Content for TS 23.060 Word version: 18.0.0
1…
5…
5.3.8…
5.4…
5.4.2…
5.4.9…
5.6…
5.6.2
5.6.3…
5.6.3.7…
5.7…
6…
6.3…
6.5…
6.6…
6.8…
6.9…
6.9.1.3
6.9.2…
6.9.2.2…
6.9.2.2.2
6.9.2.2.3…
6.9.2.2.5…
6.9.3…
6.10…
6.12…
6.13…
6.13.1.2…
6.13.2…
6.13.2.2
6.14…
8…
8.2
9…
9.2.2…
9.2.2.2
9.2.2.3…
9.2.3…
9.2.3.2…
9.2.3.3…
9.2.4…
9.2.4.2…
9.2.5…
12…
12.5…
12.6…
12.7…
12.8…
13…
14…
15…
15.3…
16…
16.2…
A…
B…
6.8 Security Function
6.8.0 General
6.8.1 Authentication
6.8.2 User Identity Confidentiality
6.8.3 User Data and GMM/SM Signalling Confidentiality
6.8.4 Identity Check Procedures
6.8.5 Data Integrity Procedure (Iu mode)
...
...
6.8 Security Function p. 104
6.8.0 General |R8| p. 104
The GERAN/UTRAN Security function:
- Guards against unauthorised packet-domain service usage (authentication of the MS by the network and service request validation).
- Provides user identity confidentiality (temporary identification and ciphering).
- Provides user data and signalling confidentiality (ciphering).
- Provides, for Iu mode only, data integrity and origin authentication of signalling data (integrity protection).
- Provides, by UMTS authentication (USIM) only, authentication of the network by the MS. GERAN/UTRAN security-related network functions are described in TS 43.020 and in TS 33.102.
6.8.1 Authentication p. 105
The Authentication function includes two types of authentication: "UMTS authentication" and "GSM authentication". These procedures are independent of the RAN modes, i.e. each procedure may be executed in A/Gb mode or in Iu mode. UMTS authentication requires a USIM for the MS and Authentication Quintets in the SGSN. GSM authentication bases on a SIM for the MS and Authentication Triplets in the SGSN or it bases on a GSM capable USIM for the MS and parameters derived from Authentication Quintets in the SGSN.
"UMTS authentication" implies mutual authentication, i.e. authentication of the MS by the network and authentication of the network by the MS. It also implies establishment of a new UMTS ciphering key (CK) and integrity key (IK) agreement between the SGSN and the MS.
"GSM authentication" implies authentication of the MS by the network and establishment of a new GSM ciphering key (Kc) agreement between the SGSN and the MS.
6.8.1.1 GSM Authentication procedure p. 105
The GSM Authentication procedure performs subscriber authentication, or selection of the ciphering algorithm, or both. In A/Gb mode it performs in addition the synchronisation of the start of ciphering. Authentication triplets are stored in the SGSN. The MSC/VLR shall not authenticate the MS via the SGSN upon IMSI attach, nor location update, but may authenticate the MS during CS connection establishment. Security-related network functions are described in TS 43.020.
The GSM Authentication procedure is illustrated in Figure 27.
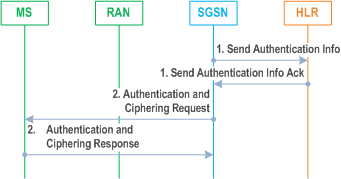
1)
In A/Gb mode, the MS starts ciphering after sending the Authentication and Ciphering Response message as described in clause "Start of Ciphering".
Change of the ciphering algorithm during PS Handover procedure is described in TS 43.129.
In Iu mode, the SGSN and the MS shall generate the UMTS CK and IK from the GSM Kc using the standardised conversion functions specified for this purpose in TS 33.102.
In Iu mode, the start of ciphering is controlled by the security mode procedure described in TS 33.102.
If the SGSN cannot determine the HLR address to establish the Send Authentication Info dialogue, the GSM Authentication of Procedure fails.
