Content for TS 33.127 Word version: 18.7.0
0…
5…
5.4…
5.6…
5.7…
6…
6.2.2…
6.2.3…
6.2.5…
6.3…
6.3.3…
6.3.4…
6.4…
7…
7.3…
7.4…
7.4.7…
7.5…
7.6…
7.7…
7.8…
7.9…
7.10…
7.11…
7.12…
7.13…
7.14…
7.15…
7.16…
8…
A…
A.2…
A.3…
A.4…
B…
D…
E…
5.4 LI interfaces
5.4.1 General
5.4.2 Interface LI_SI
5.4.3 Interface LI_HI1
5.4.4 Interface LI_X1
5.4.4.1 General
5.4.4.2 LIPF and POI
5.4.4.3 LIPF and TF
5.4.4.4 LIPF and MDF2/MDF3
5.4.5 Interface LI_X2
5.4.6 Interface LI_X3
5.4.7 Interface LI_T
5.4.7.1 General
5.4.7.2 Interface LI_T2
5.4.7.3 Interface LI_T3
5.4.8 Interface LI_HI2
5.4.9 Interface LI_HI3
5.4.10 Interface LI_HI4
5.4.10.1 General
5.4.10.2 LI operation notification
5.4.10.3 Contents of the notification
5.4.11 Interface LI_ADMF
5.4.12 Interface LI_MDF
5.4.13 Interface LI_IQF
5.4.14 Interface LI_XQR
5.4.15 Interface LI_HIQR
5.4.16 Interface LI_XER
5.4.17 Interface LI_XEM1
5.4.18 Interface LI_HILA
5.4.19 Interface LI_XLA
5.4.20 Interface LI_X2_LA
5.4.21 Interface LI_LAFP and LI_LAFC
5.5 LI service discovery
...
...
5.4 LI interfaces p. 25
5.4.1 General p. 25
A high-level interception architecture diagram showing key point-to-point LI interfaces is shown in Figure 5.4.1-1 below.
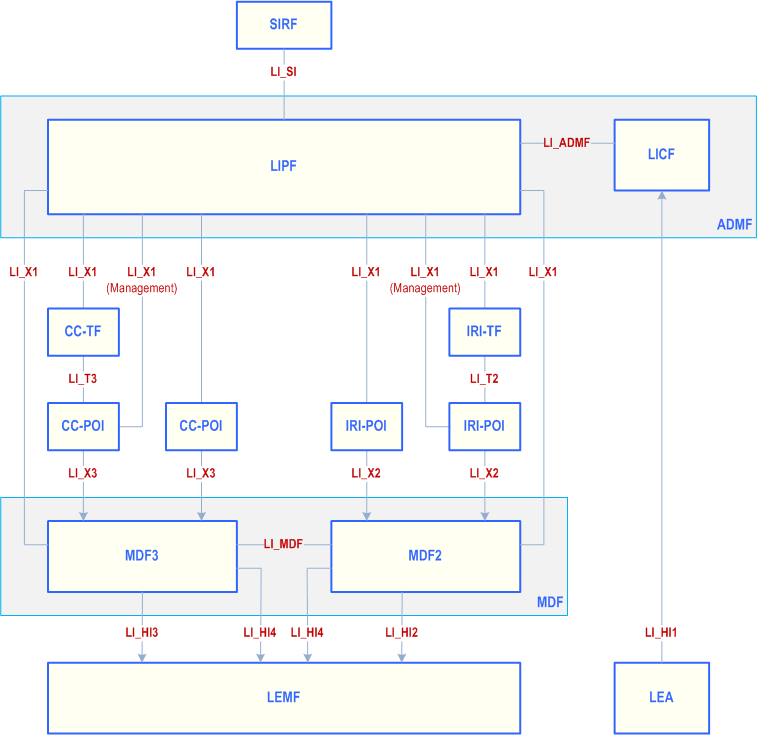
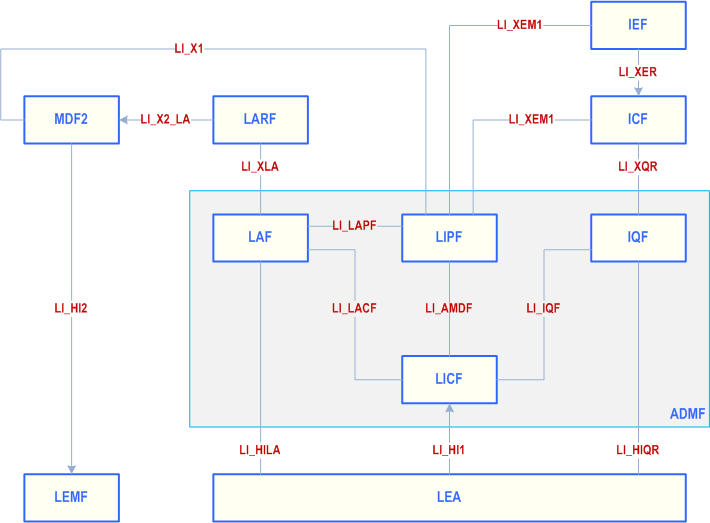
A high-level acquisition architecture diagram showing key point-to-point LI interfaces is shown in Figure 5.4.1-2 below.
