authentication by verifying the received information as described in TS 33.501.
For EAP-AKA', the AUSF of the 5G ProSe Remote UE and the 5G ProSe Remote UE may exchange EAP-Request/AKA'-Notification and EAP-Response /AKA'-Notification messages via the AMF of the 5G ProSe UE-to-Network Relay and the 5G ProSe UE-to-Network Relay. After the exchanges, the AUSF of the 5G ProSe Remote UE and the 5G ProSe Remote UE shall derive the KAUSF_P in the same way as KAUSF is derived in TS 33.501.
Step 8.
On successful authentication, the AUSF of the 5G ProSe Remote UE and the 5G ProSe Remote UE shall generate CP-PRUK as specified in clause A.2 and CP-PRUK ID.
The CP-PRUK ID is in NAI format as specified in Section 2.2 of RFC 7542, i.e. username@realm. The username part includes the Routing Indicator from step 6 and the CP-PRUK ID*, and the realm part includes Home Network Identifier. The CP-PRUK ID* is specified in clause A.3.
Step 9a.
The AUSF of the 5G ProSe Remote UE shall select the PAnF (Prose Anchor Function) based on CP-PRUK ID and send the SUPI, RSC, CP-PRUK and CP-PRUK ID in Npanf_ProseKey_Register Request message to the PAnF.
Step 9b.
The PAnF shall store the Prose context info (i.e. SUPI, RSC, CP-PRUK, CP-PRUK ID) for the 5G ProSe Remote UE and send Npanf_ProseKey_Register Response message to the AUSF.
Step 10a.
The AUSF of the 5G ProSe Remote UE shall select the PAnF based on CP-PRUK ID and send received CP-PRUK ID and RSC in Npanf_ProseKey_get Request message.
Step 10b.
The PAnF retrieves CP-PRUK based on the CP-PRUK ID and checks whether the 5G ProSe Remote UE is authorized to use the UE-to-Network Relay service based on received RSC, i.e. the PAnF uses Nudm_SDM operation defined in TS 23.502 to check with the UDM whether the Remote UE is authorized to use ProSe UE-to-Network Relay service by using the SUPI. If the 5G ProSe Remote UE is authorized and the retrieved CP-PRUK is valid, the PAnF sends Npanf_ProseKey_get Response message with CP-PRUK to the AUSF.
If the CP-PRUK is stale, the PAnF treats it as invalid based on local policy. When receiving a Npanf_ProseKey_get request in such case, the PAnF responses with CP-PRUK not found.
Step 11.
The AUSF of the 5G ProSe Remote UE shall generate Nonce_2 and derive the KNR_ProSe key using CP-PRUK, Nonce_1 and Nonce_2 as defined in clause A.4.
Step 12.
The AUSF of the 5G ProSe Remote UE shall send the KNR_ProSe, Nonce_2 in Nausf_UEAuthentication_ProseAuthenticate Response message to the 5G ProSe UE-to-Network Relay via the AMF of the 5G ProSe UE-to-Network Relay. EAP Success message shall be included if step 7 is performed successfully. The AUSF of the 5G ProSe Remote UE shall also include the CP-PRUK ID in the message.
Step 13.
When receiving a KNR_ProSe from the AUSF of the 5G ProSe Remote UE via the AMF of the 5G ProSe UE-to-Network Relay, the 5G ProSe UE-to-Network Relay derives PC5 session key Krelay-sess and confidentiality key Krelay-enc (if applicable) and integrity key Krelay-int from KNR_ProSe, as defined in clause 6.3.3.3.3 of the present document. KNR_ProSe ID and Krelay-sess ID are established in the same way as KNRP ID and KNRP-sess ID in TS 33.536. The CP-PRUK ID is sent from the AMF of the 5G ProSe UE to-Network Relay to UE-to-Network Relay. The EAP Success message is also sent from the AMF of the 5G ProSe UE-to-Network Relay to UE-to-Network Relay if received from AUSF.
Step 14.
The 5G ProSe UE-to-Network Relay shall send the received Nonce_2 and 5G ProSe Remote UE's PC5 signalling security policy to the 5G ProSe Remote UE in Direct Security mode command message, which is integrity protected using Krelay-int. EAP Success message shall be included if received from the AMF of the 5G ProSe UE-to-Network Relay.
Step 15.