If the SGSN does not have a previously stored authentication vector, a Send Authentication Info (IMSI) message is sent to the HLR. The HLR responds with a Send Authentication Info Ack (Authentication Triplets or quintets) message.
2)
The SGSN sends an Authentication and Ciphering Request (RAND, CKSN, Ciphering Algorithm) message to the MS. The MS responds with an Authentication and Ciphering Response (SRES) message.
6.8.1.2 UMTS Authentication procedure p. 106
The UMTS authentication procedure is described in TS 33.102. The UMTS authentication procedure executed from the SGSN performs both the mutual authentication and security keys agreement. Authentication quintets are stored in the SGSN. The MSC/VLR shall not authenticate the MS via the SGSN upon IMSI attach nor upon location update, but may authenticate the MS during CS connection establishment.
The UMTS Authentication procedure is illustrated in Figure 28.
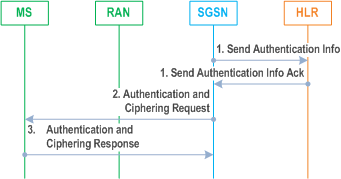
1)
In A/Gb mode, the SGSN and the MS shall generate the Kc from the UMTS CK and IK using the standardised conversion function specified for this purpose in TS 33.102.
In A/Gb mode, the MS starts ciphering after sending the Authentication and Ciphering Response message as described in clause "Start of Ciphering".
In Iu mode, the start of ciphering is controlled by the security mode procedure described in TS 33.102.
If the SGSN cannot determine the HLR address to establish the Send Authentication Info dialogue, the UMTS Authentication Procedure fails.
If the SGSN does not have previously stored UMTS Authentication Vectors (quintets), a Send Authentication Info (IMSI) message is sent to the HLR. Upon receipt of this message, the HLR responds with a Send Authentication Info Ack message including an ordered array of quintets to the SGSN. Each quintet contains RAND, XRES, AUTN, CK, and IK. The generation of quintets in HLR is performed as specified in TS 33.102.
2)
At authentication, the SGSN selects the next in-order quintet and transmits the RAND and AUTN, that belong to this quintet, to the MS in the Authentication and Ciphering Request (RAND, AUTN, KSI) message. The SGSN also selects a Key Set Identifier, KSI, and includes this in the message.
3)
At reception of this message, the USIM in the MS verifies AUTN and, if accepted, the USIM computes the signature of RAND, RES, in accordance with TS 33.102. If the USIM considers the authentication as being successful, the MS returns an Authentication and Ciphering Response (RES) message to the SGSN. During generation of authentication vectors, the USIM in the MS also computes a new Ciphering Key, CK, and a new Integrity Key, IK. These keys are stored together with the KSI until KSI is updated at the next authentication.
If the USIM considers the authentication being unsuccessful, e.g., in case of an authentication synchronisation failure, the MS returns the Authentication and Ciphering Failure message to the SGSN. The actions then taken are described in TS 33.102.
6.8.2 User Identity Confidentiality p. 106
6.8.2.1 User Identity Confidentiality (A/Gb mode) p. 106
A Temporary Logical Link Identity (TLLI) identifies a user in A/Gb mode. The relationship between TLLI and IMSI is known only in the MS and in the SGSN. TLLI is derived from the P-TMSI allocated by the SGSN or built by the MS as described in clause "NSAPI and TLLI for A/Gb mode".
6.8.2.2 User Identity Confidentiality (Iu mode) p. 107
A Radio Network Temporary Identity (RNTI) identifies a user between the MS and an Iu mode RAN. The relationship between RNTI and IMSI is known only in the MS and in the RAN. A P-TMSI identifies a user between the MS and the SGSN. The relationship between P-TMSI and IMSI is known only in the MS and in the SGSN.
