Content for TS 29.500 Word version: 19.0.0
1…
5…
5.2.3.2…
5.2.3.3…
5.2.4…
6…
6.3…
6.4…
6.5…
6.6…
6.7…
6.10…
6.10.3…
6.10.6…
6.10.11…
6.10.12…
6.11…
A
B
C
D…
5 Protocols Over Service Based Interfaces
5.1 Protocol Stack Overview
5.2 HTTP/2 Protocol
5.2.1 General
5.2.2 HTTP standard headers
5.2.2.1 General
5.2.2.2 Mandatory to support HTTP standard headers
5.2.3 HTTP custom headers
5.2.3.1 General
...
...
5 Protocols Over Service Based Interfaces p. 14
5.1 Protocol Stack Overview p. 14
The protocol stack for the service-based interfaces is shown on Figure 5.1-1.
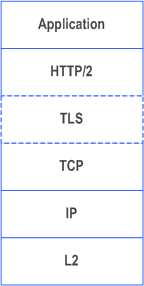
The service-based interfaces use HTTP/2 protocol (see clause 5.2) with JSON (see clause 5.4) as the application layer serialization protocol. For the security protection at the transport layer, all 3GPP NFs shall support TLS and TLS shall be used within a PLMN if network security is not provided by other means, as specified in TS 33.501.
5.2 HTTP/2 Protocol p. 14
5.2.1 General p. 14
HTTP/2 as described in RFC 9113 shall be used in Service based interface.
5.2.2 HTTP standard headers p. 15
5.2.2.1 General p. 15
This clause lists the HTTP standard headers that shall be supported on SBI, other HTTP standard headers defined in IETF RFCs may be supported by NF.
5.2.2.2 Mandatory to support HTTP standard headers p. 15
The HTTP request standard headers and the HTTP response standard headers that shall be supported on SBI are defined in Table 5.2.2.2-1 and in Table 5.2.2.2-2 respectively. Mandatory to support HTTP standard headers does not mean all the HTTP requests and responses carry the identified request and response headers respectively. It only means it is mandatory to support the processing of the identified headers in request and response message.
| Name | Reference | Description |
|---|---|---|
| Accept | RFC 9110 | This header is used to specify response media types that are acceptable. |
| Accept-Encoding | RFC 9110 | This header may be used to indicate what response content-encodings (e.g. gzip) are acceptable in the response. |
| Content-Length | RFC 9110 | This header is used to provide the anticipated size, as a decimal number of octets, for a potential content. |
| Content-Type | RFC 9110 | This header is used to indicate the media type of the associated representation. |
| Content-Encoding | RFC 9110 | This header may be used in some requests to indicate the content encodings (e.g. gzip) applied to the resource representation beyond those inherent in the media type. |
| User-Agent | RFC 9110 |
This header shall be mainly used to identify the NF type of the HTTP/2 client. This header should be included in every HTTP/2 request sent over any SBI; This header shall be included in every HTTP/2 request sent using indirect communication when target NF (re-)selection is to be performed at SCP.
For Indirect communications, the User-Agent header in a request that is:
|
| Cache-Control | RFC 9111 | This header may be used in some HTTP/2 requests to provide the HTTP cache-control directives that the client is willing to accept from the server. |
| If-Modified-Since | RFC 9110 | This header may be used in a conditional GET request, for server revalidation. This is used in conjunction with the Last-Modified server response header, to fetch content only if the content has been modified from the cached version. |
| If-None-Match | RFC 9110 | This header may be used in a conditional GET request. This is used in conjunction with the ETag server response header, to fetch content only if the tag value of the resource on the server differs from the tag value in the If-None-Match header. |
| If-Match | RFC 9110 | This header may be used in a conditional POST or PUT or DELETE or PATCH request. This is used in conjunction with the ETag server response header, to update / delete content only if the tag value of the resource on the server matches the tag value in the If-Match header. |
| Via | RFC 9110 | This header shall be inserted by HTTP proxies and it shall be inserted by an SCP and SEPP when relaying an HTTP request. When inserted by an SCP or SEPP, the header field value should be formatted as defined for the Via header in Table 5.2.2.2-2. |
| Authorization | RFC 9110 | This header shall be used if OAuth 2.0 based access authorization with "Client Credentials" grant type is used as specified in clause 13.4.1 of TS 33.501, Section 7 of RFC 6749 and RFC 6750. |
|
NOTE 1:
The value of NF type in the User-Agent header shall comply with the enumeration value (case insensitive) of Table 6.1.6.3.3-1 in TS 29.510.
