Content for TS 33.503 Word version: 17.2.0
6.3.3.2 Security procedure over User Plane
6.3.3.2.1 General
6.3.3.2.2 PC5 security establishment for 5G ProSe UE-to-Network relay communication over User Plane
6.3.3.2.3 PC5 Key Hierarchy over User Plane
...
...
6.3.3.2 Security procedure over User Plane p. 28
6.3.3.2.1 General p. 28
This clause describes a mechanism to setup a PC5 link between a 5G ProSe Remote UE and 5G ProSe UE-to-Network Relay. The mechanism includes how a 5G ProSe Remote UE and 5G ProSe UE-to-Network Relay get authorized by the 5G ProSe Key Management Function (5G PKMF) and verify each other's roles.
6.3.3.2.2 PC5 security establishment for 5G ProSe UE-to-Network relay communication over User Plane p. 29
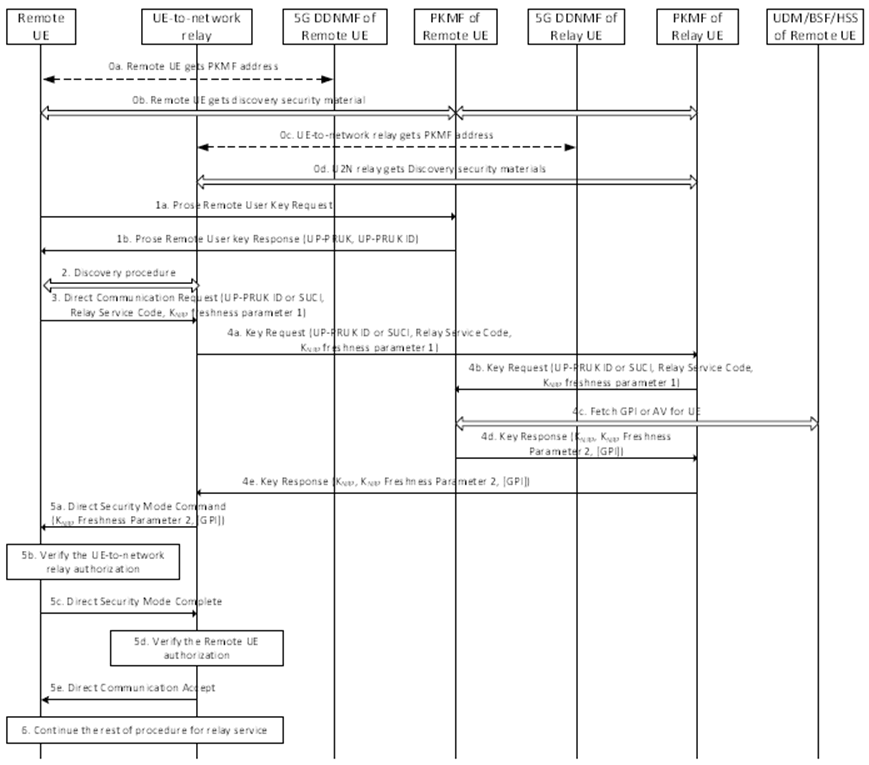
Figure 6.3.3.2.2-1: PC5 security establishment procedure for 5G ProSe UE-to-Network relay communication over User Plane
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
The 5G ProSe Remote UE is provisioned with the discovery security materials (see clause 6.1.3.2) and Prose Remote User Key (UP-PRUK) when it is in coverage. These security materials are associated with an expiration time, after which they become invalid. If the UE does not have valid discovery security materials, the 5G ProSe Remote UE needs to connect to the 5G PKMF and obtain fresh ones to use the 5G ProSe UE-to-Network Relay services.
Step 0a.
When the 5G ProSe Layer-3 UE-to-Network Relay sends a Remote UE Report to the SMF as specified in TS 23.304, the 5G ProSe Layer-3 UE-to-Network Relay shall include Remote User ID received in step 4d. If the UP-PRUK ID used as Remote User ID is not in NAI format, the 5G ProSe Layer-3 UE-to-Network Relay shall include the HPLMN ID of the 5G ProSe Remote UE in the Remote UE Report.
If the 5G ProSe Remote UE receives from the 5G ProSe UE-to-Network Relay a Direct Connection Reject due to UP-PRUK ID not found in the network, the 5G ProSe Remote UE shall not attempt to reconnect with the 5G ProSe UE-to-Network Relay using the UP-PRUK ID. The 5G ProSe Remote UE may attempt to connect with the 5G ProSe UE-to-Network Relay using its SUCI.