5.4.2 Interface LI_SI p. 27
LI_SI is an interface between the SIRF and LIPF. SIRF uses this interface to provide the system information to the LIPF. The LIPF may request the SIRF for such information before sending the intercept provisioning information to the POIs. The SIRF may also notify the LIPF whenever the status of a system function changes (e.g. removed from service, migrating to another location, etc.).
5.4.3 Interface LI_HI1 p. 27
LI_HI1 is used to send warrant and other interception request information from the LEA to the CSP. This interface may be electronic or may be an offline manual process depending on national warranty processes.
The following are some of the information elements sent over this interface:
- Target identifier: used to identify the communications to be intercepted.
- Type of intercept: used to indicate whether IRI only, CC only, or both IRI and CC, is to be delivered to the LEMF.
- Location acquisition: used to indicate whether location acquisition is required (in addition to lawful interception for other services, only location acquisition, or no location acquisition) and the type of delivery (via LI_HILA, via LI_HI2, or both).
- Service scoping: used to identify the service (e.g. voice, packet data, messaging, target positioning) to be intercepted.
- Filtering criteria: used to provide additional specificity for the interception (e.g. for bandwidth optimization).
- LEMF address: used to deliver the Interception Product.
- Lawful Interception Identifier (LIID) used to associate the issued warrant with the Interception Product.
5.4.4 Interface LI_X1 p. 28
5.4.4.1 General p. 28
LI_X1 interfaces are used to manage the POIs and TFs and to provision LI target information on the POIs and TFs in order to intercept target communications. LI_X1 interfaces are also used to manage and provision MDFs with the necessary information to deliver those communications in the correct format to LEMFs.
LI_X1 interfaces shall support the use of ETSI TS 103 221-1 [8] for transport of X1 messages / information. However, the requirements specified in the present document shall apply regardless of generic default options specified in ETSI TS 103 221-1 [8].
5.4.4.2 LIPF and POI p. 28
The following are examples of some of the information that may be passed over LI_X1 to the POI as a part of intercept provisioning:
- Information necessary to associate multiple xIRI/xCC at MDF2/MDF3.
- Target identifier.
- Type of intercept (IRI only; CC only; or IRI and CC).
- Service scoping.
- Further filtering criteria.
- Address of MDF2 or MDF3.
5.4.4.3 LIPF and TF p. 28
The following are examples of some of the information that may be passed over LI_X1 to the TF as a part of intercept provisioning:
- Information necessary to associate multiple xIRI/xCC at MDF2/MDF3.
- Target identifier.
- Type of intercept (IRI only; CC only; or IRI and CC).
- Service scoping.
- Further filtering criteria.
- Address of MDF2 or MDF3.
5.4.4.4 LIPF and MDF2/MDF3 p. 29
The following are examples of some of the information that may be passed over LI_X1 to the MDF2/MDF3 as a part of intercept provisioning:
Information necessary used to associate multiple xIRI/xCC at MDF2/MDF3.
- Target identifier.
- Lawful Interception identifier.
- Type of intercept (IRI only; CC only; or IRI and CC).
- Service scoping.
