Content for TS 33.105 Word version: 17.0.0
5 Functional algorithm requirements
5.1 Authentication and key agreement
5.1.1 Overview
5.1.2 Use
5.1.3 Allocation
5.1.4 Extent of standardisation
5.1.5 Implementation and operational considerations
5.1.6 Type of algorithm
5.1.7 Interface
...
...
5 Functional algorithm requirements p. 8
5.1 Authentication and key agreement p. 8
5.1.1 Overview p. 8
The mechanism for authentication and key agreement described in clause 6.3 of TS 33.102 requires the following cryptographic functions:
f0
the random challenge generating function;
f1
the network authentication function;
f1*
the re-synchronisation message authentication function;
f2
the user authentication function;
f3
the cipher key derivation function;
f4
the integrity key derivation function;
f5
the anonymity key derivation function for normal operation;
f5*
the anonymity key derivation function for re-synchronisation.
5.1.1.1 Generation of quintets in the AuC p. 8
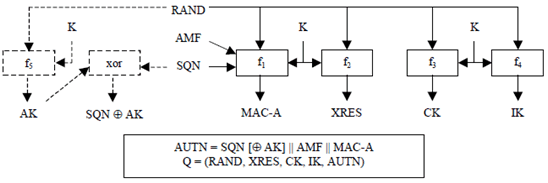
To generate a quintet the HLR/AuC:
- computes a message authentication code for authentication MAC-A = f1K(SQN || RAND || AMF), an expected response XRES = f2K (RAND), a cipher key CK = f3K (RAND) and an integrity key IK = f4K (RAND) where f4 is a key generating function.
- If SQN is to be concealed, in addition the HLR/AuC computes an anonymity key AK = f5K (RAND) and computes the concealed sequence number SQN ⊕ AK = SQN xor AK. Concealment of the sequence number is optional.
- Finally, the HLR/AuC assembles the authentication token AUTN = SQN [* AK] || AMF || MAC-A and the quintet Q = (RAND, XRES, CK, IK, AUTN).
5.1.1.2 Authentication and key derivation in the USIM p. 9
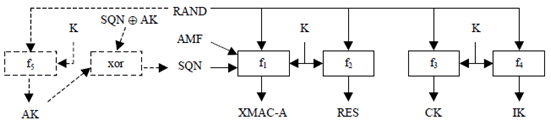
Upon receipt of a (RAND, AUTN) pair the USIM acts as follows:
- If the sequence number is concealed, the USIM computes the anonymity key AK = f5K(RAND) and retrieves the unconcealed sequence number SQN = (SQN * AK) xor AK. The USIM computes XMAC-A = f1K (SQN || RAND || AMF), the response RES = f2K(RAND), the cipher key CK = f3K (RAND) and the integrity key IK = f4K (RAND).
5.1.1.3 Generation of re-synchronisation token in the USIM p. 9
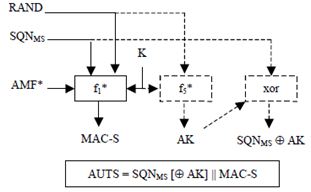
Upon the assertion of a synchronisation failure, the USIM generates a re-synchronisation token as follows:
- The USIM computes MAC-S = f1*K(SQNMS || RAND || AMF*), whereby AMF* is a default value for AMF used in re-synchronisation.
- If SQNMS is to be concealed with an anonymity key AK, the USIM computes AK = f5*K(RAND), and the concealed counter value is then computed as SQNMS ⊕ AK.
- The re-synchronisation token is constructed as AUTS = SQNMS [⊕ AK] || MAC-S.
5.1.1.4 Re-synchronisation in the HLR/AuC p. 10
Upon receipt of an indication of synchronisation failure and a (AUTS, RAND) pair, the HLR/AuC may perform the following cryptographic functions:
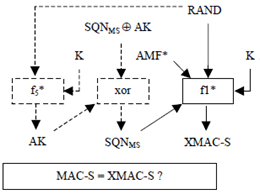
- If SQNMS is concealed with an anonymity key AK, the HLR/AuC computes AK = f5*K(RAND)and retrieves the unconcealed counter value as SQNMS = (SQNMS ⊕ AK) xor AK.
- If SQN generated from SQNHE would not be acceptable, then the HLR/AuC computes XMAC-S = f1*K(SQNMS || RAND || AMF*), whereby AMF* is a default value for AMF used in re-synchronisation.
5.1.2 Use p. 10
The functions f0—f5 shall only be used to provide mutual entity authentication between USIM and AuC, derive keys to protect user and signalling data transmitted over the radio access link and conceal the sequence number to protect user identity confidentiality. The function f1* shall only be used to provide data origin authentication for the synchronisation failure information sent by the USIM to the AuC. The function f5* shall only be used to provide user identity confidentiality during re-synchronisation.
5.1.3 Allocation p. 10
The functions f1—f5, f1* and f5* are allocated to the Authentication Centre (AuC) and the USIM. The function f0 is allocated to the AuC.