The 5G ProSe Remote UE gets the 5G PKMF address from the 5G DDNMF of its HPLMN. Alternatively, the 5G ProSe Remote UE may be provisioned with the 5G PKMF address by PCF. If the 5G ProSe Remote UE is provisioned with the 5G PKMF address, the 5G ProSe Remote UE may access the 5G PKMF directly without requesting it from the 5G DDNMF. In case that the 5G ProSe Remote UE cannot access the 5G PKMF using the provisioned 5G PKMF address, the 5G ProSe Remote UE may request the 5G PMKF address to the 5G DDNMF.
Step 0b.
The 5G ProSe Remote UE shall establish a secure connection with the 5G PKMF via PC8 reference point. Security for PC8 interface relies on Ua security if GBA specified in TS 33.220 is used (see clause 5.2.3.4) or Ua* security if AKMA specified in TS 33.535 is used (see clause 5.2.5.4). The 5G PKMF of the 5G ProSe Remote UE shall check whether the 5G ProSe Remote UE is authorized to receive UE-to-Network Relay service, and if the UE is authorized, the 5G PKMF of the 5G ProSe Remote UE provides the discovery security materials to the 5G ProSe Remote UE. If the 5G ProSe Remote UE provides a list of visited networks, the 5G PKMF of the 5G ProSe Remote UE shall request the discovery security materials from the 5G PKMFs of the potential 5G ProSe UE-to-Network Relays from which the 5G ProSe Remote UE gets the relay services. The 5G PKMF of the 5G ProSe UE-to-Network Relay may include the PC5 security policies to the 5G ProSe Remote UE.
Step 0c.
The 5G ProSe UE-to-Network Relay gets the 5G PKMF address from its HPLMN in the same way as described in step 0a.
Step 0d.
The 5G ProSe UE-to-Network Relay shall establish a secure connection with the 5G PKMF via PC8 reference point as in step 0b. The 5G PKMF of the 5G ProSe UE-to-Network Relay shall check whether the 5G ProSe UE-to-Network Relay is authorized to provide 5G ProSe UE-to-Network Relay service, and if the UE is authorized, the 5G PKMF of the 5G ProSe UE-to-Network Relay provides the discovery security materials to the 5G ProSe UE-to-Network Relay. The 5G PKMF of the 5G ProSe UE-to-Network Relay may include the PC5 security policies to the 5G ProSe UE-to-Network Relay.
Step 1a.
The 5G ProSe Remote UE sends a UP-PRUK Request message to its 5G PKMF. The message indicates that the 5G ProSe Remote UE is requesting a UP-PRUK from the 5G PKMF. If the 5G ProSe Remote UE already has a UP-PRUK from this 5G PKMF, the message shall also contain the UP-PRUK ID of the UP-PRUK.
UP-PRUK ID shall take the form of either the NAI format or the 64-bit string. If the UP-PRUK ID is in NAI format, i.e. username@realm, the realm part shall include Home Network Identifier (i.e. HPLMN ID). The username part shall include the 64-bit string.
Step 1b.
The 5G PKMF checks whether the 5G ProSe Remote UE is authorized to receive UE-to-Network Relay services. This is done by using the 5G ProSe Remote UE's identity associated with the key used to establish the secure connection between the 5G ProSe Remote UE and 5G PKMF in step 0b. If the 5G ProSe Remote UE is authorized to receive the service, the 5G PKMF sends a UP-PRUK and UP-PRUK ID to the 5G ProSe Remote UE. If a UP-PRUK and UP-PRUK ID are included, the 5G ProSe Remote UE shall store these and delete any previously stored ones for this 5G PKMF.
Step 2.
The discovery procedure is performed between the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay using the discovery parameters and discovery security material as described in clause 6.1.3.2.
Step 3.
The 5G ProSe Remote UE sends a Direct Communication Request (DCR) that contains the UP-PRUK ID or a SUCI if the Remote UE does not have a valid UP-PRUK, Relay Service Code (RSC) of the 5G ProSe UE-to-Network Relay service and KNRP freshness parameter 1 to the 5G ProSe UE-to-Network Relay. If the UP-PRUK ID is not in NAI format, the DCR message shall include the HPLMN ID of the 5G ProSe Remote UE. The PC5 security establishment procedure between the 5G ProSe Remote UE and the 5G ProSe UE-to-Network Relay including security parameters and security policy negotiation and protection of messages hereafter shall follow the one-to-one security establishment described in clause 6.2.3 of the present document. Only additional parameters required for the 5G ProSe Layer-3 UE-to-Network Relay scenario are described in this clause. The privacy and integrity protection of DCR are described in clause 6.3.5.
Step 4a.
The 5G ProSe UE-to-Network Relay sends a Key Request message that contains UP-PRUK ID or SUCI, RSC and KNRP freshness parameter 1 to its 5G PKMF. The Key Request message shall also include the HPLMN ID of the 5G ProSe Remote UE if it is included in the DCR.