|
||
| Name | Reference | Description |
|---|---|---|
| Content-Length | RFC 9110 | This header may be used to provide the anticipated size, as a decimal number of octets, for a potential content. |
| Content-Type | RFC 9110 | This header shall be used to indicate the media type of the associated representation. |
| Location | RFC 9110 | This header may be used in some responses to refer to a specific resource in relation to the response. |
| Retry-After | RFC 9110 | This header may be used in some responses to indicate how long the user agent ought to wait before making a follow-up request. |
| Content-Encoding | RFC 9110 | This header may be used in some responses to indicate to the HTTP/2 client the content encodings (e.g. gzip) applied to the resource representation beyond those inherent in the media type. |
| Cache-Control | RFC 9111 | This header may be used in some responses (e.g. NRF responses to queries) to provide HTTP response cache control directives. The cache directives "no-cache", "no-store", "max-age" and "must-revalidate" values shall be supported. |
| Age | RFC 9111 | This header may be inserted by HTTP proxies when returning a cached response. The "Age" header field conveys the sender's estimate of the amount of time since the response was generated or successfully validated at the origin server. The presence of an Age header field implies that the response was not generated or validated by the origin server for this request. |
| Last-Modified | RFC 9110 | This header may be sent to allow for conditional GET with the If-Modified-Since header. |
| ETag | RFC 9110 | This header may be sent to allow for conditional GET with the If-If-None-Match header or a conditional POST / PUT / PATCH / DELETE with the If-Match header. |
| Via | RFC 9110 | This header shall be inserted by HTTP proxies.
This header shall be inserted by an SCP or SEPP when relaying an HTTP error response (see clause 6.10.8). It may be inserted when relaying other HTTP responses.
When inserted by an SCP or SEPP, the received-protocol portion of the header field value should be set to "HTTP/2.0" or "2.0" and the received-by portion of the header field value should be formatted as follows:
|
| Allow | RFC 9110 | This header field shall be used to indicate methods supported by the target resource. |
| WWW-Authenticate | RFC 9110 | This header field shall be included when an NF service producer rejects a request with a "401 Unauthorized" status code (e.g. when a request is sent without an OAuth 2.0 access token or with an invalid OAuth 2.0 access token). |
| Accept-Encoding | RFC 9110 | See clause 6.9 for the use of this header. |
| Server | RFC 9110 |
This header should be inserted by the originator of an HTTP error response (see clause 6.10.8). It may be inserted otherwise.
When inserted by an NF, an SCP or a SEPP, the pattern of the header should be formatted as follows:
|
|
NOTE:
The value of NF type in the Server header shall comply with the enumeration value (case insensitive) of Table 6.1.6.3.3-1 in TS 29.510.
|
||
5.2.3 HTTP custom headers p. 18
5.2.3.1 General p. 18
The list of custom HTTP headers applicable to 3GPP Service Based NFs are specified below.
The ABNF definition of these custom headers is expressed in the following clauses using common syntax components defined in Section 5.6.2 of RFC 9110 to Section 5.6.5 of RFC 9110, such as <token> and <tchar>. As indicated there, the following characters (expressed by their UNICODE name) shall not be used as part of a <token>, or as a <tchar>:
If a 3GPP custom HTTP header, whose ABNF syntax definition uses the <token> or <tchar> components, needs to include a value containing a character outside of the character set allowed for <token> or <tchar>, such character shall be encoded using percent-encoding, as follows:
| QUOTATION MARK (U+0022) | " |
| LEFT PARENTHESIS (U+0028) | ( |
| RIGHT PARENTHESIS (U+0029) | ) |
| COMMA (U+002C) | , |
| SOLIDUS (U+002F) | / |
| COLON (U+003A) | : |
| SEMICOLON (U+003B) | ; |
| LESS-THAN SIGN (U+003C) | < |
| EQUALS SIGN (U+003D) | = |
| GREATER-THAN SIGN (U+003E) | > |
| QUESTION MARK (U+003F) | ? |
| COMMERCIAL AT (U+0040) | @ |
| LEFT SQUARE BRACKET (U+005B) | [ |
| REVERSE SOLIDUS (U+005C) | \ |
| RIGHT SQUARE BRACKET (U+005D) | ] |
| LEFT CURLY BRACKET (U+007B) | { |
| RIGHT CURLY BRACKET (U+007D) | } |
The HEXDIG ABNF production rule, originally defined in RFC 5234, shall be considered as if the uppercase hexadecimal digits 'A' through 'F' are equivalent to the lowercase digits 'a' through 'f', respectively.
The literal "%" character shall also be encoded as above (i.e. %25).
Percent encoding shall not be used for characters that are in the <token> or <tchar> allowed character set.
EXAMPLE:
3GPP Custom Header "3gpp-Sbi-Oci" (see clause 5.2.3.2.9) can include an optional parameter "snssai". If this parameter takes the value:
{"sst": 1, "sd": "A08923"}
it will be formatted, when included in this custom header, as:
S-NSSAI: %7B%22sst%22%3A%201%2C%20%22sd%22%3A%20%22A08923%22%7D