Content for TS 33.127 Word version: 18.7.0
0…
5…
5.4…
5.6…
5.7…
6…
6.2.2…
6.2.3…
6.2.5…
6.3…
6.3.3…
6.3.4…
6.4…
7…
7.3…
7.4…
7.4.7…
7.5…
7.6…
7.7…
7.8…
7.9…
7.10…
7.11…
7.12…
7.13…
7.14…
7.15…
7.16…
8…
A…
A.2…
A.3…
A.4…
B…
D…
E…
6.2.2 LI at AMF
6.2.2.1 Architecture
6.2.2.2 Target identities
6.2.2.3 Identity privacy
6.2.2.4 IRI events
6.2.2.5 Common IRI parameters
6.2.2.6 Specific IRI parameters
6.2.2.7 Network topologies
6.2.2A Identifier Reporting for AMF
6.2.2A.1 General
6.2.2A.2 IEF Events
6.2.2A.3 IEF Event parameters
6.2.2A.4 Network topologies
...
...
6.2.2 LI at AMF p. 43
6.2.2.1 Architecture p. 43
In the 5GC network, the AMF handles the access and mobility functions as well as provides or facilitates UE location information delivery to other NFs in the course of location-related service operations, such as LCS or Location Reporting. The AMF shall have LI capabilities to generate the target UE's network access, registration, connection management, and location update related xIRI. Extending the generic LI architecture presented in clause 5, Figure 6.2-3 below gives a reference point representation of the LI architecture with AMF as a CP NF providing the IRI-POI functions.
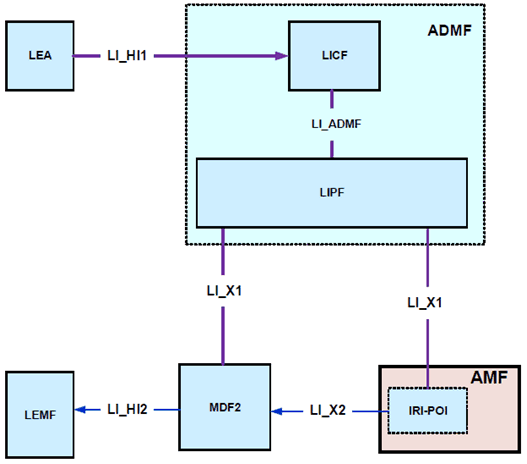
The LICF present in the ADMF receives the warrant from an LEA, derives the intercept information from the warrant and provides the same to the LIPF.
The LIPF present in the ADMF provisions the IRI-POI (over LI_X1) present in the AMF and the MDF2. The LIPF may interact with the SIRF (over LI_SI) present in the NRF to discover the AMFs in the network.
The IRI-POI present in the AMF detects the target UE's access and mobility related functions (network access, registration and connection management), generates and delivers the xIRI to the MDF2 over LI_X2. The MDF2 delivers the IRI messages as part of the Interception Product to the LEMF over LI_HI2.
6.2.2.2 Target identities p. 44
The LIPF present in the ADMF provisions the intercept information associated with the following target identities to the IRI-POI present in the AMF:
- SUPI.
- PEI.
- GPSI.
6.2.2.3 Identity privacy p. 45
TS 33.501 defines the ability to prevent the SUPI being exposed over the 5G RAN through the use of SUCI. Where SUPI privacy is implemented by both the UDM and UE, the SUPI is not sent in the clear over the RAN. Therefore, AMF has to rely on the UDM to provide the SUPI as part of the registration procedure as defined in TS 33.501.
If the AMF receives a SUCI from the UE then the AMF shall ensure for every registration (including re-registration) that SUPI has been provided by the UDM to the AMF and that the SUCI to SUPI mapping has been verified as defined in TS 33.501. This shall be performed regardless of whether the SUPI is a target of interception.
The AMF IRI-POI shall provide both the SUPI and the current SUCI in all applicable events defined in clause 6.2.2.4.
6.2.2.4 IRI events p. 45
The IRI-POI present in the AMF shall generate xIRI, when it detects the following specific events or information:
- Registration.
- Deregistration.
- Location update.
- Identifier association.
- Start of interception with already registered UE.
- Unsuccessful procedure.
- Positioning info transfer.
- Handover.
- Trace.
- UE policy transfer.
- Service accept.
- network-based or network-assisted positioning requests, responses or reports related to a target UE are being exchanged between LMF and NG-RAN via the AMF.
- UE-based or UE-assisted positioning requests, responses or reports related to a target UE are being exchanged between LMF and the target UE via the AMF.
6.2.2.5 Common IRI parameters p. 46
The list of xIRI parameters is specified in TS 33.128. All xIRI shall include the following:
- Target identity.
- Time stamp.
- Correlation information.
6.2.2.6 Specific IRI parameters p. 46
The list of parameters in each xIRI is defined in TS 33.128. The following give a summary.
The registration xIRI shall include the following:
- Registration type information.
- Access type information.
- Requested slice information.
- UE initiated de-registration.
- Access type information.
- Network initiated de-registration.
- Location of the target UE (see clause 7.3).
- Subscription permanent identifier.
- Temporary identifier association (i.e. SUCI or 5G-GUTI).
- Association change type indication.
- Access type information.
- Requested slice information.
- Rejected type of communication attempt.
- Access type information.
- Failure reason.
- Handover type and reason.
- Radio related information.
- UE capability information.
- Trace related information.
- UE policies.
- Service request related information.
- Service accept related information.
6.2.2.7 Network topologies p. 47
The AMF shall provide the IRI-POI functions in the following network topology cases:
- Non-roaming case.
- Roaming case, in VPLMN.
- Roaming case, in HPLMN for non-3GPP access.
6.2.2A Identifier Reporting for AMF p. 47
6.2.2A.1 General p. 47
The AMF shall provide IEF capabilities. The IEF present in the AMF shall support LI_XEM1 interface and upon activation shall provide IEF events to the ICF over LI_XER interface.
The IEF shall not generate events prior to UEs being successfully registered by the AMF onto the network.
6.2.2A.2 IEF Events p. 48
The IEF present in the AMF shall generate report records, when it detects the following specific events or information for any UE:
- Association of a 5G-GUTI to a SUPI (this may also include SUCI to SUPI association).
- De-association of a 5G-GUTI from a SUPI.
6.2.2A.3 IEF Event parameters p. 48
The list of event parameters is specified in TS 33.128. Each event shall include at the minimum the following information:
- Subscription permanent identifier.
- Observed temporary identifier(s).
- Cell identity (see clause 7.3).
- Time stamp of event.
- AMF identifier (including Region and Set Identifiers).
- Tracking area identifier.
- Registration area (including tracking area identifier list).
- Permanent equipment identifier.
6.2.2A.4 Network topologies p. 48
Since the IEF generates events independently of network topology for individual service usage UEs, no specific network topology handling is provided by the IEF. The IQF shall be responsible for handling any network topology requirements that may be applied by the LEA in an individual warrant.