Content for TS 33.102 Word version: 18.0.0
6.8 Interoperation and handover between UMTS and GSM
6.8.1 Authentication and key agreement of UMTS subscribers
6.8.1.1 General
6.8.1.2 R99+ HLR/AuC
6.8.1.3 R99+ VLR/SGSN
6.8.1.4 R99+ ME
6.8.1.5 USIM
6.8.2 Authentication and key agreement for GSM subscribers
6.8.2.1 General
6.8.2.2 R99+ HLR/AuC
6.8.2.3 VLR/SGSN
6.8.2.4 R99+ ME
6.8.3 Distribution and use of authentication data between VLRs/SGSNs
...
...
6.8 Interoperation and handover between UMTS and GSM p. 42
6.8.1 Authentication and key agreement of UMTS subscribers p. 42
6.8.1.1 General p. 42
For UMTS subscribers, authentication and key agreement will be performed as follows:
- UMTS AKA shall be applied when the user is attached to a UTRAN.
- UMTS AKA shall be applied when the user is attached to a GSM BSS, in case the user has a ME capable of UMTS AKA and also the VLR/SGSN is R99+. In this case, the 64-bit GSM cipher key Kc is derived from the UMTS cipher/integrity keys CK and IK, by the VLR/SGSN on the network side and by the USIM on the user side.The 128-bit GSM cipher key Kc 128 is derived from the UMTS cipher/integrity keys CK and IK, by the VLR/SGSN on the network side and by the ME on the user side if needed to support 128-bit ciphering algorithms in GSM as described in subclause 6.3.3 of this specification.
- GSM AKA shall be applied when the user is attached to a GSM BSS, in case the user has a ME not capable of UMTS AKA. In this case, the GSM user response SRES and the 64-bit GSM cipher key Kc are derived from the UMTS user response RES and the UMTS cipher/integrity keys CK and IK. A R98- VLR/SGSN uses the stored Kc and RES and a R99+ VLR/SGSN derives the SRES from RES and Kc from CK, IK.
- GSM AKA shall be applied when the user is attached to a GSM BSS, in case the VLR/SGSN is R98-. In this case, the USIM derives the GSM user response SRES and the GSM cipher key Kc from the UMTS user response RES and the UMTS cipher/integrity keys CK, IK.
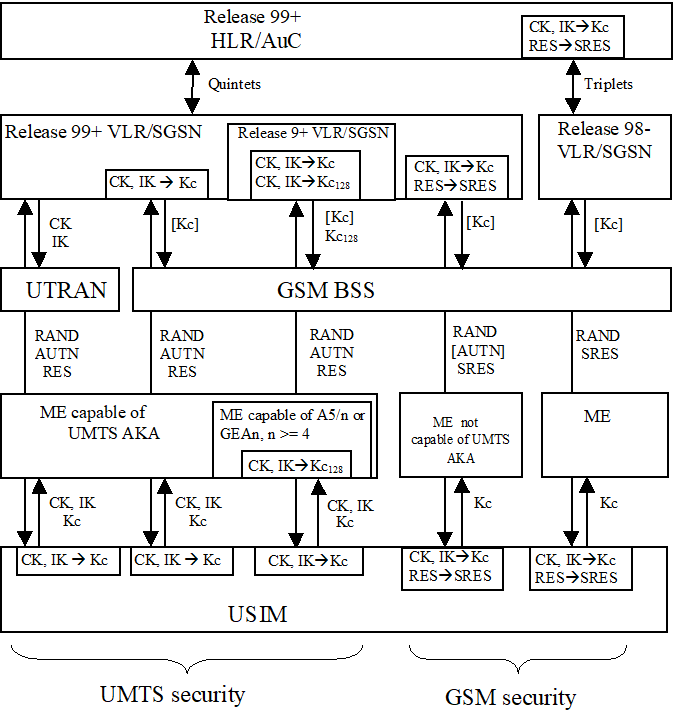
Note that the UMTS parameters RAND, AUTN and RES are sent transparently through the UTRAN or GSM BSS and that the GSM parameters RAND and SRES are sent transparently through the GSM BSS.
In case of a GSM BSS, ciphering is applied in the GSM BSS for services delivered via the MSC/VLR, and by the SGSN for services delivered via the SGSN. In the latter case the GSM cipher keys Kc or Kc 128 are not sent to the GSM BSS.
In case of a UTRAN, ciphering and integrity are always applied in the RNC, and the UMTS cipher/integrity keys CK an IK are always sent to the RNC.
6.8.1.2 R99+ HLR/AuC p. 43
Upon receipt of an authentication data request from a R99+ VLR/SGSN for a UMTS subscriber, a R99+ HLR/AuC shall send quintets, generated as specified in 6.3.
