Content for TS 23.273 Word version: 18.6.0
1…
4…
4.2…
4.2a…
4.3…
5…
5.5…
6…
6.1.2
6.1.3
6.1.4
6.2
6.3…
6.3.2…
6.4
6.5…
6.7…
6.7.3
6.7.4
6.7.5
6.8
6.9…
6.10…
6.11…
6.12…
6.13…
6.14…
6.15…
6.16…
6.17…
6.18…
6.19…
6.19.3…
6.20…
6.20.4…
6.21…
7…
8…
A…
B…
C…
6.7.5 Event Reporting in RRC INACTIVE state for UL+DL Positioning |R17| p. 83
Figure 6.7.5-1 summarizes the initiation and reporting of location events for a deferred 5GC-MT-LR procedure for Periodic or Triggered Location Events when a UE is in RRC INACTIVE state and when UL-DL positioning is used for event reporting. This procedure is only applicable to a UE with NR access to 5GC.
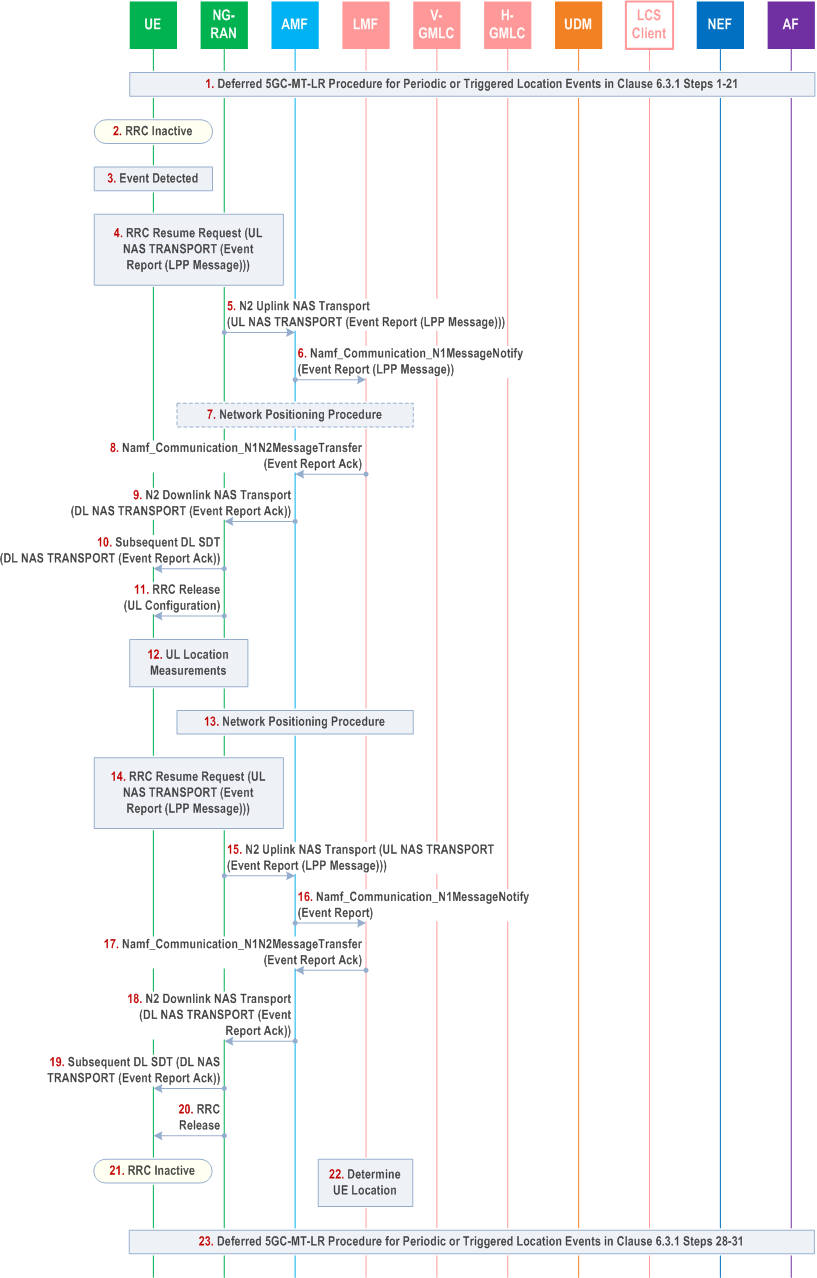
Step 1.
Steps 1-21 for the deferred 5GC-MT-LR procedure for periodic or triggered location events in clause 6.3.1 are performed with the following differences.
Step 2.
- At step 16 in clause 6.3.1, the LMF indicates to the UE that UL+DL positioning will be used for subsequent location reporting events when the UE is in RRC INACTIVE state by including an LPP positioning message in the LCS Periodic-Triggered Invoke Request sent to the UE at step 16, where the LPP positioning message identifies an UL-DL positioning method and requests DL location measurements for this positioning method. The LMF also includes a deferred routing identifier in the LCS Periodic-Triggered Location Invoke which is an identification of the LMF.