Step 4b.
On receiving the Key Request message, the 5G PKMF of the 5G ProSe UE-to-Network Relay shall check if the 5G ProSe UE-to-Network Relay is authorized to provide relay service to the 5G ProSe Remote UE based on the 5G ProSe UE-to-Network Relay's identity associated with the key used to establish the secure PC8 connection and the received RSC.
If the 5G ProSe UE-to-Network Relay's authorization information is not locally available, the 5G PKMF shall request the authorization information from the UDM of the 5G ProSe UE-to-Network Relay (not shown in the figure) using Nudm_SDM_Get service as described in TS 23.502. If the 5G ProSe UE-to-Network Relay is authorized to provide the relay service based on ProSe Subscription data as specified in TS 23.502, the 5G PKMF of the 5G ProSe UE-to-Network Relay sends the Key Request with the UP-PRUK ID or the SUCI to the 5G PKMF of the 5G ProSe Remote UE. The 5G PKMF of the 5G ProSe UE-to-Network Relay identifies the 5G PKMF address of the 5G ProSe Remote UE based on the UP-PRUK ID or HPLMN ID or SUCI of the 5G ProSe Remote UE if it is included in the Key Request message.
Step 4c.
On receiving the Key Request message from the 5G PKMF of the 5G ProSe UE-to-Network Relay, the 5G PKMF of the 5G ProSe Remote UE shall check if the 5G ProSe Remote UE is authorized to use the relay service. The relay service authorization check shall be based on the UP-PRUK ID and RSC included in the Key Request message or the SUPI of the Remote UE and the RSC included in the Key Request message. If a SUCI is included in the Key Request message, the 5G PKMF of the 5G ProSe Remote UE shall request the UDM of the 5G ProSe Remote UE to de-conceal the SUCI to gain the SUPI using Nudm_UEIdentifier_Deconceal service, and the UDM invokes SIDF to de-conceal SUCI to gain SUPI. If the 5G ProSe Remote UE's authorization information is not locally available, the 5G PKMF shall request the authorization information from the UDM of the 5G ProSe Remote UE (not shown in Figure 6.3.3.2.2-1).
If a new UP-PRUK is required, the 5G PKMF shall perform the one of the following procedures (as shown in the step 4c in Figure 6.3.3.2.2-1):
Step 4d.
- If the 5G PKMF of the 5G ProSe Remote UE supports the Zpn interface to the BSF of the 5G ProSe Remote UE, the 5G PKMF of the 5G ProSe Remote UE may request a GBA Push Info (GPI - see TS 33.223) for the 5G ProSe Remote UE from the BSF. When requesting the GPI, the 5G PKMF shall include a UP-PRUK ID in the P-TID field. On receiving the GPI, the 5G PKMF shall use Ks(_ext)_NAF as the UP-PRUK.
- If the 5G PKMF of the 5G ProSe Remote UE supports the SBI interface to the BSF of the 5G ProSe Remote UE, the 5G PKMF may request the GPI via SBI interface as described in TS 33.223. On receiving the GPI, the 5G PKMF shall use Ks(_ext)_NAF as the UP-PRUK.
- If the 5G PKMF of the 5G ProSe Remote UE supports the PC4a interface to the HSS of the UE, then the 5G PKMF of 5G ProSe Remote UE may request a GBA Authentication Vector (AV) for the 5G ProSe Remote UE from the HSS. On receiving the AV, the 5G PKMF locally forms the GPI including a UP-PRUK ID in the P-TID field. The 5G PKMF shall use Ks(_ext)_NAF as the UP-PRUK.
- If the 5G PKMF of the 5G ProSe Remote UE is co-located or integrated with BSF functionality and supports the SBI interface to the UDM/HSS of the 5G ProSe Remote UE, the 5G PKMF may request the GBA AV via SBI interface as described in TS 33.220. On receiving the AV, the 5G PKMF locally forms the GPI including a UP-PRUK ID in the P-TID field. The 5G PKMF shall use Ks(_ext)_NAF as the UP-PRUK.
The 5G PKMF of the 5G ProSe UE-to-Network Relay sends the Key Response message to the 5G ProSe UE-to-Network Relay, which includes Remote User ID, KNRP, KNRP freshness parameter 2, the GPI if used to calculate a fresh UP-PRUK to the UE-to-Network Relay.
Step 4e.
The 5G PKMF of the 5G ProSe UE-to-Network Relay sends the Key Response message to the 5G ProSe UE-to-Network Relay, which includes Remote User ID, KNRP, KNRP freshness parameter 2, the GPI if used to calculate a fresh UP-PRUK to the UE-to-Network Relay.
Step 5a.
