Content for TR 33.824 Word version: 17.0.0
4 Security aspects in the 5G System to enable support of NR Integrated Access and Backhaul
4.1 IAB Architecture
4.2 IAB security architecture
4.3 Existing security mechanisms
...
...
4 Security aspects in the 5G System to enable support of NR Integrated Access and Backhaul p. 8
4.1 IAB Architecture p. 8
This clause aims to provide some brief details of IAB architecture as background to the rest of the analysis in the present document. A more complete description of architecture is covered in TS 38.401.
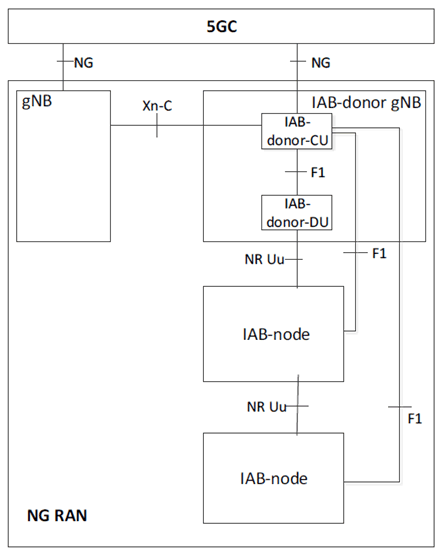
The NG-RAN supports multi-hop backhauling for flexible range extension by the IAB-node connecting to the gNB capable of serving the IAB-nodes via NR Uu, named IAB-donor gNB [4].
4.2 IAB security architecture p. 9
This clause provides the IAB security architecture diagram and lists the groups of related security aspects.
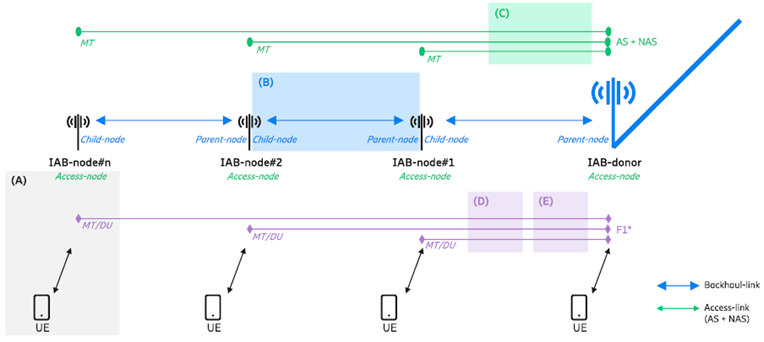
The IAB security architecture is shown in Figure 4.2-1. There are following groups of security aspects:
(A)
Authentication, AS, and NAS security of UE.
(B)
Security of backhaul-link between Child-node and Parent-node.
(C)
Authentication, AS, and NAS security of MT part of IAB-node.
(D)
Security of F1*-C between MT/DU part of IAB-node and IAB-donor.
(E)
Security of F1*-U between MT/DU part of IAB-node and IAB-donor.
4.3 Existing security mechanisms p. 10
It is assumed that the UE is agnostic to the IAB architecture. Therefore, all security mechanisms between the UE and the network (including UE-RAN and UE-CN) are inherited, i.e., remain unchanged, from TS 33.501. However, the present document could study security aspects between the UE and network that are different from TS 33.501, if any.
Some security mechanisms that are directly related to the present document and inherited from TS 33.501 are listed below:
- Authentication procedures between the UE and the CN.
- AS security mechanism between the UE and the RAN. The key hierarchy is reused for the AS keys. The IAB node is acting as the UE and the IAB donor is acting as the gNB in the key hierarchy.
- NAS security mechanism between the UE and the CN. The key hierarchy is reused for the NAS keys. The IAB node is acting as the UE in the key hierarchy.
- Mobility (handovers, RNA update, and mobility registration update) between the UE and the network (RAN/CN).
- The role of the 5G Core in the IAB architecture is unchanged in the key hierarchy compared to 5GS Rel-15.