The UE enters RRC INACTIVE state some time before an event is detected at step 22 or step 31 in clause 6.3.1. If the UE is not in RRC INACTIVE state when an event is detected at step 22 or step 31 in clause 6.3.1, then the UE follows the procedure described for steps 22-31 in clause 6.3.1 to report the event to the LMF and to the LCS Client or AF.
Step 3.
The UE monitors for and detects a trigger event as described for step 22 in clause 6.3.1.
Step 4.
The UE sends an RRC Resume Request with small data transmission (SDT) to a receiving gNB node in the NG-RAN. The RRC Resume Request includes an RRC UL Information Transfer message containing an UL NAS TRANSPORT message that includes a supplementary services event report message. The UE includes an LPP positioning message in the supplementary services event report message that includes a request for an UL Configuration to support the UL+DL positioning method indicated to the UE at step 1. The event report message also includes other information described in step 25 in clause 6.3.1 (e.g. the type of event being reported). The UL NAS TRANSPORT message also includes the deferred routing identifier received in step 16 in clause 6.3.1.
Step 5.
The receiving gNB node forwards the UL NAS TRANSPORT message to the serving AMF in an N2 Uplink NAS Transport message.
Step 6.
The AMF checks the integrity of the NAS message and deciphers its contents. The AMF then invokes an Namf_Communication_N1MessageNotify service operation to forward the event report to the serving LMF as described for step 25 in clause 6.3.1.
Step 7.
The LMF uses the Network Assisted Positioning Procedure in clause 6.11.2 to request the receiving gNB node to provide an UL configuration to the UE at step 11. The receiving gNB node then determines an UL Configuration to be used later at step 11 and indicates this to the LMF. The LMF also uses the Non-UE Associated Network Assistance Data procedure in clause 6.11.3 to request UL location measurements of the UE by NG-RAN gNB nodes.
Step 8.
The LMF invokes an Namf_Communication_N1N2MessageTransfer operation to return an acknowledgment for the event report as described for step 26 in clause 6.3.1.
Step 9.
The AMF forwards the acknowledgment to the receiving gNB node in a DL NAS TRANSPORT message which is encapsulated in an N2 Downlink NAS Transport message.
Step 10.
The receiving gNB node sends a Subsequent DL SDT message to the UE and includes the NAS message received in step 9.
Step 11.
The receiving gNB node sends an RRC Release message to the UE to keep the UE in RRC INACTIVE state and includes the UL Configuration determined at step 7.
Step 12.
The UE transmits UL positioning signals according to the UL Configuration received at step 11. The UE also obtains DL location measurements as requested at step 1. The NG-RAN gNB nodes that were requested to obtain UL location measurements at step 7 obtain the UL location measurements of the UL positioning signals transmitted by the UE.
Step 13.
The NG-RAN gNB nodes transfer the UL location measurements obtained at step 12 to the LMF according to the Non-UE Associated Network Assistance Data Procedure in clause 6.11.3.
Step 14.
The UE sends an RRC Resume Request with small data transmission to the receiving gNB node. The RRC Resume Request includes an RRC UL Information Transfer message containing an UL NAS TRANSPORT message that includes a supplementary services event report message. The event report message indicates that this is a second event report associated with the first event report sent at step 4 and includes an LPP positioning message that includes the DL location measurements obtained at step 12. The UL NAS TRANSPORT message also includes the deferred routing identifier received in either step 16 in clause 6.3.1 or step 10 in this procedure if there was a change of LMF.
Step 15.
The receiving gNB node forwards the UL NAS TRANSPORT message to the serving AMF in an N2 Uplink NAS Transport message.
Step 16.
The AMF checks the integrity of the NAS message and deciphers its contents. The AMF then invokes an Namf_Communication_N1MessageNotify service operation to forward the event report to the serving LMF as described for step 25 in clause 6.3.1.
Step 17.
The LMF invokes an Namf_Communication_N1N2MessageTransfer operation to return an acknowledgment for the event report as described for step 26 in clause 6.3.1.
Step 18.
The AMF forwards the acknowledgment to the receiving gNB node in a DL NAS TRANSPORT message which is encapsulated in an N2 Downlink NAS Transport message.
Step 19.
The receiving gNB node sends a Subsequent DL SDT message to the UE and includes the NAS message received in step 18.
Step 20.
The receiving gNB node sends an RRC Release message to the UE to keep the UE in RRC INACTIVE state.
Step 21.
Following step 20, the UE remains in RRC INACTIVE state.
Step 22.
The LMF determines the UE location using the UL location measurements received at step 13 and the DL location measurements received at step 16.
Step 23.
Steps 28-31 in clause 6.3.1 are performed to send the event report to the LCS client or AF.