The 5G ProSe Remote UE shall generate the KNR_ProSe key to be used for remote access via the 5G ProSe UE-to-Network Relay in the same way as defined in step 11. The 5G ProSe Remote UE shall derive PC5 session key Krelay-sess and confidentiality and integrity keys from KNR_ProSe in the same way as defined in step 13.
The 5G ProSe Remote UE shall verify the Direct Security Mode Command message. Successful verification of the Direct Security Mode Command message assures the 5G ProSe Remote UE that the 5G ProSe UE-to-Network Relay is authorized to provide the relay service.
Step 16.
The 5G ProSe Remote UE shall send the Direct Security Mode Complete message containing its PC5 user plane security policies to the 5G ProSe UE-to-Network relay, which is protected by Krelay-int or/and Krelay-enc derived from Krelay-sess according to the negotiated PC5 signalling policies between the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay.
Step 17.
On receiving the Direct Security Mode Complete message, the 5G ProSe UE-to-Network Relay shall verify the Direct Security Mode Complete message. Successful verification of the Direct Security Mode Complete message assures the 5G ProSe UE-to-Network Relay that the 5G ProSe Remote UE is authorized to get the relay service.
After the successful verification of the Direct Security Mode complete message, the 5G ProSe UE-to-Network Relay responds a Direct Communication Accept message to the 5G ProSe Remote UE to finish the PC5 connection establishment procedures and store the CP-PRUK ID in the security context associated to the PC5 link with the 5G ProSe Remote UE.
6.3.3.3.3 PC5 Key Hierarchy over Control Plane p. 38
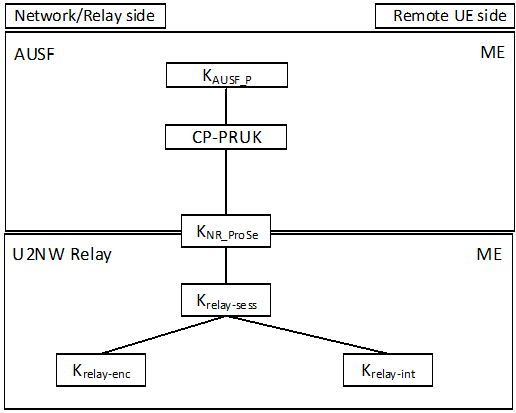
Figure 6.3.3.3.3-1: PC5 Key Hierarchy for 5G ProSe UE-to-Network Relay security over Control Plane
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
The different layers of keys (see Figure 6.3.3.3.3-1) are the following:
- KAUSF_P: A key derived based on 5G ProSe Remote UE specific authentication, only used to derive CP-PRUK.
- CP-PRUK: The root credential derived from KAUSF_P that is the root of security of the PC5 unicast link used for 5G ProSe UE-to-Network Relay service.
- KNR_ProSe: This is a 256-bit root key that is established between the two entities that communicating using NR PC5 unicast link.
- Krelay-sess: This is the 256-bit key that is derived by UE from KNR_ProSe and is used derive keys that to protect the transfer of data between the UEs. The Krelay-sess is derived per unicast link same as KNRP-sess specified in TS 33.536. During activated unicast communication session between the UEs, the Krelay-sess may be refreshed by running the rekeying procedure. The keys for confidentiality and integrity algorithms are derived directly from Krelay-sess. The 16-bit Krelay-sess ID identifies the Krelay-sess.
- Krelay-int, Krelay-enc: The Krelay-int and Krelay-enc are used in the chosen confidentiality and integrity algorithms respectively for protecting PC5-S signalling, PC5 RRC signalling, and PC5 user plane data. These keys are equivalent to NRPIK and NRPEK as specified in TS 33.536. They are derived from Krelay-sess and are refreshed automatically every time Krelay-sess is changed.
6.3.3.3.4 Void
6.3.3.4 Security for 5G ProSe Communication via Layer-3 UE-to-Network Relay with N3IWF support p. 38
The 5G ProSe Layer-3 Remote UE selects N3IWF as specified in TS 23.304.
The 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay shall establish security for PC5 connection using either User Plane based solution as specified in clause 6.3.3.2 or Control Plane based solution as specified in clause 6.3.3.3. Then, the 5G ProSe Layer-3 Remote UE performs the security procedures as specified in clause 7.2.1 of TS 33.501.