5.1.4 Extent of standardisation p. 11
The functions f0—f5, f1* and f5* are proprietary to the home environment. Examples of the functions f1, f1* and f2 are CBC-MACs or H-MACs [3].
5.1.5 Implementation and operational considerations p. 11
The functions f1—f5, f1* and f5* shall be designed so that they can be implemented on an IC card equipped with a 8-bit microprocessor running at 3 MHz with 8 kbyte ROM and 300byte RAM and produce AK, XMAC-A, RES, CK and IK in less than 500 ms execution time.
5.1.6 Type of algorithm p. 11
5.1.6.1 f0 p. 11
f0: the random challenge generating function
f0: (internal state) → RAND
f0 should be (pseudo) random number generating function.
5.1.6.2 f1 p. 11
f1: the network authentication function
f1: (K; SQN, RAND, AMF) → MAC-A (or XMAC-A)
f1 should be a MAC function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND, SQN, AMF and MAC-A (or XMAC-A).
5.1.6.3 f1* p. 11
f1*: the re-synchronisation message authentication function
f1*: (K; SQN, RAND, AMF) → MAC-S (or XMAC-S)
f1 should be a MAC function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND, SQN, AMF and MAC-S (or XMAC-S).
5.1.6.4 f2 p. 11
f2: the user authentication function
f2: (K; RAND) → RES (or XRES)
f2 should be a MAC function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND and RES (or XRES).
5.1.6.5 f3 p. 11
f3: the cipher key derivation function
f3: (K; RAND) → CK
f3 should be a key derivation function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND and CK.
5.1.6.6 f4 p. 12
f4: the integrity key derivation function
f4: (K; RAND) → IK
f4 should be a key derivation function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND and IK.
5.1.6.7 f5 p. 12
f5: the anonymity key derivation function for normal operation
f5: (K; RAND) → AK
f5 should be a key derivation function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND and AK.
The use of f5 is optional.
5.1.6.8 f5* p. 12
f5*: the anonymity key derivation function for re-synchronisation
f5*: (K; RAND) → AK
f5* should be a key derivation function. In particular, it shall be computationally infeasible to derive K from knowledge of RAND and AK.
The use of f5* is optional.
5.1.7 Interface p. 12
5.1.7.1 K p. 12
K: the subscriber authentication key
K[0], K[1], …, K[127]
The length of K is 128 bits. The subscriber authentication key K is a long term secret key stored in the USIM and the AuC.
5.1.7.2 RAND p. 12
RAND: the random challenge
RAND[0], RAND[1], …, RAND[127]
The length of RAND is 128 bits.
5.1.7.3 SQN p. 12
SQN: the sequence number
SQN[0], SQN[1], …, SQN[47]
The length of SQN is 48 bits. The AuC should include a fresh sequence number in each authentication token. The verification of the freshness of the sequence number by the USIM constitutes to entity authentication of the network to the user.
5.1.7.4 AMF p. 13
AMF: the authentication management field
AMF[0], AMF[1], …, AMF[15]
The length of AMF is 16 bits. The use of AMF is not standardised. Example uses of the AMF are provided in annex F of TS 33.102.
5.1.7.6 MAC-A (equivalent for XMAC-A) p. 13
MAC-A: the message authentication code used for authentication of the network to the user
MAC-A[0], MAC-A[1], …, MAC-A[63]
The length of MAC-A is 64 bits. MAC-A authenticates the data integrity and the data origin of RAND, SQN and AMF. The verification of MAC-A by the USIM constitutes to entity authentication of the network to the user.
5.1.7.7 MAC-S (equivalent for XMAC-S) p. 13
MAC-S: the message authentication code used to provide data origin authentication for the synchronisation failure information sent by the USIM to the AuC.
MAC-S[0], MAC-S[1], …, MAC-S[63]
The length of MAC-S is 64 bits. MAC-S authenticates the data integrity and the data origin of RAND, SQN and AMF. MAC-S is generated by the USIM and verified by the AuC.
5.1.7.8 RES (or XRES) p. 13
RES: the user response
RES[0], RES[1], …, RES[n 1]
The length n of RES and XRES is at most 128 bits and at least 32 bits, and shall be a multiple of 8 bits. RES and XRES constitute to entity authentication of the user to the network.
5.1.7.9 CK p. 13
CK: the cipher key
CK[0], CK[1], …, CK[127]
The length of CK is 128 bits. In case the effective key length should need to be made smaller than 128 bits, the most significant bits of CK shall carry the effective key information, whereas the remaining, least significant bits shall be set zero.
5.1.7.10 IK p. 13
IK: the integrity key
IK[0], IK[1], …, IK[127]
The length of IK is 128 bits. In case the effective key length should need to be made smaller than 128 bits, the most significant bits of IK shall carry the effective key information, whereas the remaining, least significant bits shall be set zero.
5.1.7.11 AK p. 14
AK: the anonymity key
AK[0], AK[1], …, AK[47]
The length of AK is 48 bits. It equals the length of SQN.