Upon receipt of an authentication data request from a R98- VLR/SGSN for a UMTS subscriber, a R99+ HLR/AuC shall send triplets, derived from quintets using the following conversion functions:
- c1: RAND[GSM] = RAND
- c2: SRES[GSM] = XRES*1 xor XRES*2 xor XRES*3 xor XRES*4
- c3: Kc[GSM] = CK1 xor CK2 xor IK1 xor IK2
6.8.1.3 R99+ VLR/SGSN p. 44
The AKA procedure will depend on the terminal capabilities, as follows:
UMTS subscriber with R99+ ME
When the user has R99+ ME, the VLR/SGSN shall send the ME a UMTS authentication challenge (i.e. RAND and AUTN) using a quintet that is either:
When the user has R98- ME, the R99+ VLR/SGSN sends the ME a GSM authentication challenge using a triplet that is either:
- retrieved from the local database,
- provided by the HLR/AuC, or
- provided by the previously visited R99+ VLR/SGSN.
- UMTS AKA results in the establishment of a UMTS security context; the UMTS cipher/integrity keys CK and IK and the key set identifier KSI are stored in theVLR/SGSN.
- When the user is attached to a UTRAN, the UMTS cipher/integrity keys are sent to the RNC, where the cipher/integrity algorithms are allocated.
- When the user is attached to a GSM BSS, UMTS AKA is followed by the derivation of the GSM cipher keys Kc (and Kc 128 when needed)from the UMTS cipher/integrity keys. When the user receives service from an MSC/VLR, the derived cipher keys Kc (and Kc 128 when needed) are then sent to the BSC (and forwarded to the BTS). When the user receives service from an SGSN, the derived cipher key Kc or Kc 128 applied in the SGSN itself.
- UMTS authentication and key freshness is always provided to UMTS subscribers with R99+ ME independently of the radio access network.
- GSM AKA results in the establishment of a GSM security context; the 64-bit GSM cipher key Kc and the cipher key sequence number CKSN are stored in the VLR/SGSN.
-
derived by means of the conversion functions c2 and c3 in the R99+ VLR/SGSN from a quintet that is:
- retrieved from the local database,
- provided by the HLR/AuC, or
- provided by the previously visited R99+ VLR/SGSN, or
- provided as a triplet by the previously visited VLR/SGSN.
6.8.1.4 R99+ ME p. 45
Release 99+ ME that has UTRAN radio capability shall support the USIM-ME interface as specified in TS 31.102.
Rel4- ME that has no UTRAN radio capabilities may support the USIM-ME interface as specified in TS 31.102.
Rel5+ ME that has no UTRAN radio capabilities shall support the USIM-ME interface as specified in TS 31.102.
A ME capable of UMTS AKA with a USIM active and attached to a UTRAN shall only participate in UMTS AKA and shall not participate in GSM AKA.
A ME capable of UMTS AKA with a USIM active and attached to a GSM BSS shall participate in UMTS AKA and may participate in GSM AKA. Participation in GSM AKA is required to allow registration in a R98- VLR/SGSN.
However, the use of GSM AKA in the MS shall be disabled on a particular visited network if instructed to do so by the USIM application. The mechanism is based on an EF 'Disabled Authentications' in the USIM application containing the unauthorized authentication methods per visited network. If the EF 'Disabled Authentications' is present and active, then the authentication methods marked as disabled shall not be used by the MS in the corresponding visited network. The disabled authentication method may be defined on a global, per country or per network basis. The relevant file in the USIM application is managed by the home operator based on information supplied to the home operator by the visited network.
A ME that not capable of UMTS AKA with a USIM active can only participate in GSM AKA.
The execution of UMTS AKA results in the establishment of a UMTS security context; the UMTS cipher/integrity keys CK and IK and the key set identifier KSI are passed to the ME. If the USIM supports conversion function c3 and/or GSM AKA, the ME shall also receive a 64-bit GSM cipher key Kc derived at the USIM.
If the ME supports 128-bit ciphering algorithms A5 and/or GEA for GSM, the ME shall also support the key derivation function for Kc 128 as specified in Annex B.5. The execution of GSM AKA results in the establishment of a GSM security context; the 64-bit GSM cipher key Kc and the cipher key sequence number CKSN are stored in the ME.
6.8.1.5 USIM p. 45
The USIM shall support UMTS AKA and may support backwards compatibility with the GSM system, which consists of:
Feature 1:
64-bit GSM cipher key derivation (conversion function c3) to access GSM BSS attached to a R99+ VLR/SGSN using a dual-mode R99+ ME;
Feature 2:
GSM AKA to access the GSM BSS attached to a R98- VLR/SGSN or when using ME not capable of UMTS AKA;
Feature 3:
SIM-ME interface (GSM 11.11) to operate within ME not capable of UMTS AKA.
