Content for TS 33.127 Word version: 18.7.0
0…
5…
5.4…
5.6…
5.7…
6…
6.2.2…
6.2.3…
6.2.5…
6.3…
6.3.3…
6.3.4…
6.4…
7…
7.3…
7.4…
7.4.7…
7.5…
7.6…
7.7…
7.8…
7.9…
7.10…
7.11…
7.12…
7.13…
7.14…
7.15…
7.16…
8…
A…
A.2…
A.3…
A.4…
B…
D…
E…
6 Network layer based interception p. 42
6.1 General p. 42
Clause 6 gives details for the configuration of the high-level LI architecture for network layer based interception. It defines aspects of the LI configuration specific to each network under consideration (e.g. 5G), while aspects concerning services delivered over this network are considered in clause 7.
6.2 5G p. 42
6.2.1 General p. 42
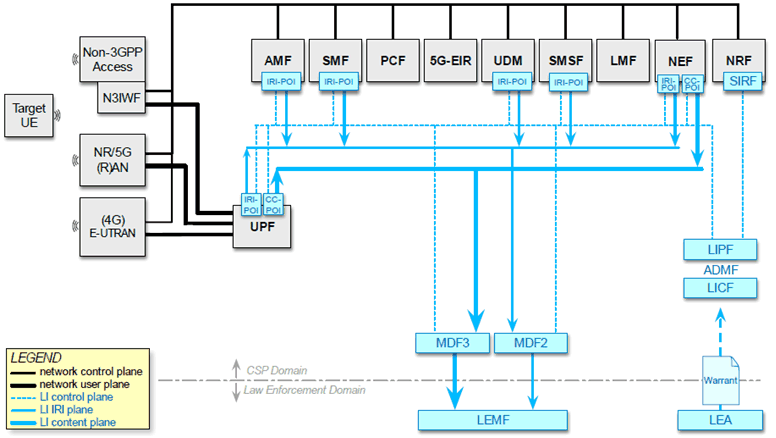
Figure 6.2-1 depicts the 5G EPC-anchored LI architecture. The network functions are depicted in grey, while the LI elements are depicted in blue.
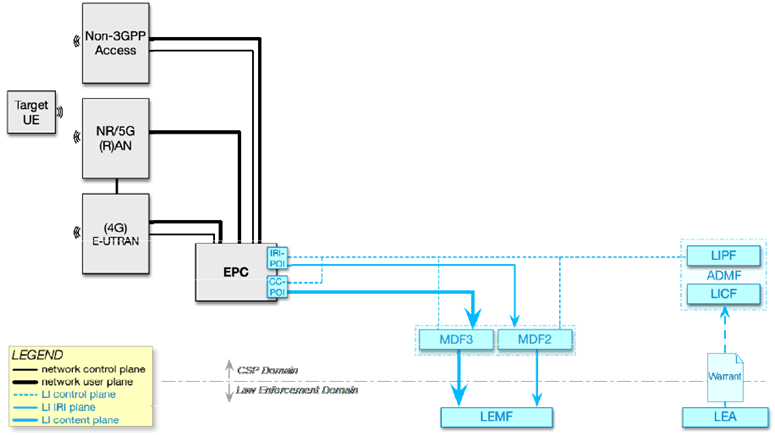
Figure 6.2-2 depicts the 5G core-anchored LI architecture. The network functions are depicted in grey, while the LI elements are depicted in blue.