- Further filtering criteria.
- LEMF address.
5.4.5 Interface LI_X2 p. 29
The LI_X2 interfaces are used to pass xIRI from IRI-POIs to the MDF2.
The following are some of the information passed over this interface to the MDF2 as a part of xIRI:
- Target identifier.
- Time stamp.
- Correlation information.
- IRI event resulting in xIRI.
5.4.6 Interface LI_X3 p. 29
LI_X3 interfaces are used to pass real-time content of communications (i.e. xCC) and associated metadata from CC-POIs to MDF3.
The following are some of the information passed over this interface to the MDF3 as a part of xCC:
- Target identifier.
- Time stamp.
- Correlation information.
- User plane packets.
5.4.7 Interface LI_T p. 29
5.4.7.1 General p. 29
The LI_T interface is used to pass the triggering information from the Triggering Function to the POI. Depending on the POI type, two types of LI_T are defined:
- LI_T2.
- LI_T3.
5.4.7.2 Interface LI_T2 p. 30
The LI_T2 interface is from IRI-TF to IRI-POI.
The following are some of the information passed over this interface to the IRI-POI:
- Target identifier.
- IRI interception rules.
- MDF2 address.
- Correlation information.
5.4.7.3 Interface LI_T3 p. 30
LI_T3 interface is from CC-TF to CC-POI.
The following are some of the information passed over this interface to CC-POI:
- Target identifier.
- CC interception rules.
- MDF3 address.
- Correlation information.
5.4.8 Interface LI_HI2 p. 30
LI_HI2 is used to send IRI from the MDF2 to the LEMF. This interface is defined in TS 33.128.
5.4.9 Interface LI_HI3 p. 30
LI_HI3 is used to send CC from the MDF3 to the LEMF. This interface is defined in TS 33.128.
5.4.10 Interface LI_HI4 p. 30
5.4.10.1 General p. 30
LI_HI4 is used by the MDF2 and MDF3 to report to the LEMF that the MDF2/3 have been provisioned as expected. This capability is mandatory to support but optional to use (subject to relevant national agreement) at both MDF2 and MDF3.
5.4.10.2 LI operation notification p. 30
The MDF2 and MDF3 shall support reporting to the LEMF changes to provisioning, including:
- Activation of LI.
- Modification of active LI.
- Deactivation of LI.
5.4.10.3 Contents of the notification p. 31
Each notification shall include at least the following:
- The type of notification (e.g. activation, deactivation).
- Relevant related information (LIID, time of change).
5.4.11 Interface LI_ADMF p. 31
LI_ADMF is an interface between LICF and LIPF and is used by the LICF to send the intercept provisioning information to the LIPF. Further details about this interface are outside the scope of the present document.
5.4.12 Interface LI_MDF p. 31
LI_MDF is an interface between MDF2 and MDF3 and is used for MDF2 and MDF3 to interact with each other in the generation of IRI and CC. Further details about this interface are outside the scope of the present document.
5.4.13 Interface LI_IQF p. 31
LI_IQF is an interface between LICF and IQF and is used by the LICF to send management information related to IEFs and ICF, to the IQF. Further details about this interface are outside the scope of the present document.
5.4.14 Interface LI_XQR p. 31
The LI_XQR interface is used by the IQF to send identifier association queries to the ICF and from the ICF to return identities associations to the IQF in response.
The following are examples of some of the information that may be passed over LI_XQR from the IQF to the ICF:
- Information relating to the type of query.
- Temporary or permanent identifier provided by the LEA.
-
Other information associated with identifier required for localisation provided by the LEA.
- Cell identity.
- Tracking area identifier.
- Time that identifier provided by the LEA was observed by the LEA.
- Location information request from the LEA.
- Information relating to the type of query being responded to.
- Temporary and permanent identifiers corresponding to identifier provided by LEA.
- Identifier association validity start and end times.
- Location information for the target, if requested by the LEA.
5.4.15 Interface LI_HIQR p. 31
The LI_HIQR interface is used by the LEA to send identifier association queries to the IQF and from the IQF to return identities associations to the LEA in response.
The following are examples of some of the information that may be passed over LI_HIQR from LEA to the IQF:
- Information relating to the type of query.