When the ME provides the USIM with RAND and AUTN, UMTS AKA shall be executed. If the verification of AUTN is successful, the USIM shall respond to the ME with the UMTS user response RES and the UMTS cipher/integrity keys CK and IK. The ME shall store CK and IK as current security context data on the USIM. If the USIM supports access to 64-bit GSM cipher key derivation (feature 1), the USIM shall also derive the 64-bit GSM cipher key Kc from the UMTS cipher/integrity keys CK and IK using conversion function c3 and send the derived Kc to the ME. In case the verification of AUTN is not successful, the USIM shall respond with an appropriate error indication to the ME.
When the ME provides the USIM with only RAND, and the USIM supports GSM AKA (Feature 2), GSM AKA shall be executed. The USIM first computes the UMTS user response RES and the UMTS cipher/integrity keys CK and IK. The USIM then derives the GSM user response SRES and the 64-bit GSM cipher key Kc using the conversion functions c2 and c3 and send the GSM user response SRES and the 64-bit GSM cipher key Kc to the ME. The ME shall store the 64-bit GSM cipher key Kc as the current security context on the USIM.
In case the USIM does not support 64-bit GSM cipher key derivation (Feature 1) or GSM AKA (Feature 2), the ME shall be informed. An ME with a USIM that does not support GSM cipher key derivation (Feature 1) shall not perform the GSM cipher key derivation (conversion function c3) in the ME and therefore cannot operate in any GSM BSS with 64-bit key ciphering enabled. An ME with a USIM that does not support GSM AKA (Feature 2) cannot operate under a R98- VLR/SGSN. A USIM that does not support GSM AKA (Feature 2) cannot work within a ME that is not capable of UMTS AKA.
6.8.2 Authentication and key agreement for GSM subscribers p. 46
6.8.2.1 General p. 46
For GSM subscribers, GSM AKA shall always be used.
The execution of the GSM AKA results in the establishment of a GSM security context between the user and the serving network domain to which the VLR/SGSN belongs. The user needs to separately establish a security context with each serving network domain.
When in a UTRAN, the UMTS cipher/integrity keys CK and IK are derived from the GSM cipher key Kc by the ME and the VLR/SGSN, both R99+ entities.
Figure 19 shows the different scenarios that can occur with GSM subscribers using either R98- or R99+ ME in a mixed network architecture.
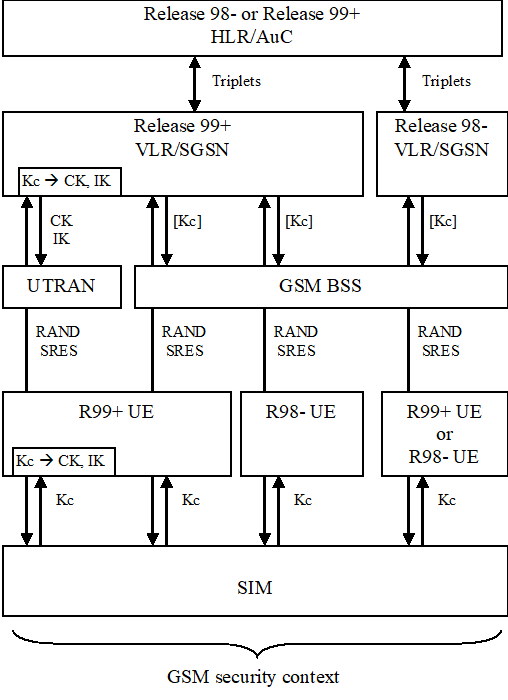
Note that the GSM parameters RAND and RES are sent transparently through the UTRAN or GSM BSS.
In case of a GSM BSS, ciphering is applied in the GSM BSS for services delivered via the MSC/VLR, and by the SGSN for services delivered via the SGSN. In the latter case the GSM cipher key Kc is not sent to the GSM BSS.
In case of a UTRAN, ciphering is always applied in the RNC, and the UMTS cipher/integrity keys CK an IK are always sent to the RNC.
6.8.2.2 R99+ HLR/AuC p. 47
Upon receipt of an authentication data request for a GSM subscriber, a R99+ HLR/AuC shall send triplets generated as specified in TS 43.020.
6.8.2.3 VLR/SGSN p. 47
The R99+ VLR/SGSN shall perform GSM AKA using a triplet that is either:
- retrieved from the local database,
- provided by the HLR/AuC, or
- provided by the previously visited VLR/SGSN.
