Content for TR 33.824 Word version: 17.0.0
6.3 Solutions for protection of the F1*-U/C interfaces (wireless backhaul links)
6.3.1 Solution #3.1: F1 interface security for IAB
6.3.2 Solution #3.2: F1 security context establishment
6.3 Solutions for protection of the F1*-U/C interfaces (wireless backhaul links) p. 19
6.3.1 Solution #3.1: F1 interface security for IAB p. 19
6.3.1.1 Introduction p. 19
This solution addresses the key issue #3.1: F1 interface security for IAB.
6.3.1.2 Solution details p. 19
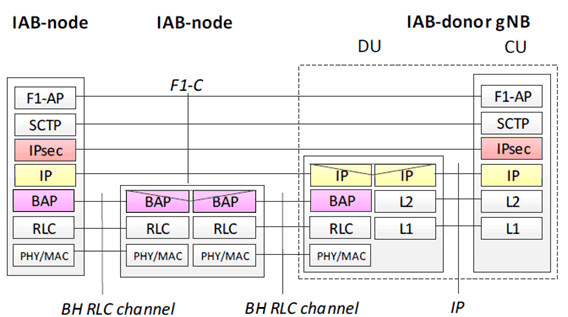
The control plane signalling between the IAB node and the IAB-donor node is confidentiality, integrity and replay protected in an end-to-end manner in the same way as the wireline fronthaul control (F1-C) protection using IPsec ESP and IKEv2 as specified in TS 33.501. Alternatively, the F1-C interface could be protected using DTLS. Figure 6.3.2-1 shows the protocol stack when IPsec is used for F1-C protection.
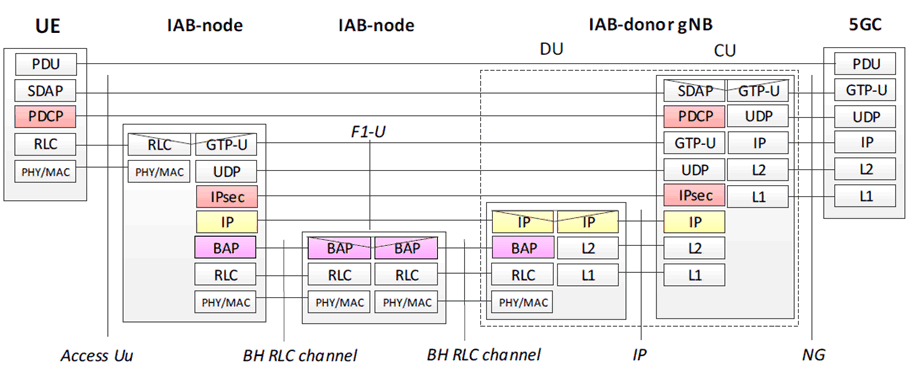
The user plane traffic between the IAB node and the IAB-donor node is confidentiality, integrity and replay protected in an end-to-end manner in the same way as the wireline fronthaul user plane (F1-U) protection specified in TS 33.501. F1-U is used to transport traffic between UE and CU that is protected in PDCP layer as shown in Figure 6.3.1.2-2.
6.3.1.3 Evaluation p. 20
The solution provides confidentiality and integrity protection of both control plane (i.e., F1-C) and user plane (i.e., F1-U) interfaces between the IAB node and IAB-donor, in an end-to-end manner. Therefore, the solution fulfils the potential security requirements of KI #3.1.
Furthermore, the solution allows to reuse the F1 security protocols for the wireline F1 interface as specified in TS 33.501. This simplifies the handling of the security in an environment that supports both wireline F1 interface and wireless F1 interface as the same security protocol is used for both interfaces.
6.3.2 Solution #3.2: F1 security context establishment p. 20
6.3.2.1 Introduction p. 20
This solution addresses the F1 security establishment requirements for IAB in key issue #3.1.
6.3.2.2 Solution details p. 21
IAB integration procedure consists of 3 phases [3].
- IAB-MT setup: The IAB-MT performs registration to the network as a UE and consequently, the AS security is established between the IAB-MT and IAB donor.
- Backhaul RLC channel establishment and routing update: If the IAB-MT is authorized to run as an IAB node based on the CN indication to the IAB donor, the backhaul RLC channels and the BAP layer are established and configured using the secure RRC signalling to support routing between the IAB node and the IAB donor.
- IAB-DU setup: F1 security establishment for IAB is performed over the RLC channel using the procedure specified in clause 9.8.2 of TS 33.501.
6.3.2.3 Evaluation p. 21
This solution supports a mechanism to fulfil the security requirements of key issue #3.1.
This solution supports a unified F1 security context establishment procedure for both wireline and wireless F1 interfaces.