- Warrant/authorisation identifier.
- Temporary or permanent identifier provided by the LEA.
-
Other information associated with identifier required for localisation provided by LEA.
- Cell identity.
- Tracking area identifier.
- Time that identifier provided by LEA was observed by the LEA.
- Location information request.
- Information relating to the type of query being responded to.
- Warrant/authorisation identifier.
- Temporary and permanent identifiers corresponding to identifier provided by LEA.
- Identifier association validity start and end times.
- Location information for the target, if requested by the LEA.
5.4.16 Interface LI_XER p. 32
The LI_XER interface is used by the IEF to send identifier association events to the ICF.
The following are examples of some of the information that may be passed over LI_XER from the IEF to the ICF:
- Permanent identifier and temporary identifier association.
- Permanent identifier and temporary identifier excommunication / de-association.
- Time stamp of association observation.
- Location information.
5.4.17 Interface LI_XEM1 p. 32
The LI_XEM1 interface is used by the LICF (proxied by the LIPF) to manage and control the activation state of the IEF(s) and ICF.
LI_XEM1 interfaces shall support the use of ETSI TS 103 221-1 [8] for transport of XEM1 messages / information. However, the requirements specified in the present document shall apply regardless of generic default options specified in [8].
5.4.18 Interface LI_HILA p. 32
The LI_HILA interface is used by the LEA to forward the location acquisition requests to the LAF and when required to forward the location acquisition responses from the LAF to the LEA.
The following are examples of some of the information that may be passed over the LI_HILA interface:
- Target identifier (IMSI, MSISDN, SUPI, GPSI).
- Authorisation identifier (LIID).
- Timestamp of when the target's location was acquired.
- Location information.
5.4.19 Interface LI_XLA p. 33
The LI_XLA interface is used by the LAF to forward the location acquisition requests to the LARF and when required to forward the location acquisition responses from the LARF to the LAF if the delivery type of location acquisition delivery is via the LI_HILA.
The following are examples of some of the information that may be passed over the LI_XLA interface from LAF to LARF:
- Internal interception identifier.
- Target identifier (IMSI, MSISDN, SUPI, GPSI).
- Information relating to the type of delivery (via LI_HILA, via LI_HI2, or both).
- Address of MDF2.
- Timestamp of when the target's location was acquired.
- Location information.
5.4.20 Interface LI_X2_LA p. 33
LI_X2_LA interfaces are used to pass the xIRI containing location acquisition outcomes between the LARF to the MDF2. It is realised using TS 103 221-2 [16].
5.4.21 Interface LI_LAFP and LI_LAFC p. 33
LI_LAFP and LI_LAFC are interfaces used to exchange relevant information between the LIPF, LICF and the LAF. Further details about this interface are outside the scope of the present document.
5.5 LI service discovery p. 33
In SBA as defined in TS 23.501 the NRF is a central repository of discoverable NFs. For NFs to be discoverable, they need to have been previously instantiated and undergone a degree of configuration (function identity allocated, IP addresses, certificates, network connectivity to NRF, etc.).
LI functions (e.g. ADMF, POIs and MDFs) exist within a separate security domain to the main network NF to which they are embedded. Furthermore, as with legacy networks, LI functions associated with NFs shall be configured and tested before the associated NF is allowed to enter active network user service (i.e. LI shall be configured and tested before an NF can handle live user traffic).
In the present document, all LI functions have dedicated LI_X interfaces and discovery of LI functions by the LIPF shall happen as part of the NF / LI function instantiation phase. POIs, TFs and MDFs shall not be subject to or within the scope of NRF service discovery as defined in TS 23.501. The SIRF is used to provide the LIPF with NF discovery information which shall be used to identify which NFs are applicable to intercept specific user sessions, as described in clause 5.3.6. However, the SIRF is not involved directly in LI service discovery.
The SIRF may be used to inform the LIPF that an NF has been registered / deregistered with the NRF and is now ready for use in a network user service. The LIPF is assumed to already have knowledge of which POIs and TFs are associated with which NFs.
POIs, TFs and MDFs may be discovered in virtualised deployments using the approach described in clause 5.6. The exact mechanisms for achieving this are out of scope of the present document.