The 5G ProSe UE-to-Network Relay shall derive the session key (KNRP-SESS) from KNRP and then derive the confidentiality key (NRPEK) (if applicable) and integrity key (NRPIK) based on the PC5 security policies as specified in TS 33.536. The 5G ProSe UE-to-Network Relay shall store the Remote User ID received in step 4d. The 5G ProSe UE-to-Network Relay sends a Direct Security Mode Command message to the 5G ProSe Remote UE. This message shall also include the KNRP Freshness Parameter 2 in addition to the parameters specified in TS 33.536 and shall be protected as specified in TS 33.536.
Step 5b.
If the 5G ProSe Remote UE receives the message containing the GPI, it processes the GPI as described in TS 33.223. The 5G ProSe Remote UE shall derive the UP-PRUK and obtain the UP-PRUK ID from the GPI.
The 5G ProSe Remote UE shall derive KNRP from its UP-PRUK, RSC, KNRP Freshness Parameter 1 and the received KNRP Freshness Parameter 2 as specified in clause A.8. It shall then derive the session key (KNRP-SESS) and the confidentiality key (NRPEK) (if applicable) and integrity key (NRPIK) based on the PC5 security policies in the same manner as the 5G ProSe UE-to-Network Relay and process the Direct Security Mode Command. Successful verification of the Direct Security Mode Command assures the 5G ProSe Remote UE that the 5G ProSe UE-to-Network Relay is authorized to provide the relay service.
Handling of synchronization failure (for details of synchronization failures - see TS 33.102) when UE processes the authentication challenge in the GPI is performed similarly to clause 6.7.3.2.1.2 of TS 33.303. The 5G ProSe Remote UE shall send Direct Security Mode Failure message and include RAND and AUTS in the message. The 5G ProSe UE-to-Network Relay shall send the key request message to the 5G PKMF of the 5G ProSe Remote UE via the 5G PKMF of the 5G ProSe UE-to-Network Relay upon receiving the Direct Security Mode Failure message from the 5G ProSe Remote UE. The key request message shall include the HPLMN ID of the 5G ProSe Remote UE, if provided in step 3, the UP-PRUK ID or the SUCI of the 5G ProSe Remote UE received in step 3, Relay Service Code and KNRP freshness parameter 1 together with the RAND and the AUTS received from the 5G ProSe Remote UE. If the 5G PKMF of the 5G ProSe Remote UE decides to retry GBA Push procedure, the 5G PKMF of the 5G ProSe Remote UE shall request GPI as described in step 4c.
Step 5c.
The 5G ProSe Remote UE responds with a Direct Security Mode Complete message to the 5G ProSe UE-to-Network Relay as specified in TS 33.536.
Step 5d.
On receiving the Direct Security Mode Complete message, the 5G ProSe UE-to-Network Relay shall verify the Direct Security Mode Complete message. Successful verification of the Direct Security Mode Complete message assures the 5G ProSe UE-to-Network Relay that the 5G ProSe Remote UE is authorized to get the relay service.
5e. After successful verification, the 5G ProSe UE-to-Network Relay responds a Direct Communication Accept message to the 5G ProSe Remote UE to complete the PC5 connection establishment procedure.
Step 6.
The 5G ProSe Remote UE and 5G ProSe UE-to-Network Relay continues the rest of procedure for the relay service over the secure PC5 link such as establishing a new PDU session or modifying an existing PDU session for relaying, if needed etc.
6.3.3.2.3 PC5 Key Hierarchy over User Plane p. 33
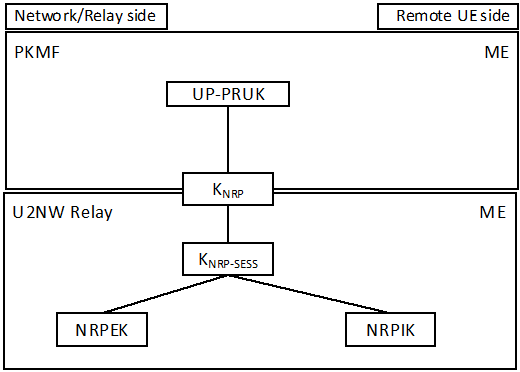
Figure 6.3.3.2.3-1: PC5 Key Hierarchy for 5G ProSe UE-to-Network Relay security over User Plane
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
The different layers of keys (see Figure 6.3.3.2.3-1) are the following:
- UP-PRUK: The root key of the PC5 unicast link.
- KNRP: The key is equivalent to KNRP as specified in TS 33.536. This key is derived as specified in clause A.8.
- KNRP-SESS: This key is derived as specified in TS 33.536.
- NRPEK, NRPIK: These keys are derived as specified in TS 33.536.