6.8.2.3 P-TMSI Signature p. 107
P-TMSI Signature is optionally sent by the SGSN to the MS in Attach Accept and Routeing Area Update Accept messages. If the P-TMSI Signature has been sent by the SGSN to the MS since the current P-TMSI was allocated, then the MS shall include the P-TMSI Signature in the next Routeing Area Update Request, Detach Request, and Attach Request for identification checking purposes. If the P-TMSI Signature was sent, then the SGSN shall compare the P-TMSI Signature sent by the MS with the signature stored in the SGSN. If the values do not match, the SGSN should use the security functions to authenticate the MS. If the values match or if the P-TMSI Signature is missing, the SGSN may use the security functions to authenticate the MS. The P-TMSI Signature parameter has only local significance in the SGSN that allocated the signature.
If the network supports ciphering, the SGSN shall send the P-TMSI Signature ciphered to the MS. Routeing Area Update Request and Attach Request, into which the MS includes the P-TMSI Signature, are not ciphered.
6.8.2.4 P-TMSI Reallocation Procedure p. 107
The SGSN may attempt to reallocate the P-TMSI at any time that the MS is in GERAN/UTRAN PS coverage. The reallocation procedure can be performed by the P-TMSI Reallocation procedure, or it can be included in the Attach or Routeing Area Update procedures. The P-TMSI reallocation during PS Handover procedure is described in TS 43.129.
The P-TMSI Reallocation procedure is illustrated in Figure 29.
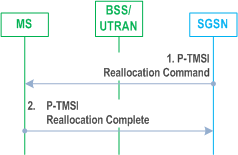
1)
The SGSN sends a P-TMSI Reallocation Command (new P-TMSI, P-TMSI Signature, RAI) message to the MS. P-TMSI Signature is an optional parameter that the MS, if received, shall return to the SGSN in the next Attach and Routeing Area Update procedures.
2)
The MS returns a P-TMSI Reallocation Complete message to the SGSN.
6.8.3 User Data and GMM/SM Signalling Confidentiality p. 107
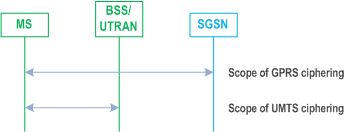
6.8.3.1 Scope of Ciphering p. 107
In A/Gb mode, the scope of ciphering is from the ciphering function in the SGSN to the ciphering function in the MS. Ciphering is done in the LLC layer, and from the perspective of the A/Gb mode MS-BTS radio path, an LLC PDU is transmitted as plain text.
In Iu mode, the scope of ciphering is from the ciphering function in the RAN to the ciphering function in the MS.
6.8.3.2 Ciphering Algorithm p. 108
TS 41.061 contains the requirements for the GPRS Encryption Algorithm (GEA) for A/Gb mode. The A/Gb mode ciphering key Kc is an input to the algorithm. The standard key management procedures for the Kc shall be used.
In Iu mode ciphering is performed with the UMTS Encryption Algorithm (UEA). The Iu mode Ciphering Key CK is an input to the algorithm.
6.8.3.3 Start of Ciphering p. 108
In A/Gb mode, the MS starts ciphering after sending the Authentication and Ciphering Response message. The SGSN starts ciphering when a valid Authentication and Ciphering Response message is received from the MS. In the routeing area update case, if ciphering was used before the routeing area update, and if the authentication procedure is omitted, then the SGSN shall resume ciphering with the same algorithm when a ciphered Routeing Area Update Accept message is sent, and the MS shall resume ciphering when a ciphered Routeing Area Update Accept message is received.
In Iu mode, the start of ciphering is controlled by the security mode procedure described in TS 33.102.
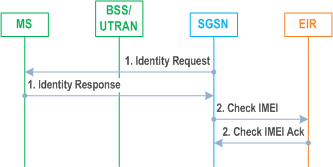
6.8.4 Identity Check Procedures p. 108
The Identity Check procedure is illustrated in Figure 31.
6.8.5 Data Integrity Procedure (Iu mode) p. 108
The Data Integrity procedure is performed between the MS and the RAN. It is applicable only to radio signalling. The Iu mode integrity check is made with the UMTS Integrity Algorithm (UIA). The UMTS Integrity Key IK is an input to the algorithm. The start of the data integrity procedure is controlled by the security mode procedure as described in TS 33.102.