- c4: CK[UMTS] = Kc || Kc;
- c5: IK[UMTS] = Kc1 xor Kc2 || Kc || Kc1 xor Kc2;
6.8.2.4 R99+ ME p. 48
R99+ ME with a SIM inserted, shall participate only in GSM AKA.
GSM AKA results in the establishment of a GSM security context; the GSM cipher key Kc and the cipher key sequence number CKSN are stored in the ME.
When the user is attached to a UTRAN, R99+ ME shall derive the UMTS cipher/integrity keys CK and IK from the GSM cipher key Kc using the conversion functions c4 and c5. The ME shall handle the STARTCS and STARTPS as described in clause 6.4.8 with the exception that the START values shall be stored in non-volatile memory on the ME rather than on the GSM SIM. If a different SIM is inserted then the ME shall delete the GSM cipher keys for the PS and CS domain (Kc), the derived UMTS cipher/integrity keys (CK and IK) for the PS and CS domain, and reset the START values to zero. The ME shall then trigger a new authentication and key agreement at the next connection establishment by indicating to the network that no valid keys are available for use using the procedure described in clause 6.4.4.
When the user is attached to a UTRAN, a R99+ ME with a SIM inserted shall use a default value of all ones for maximum value of STARTCS or STARTPS. The ME shall handle the maximum value of STARTCS or STARTPS as described in clause 6.4.3 with the exception that the maximum value of STARTCS or STARTPS is stored on the ME rather than on the GSM SIM.
6.8.3 Distribution and use of authentication data between VLRs/SGSNs p. 48
The distribution of authentication data (unused authentication vectors and/or current security context data) between R99+ VLRs/SGSNs of the same service network domain is performed according to chapter 6.3.4. The following four cases are distinguished related to the distribution of authentication data between VLRs/SGSNs (of the same or different releases). Conditions for the distribution of such data and for its use when received at VLRn/SGSNn are indicated for each case:
-
R99+ VLR/SGSN to R99+ VLR/SGSN
UMTS and GSM authentication vectors can be distributed between R99+ VLRs/SGSNs. Note that originally all authentication vectors (quintets for UMTS subscribers and triplets for GSM subscribers) are provided by the HLR/AuC.
Current security context data can be distributed between R99+ VLRs/SGSNs. VLRn/SGSNn shall not use current security context data received from VLRo/SGSNo to authenticate the subscriber using local authentication in the following cases:
- Security context to be established at VLRn/SGSNn requires a different set of keys than the one currently in use at VLRo/SGSNo. This change of security context is caused by a change of ME release (R'99 ME ↔ R'98 ME) when the user registers at VLRn/SGSNn.
- Authentication data from VLRo includes 64-bit Kc+CKSN but no unused AVs and the subscriber has a R'99 ME (under GSM BSS or UTRAN). In this situation, VLRn have no indication of whether the subscriber is GSM or UMTS and it is not able to decide whether the 64-bit Kc received can be used (in case the subscriber were a GSM subscriber).
- R98- VLR/SGSN to R98- VLR/SGSN Only triplets can be distributed between R98- VLRs/SGSNs. Note that originally for GSM subscribers, triplets are generated by HLR/AuC and for UMTS subscribers, they are derived from UMTS authentication vectors by R99+ HLR/AuC. UMTS AKA is not supported and only GSM security context can be established by a R98- VLR/SGSN. R98- VLRs are not prepared to distribute current security context data. Since only GSM security context can be established under R98- SGSNs, security context data can be distributed and used between R98- SGSNs.
- R99+ VLR/SGSN to R98- VLR/SGSN R99+ VLR/SGSN can distribute to a new R98- VLR/SGSN triplets originally provided by HLR/AuC for GSM subscribers or can derive triplets from stored quintets originally provided by R99+ HLR/AuC for UMTS subscribers. Note that R98- VLR/SGSN can only establish GSM security context. R99+ VLRs shall not distribute current security context data to R98- VLRs. Since R98- SGSNs are only prepared to handle GSM security context data, R99+ SGSNs shall only distribute GSM security context data (64-bit Kc, CKSN) to R98- SGSNs.
- R98- VLR/SGSN to R99+ VLR/SGSN. In order to not establish a GSM security context for a UMTS subscriber, triplets provided by a R98- VLR/SGSN can only be used by a R99+ VLR/SGSN to establish a GSM security context under GSM-BSS with a R98- ME. In all other cases, R99+ VLR/SGSN shall request fresh AVs (either triplets or quintets) to HE. In the event, the R99+ VLR/SGSN receives quintets, it shall discard the triplets provided by the R98- VLR/SGSN. R98- VLRs are not prepared to distribute current security context data. R98- SGSNs can distribute GSM security context data only. The use of this information at R99+ SGSNn shall be performed according to the conditions stated in a).