Content for TS 33.105 Word version: 17.0.0
5.3 Data integrity
5.3.1 Overview
5.3.2 Use
5.3.3 Allocation
5.3.4 Extent of standardisation
5.3.5 Implementation and operational considerations
5.3.6 Type of algorithm
5.3.7 Interface
5.3 Data integrity p. 18
5.3.1 Overview p. 18
The mechanism for data integrity of signalling data that is described in clause 6.6 of TS 33.102 requires the following cryptographic function:
f9 UMTS integrity algorithm.
Figure 6 illustrates the use of the function f9 to derive a MAC-I from a signalling message.
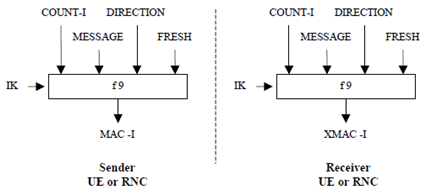
The input parameters to the algorithm are the Integrity Key (IK), a time dependent input (COUNT-I), a random value generated by the network side (FRESH), the direction bit (DIRECTION) and the signalling data (MESSAGE). Based on these input parameters the user computes with the function f9 the message authentication code for data integrity (MAC-I) which is appended to the message when sent over the radio access link. The receiver computes XMAC-I on the messages received in the same way as the sender computed MAC-I on the message sent.
5.3.2 Use p. 18
The MAC function f9 shall be used to authenticate the data integrity and data origin of signalling data transmitted between UE and RNC.
5.3.3 Allocation p. 18
The MAC function f9 is allocated to the UE and the RNC.
Integrity protection shall be applied at the RRC layer.
5.3.4 Extent of standardisation p. 18
The function f9 is fully standardized.
5.3.5 Implementation and operational considerations p. 18
The algorithm should be designed to accommodate a range of implementation options including hardware and software implementations.
5.3.6 Type of algorithm p. 18
The function f9 shall be a MAC function.
5.3.7 Interface p. 19
5.3.7.1 IK p. 19
IK: the integrity key
IK[0], IK[1], …, IK[127]
The length of IK is 128 bits.
5.3.7.2 COUNT-I p. 19
COUNT-I: a frame dependent input.
COUNT-I[0], COUNT-I[1], …, COUNT-I[31]
The length of COUNT-I is 32 bits.
The input parameter COUNT-I protects against replay during a connection. It is a value incremented by one for each integrity protected message. COUNT-I consists of two parts: the HYPERFRAME NUMBER (HFN) as the most significant part and a RRC Sequence Number as the least significant part. The initial value of the hyperframe number is sent by the user to the network at connection set-up. The user stores the greatest used hyperframe number from the previous connection and increments it by one. In this way the user is assured that no COUNT-I value is re-used (by the network) with the same integrity key.
5.3.7.3 FRESH p. 19
FRESH: a random number generated by the RNC.
FRESH[0], FRESH[1], …, FRESH[31]
The length of FRESH is 32 bits.
The same integrity key may be used for several consecutive connections. This FRESH value is an input to the algorithm in order to assure the network side that the user is not replaying old MAC-Is.
5.3.7.4 MESSAGE p. 19
MESSAGE: the signalling data.
MESSAGE[0], MESSAGE[1], …, MESSAGE[X-1]
The length of MESSAGE is X.
5.3.7.5 DIRECTION p. 19
DIRECTION: the direction of transmission of signalling messages (user to network or network to users).
DIRECTION[0]
The length of DIRECTION is 1 bit.
The same integrity key may be used for uplink and downlink channels simultaneously associated with a UE.
The value of the DIRECTION is 0 for messages from UE to RNC and 1 for messages from RNC to UE.
5.3.7.6 MAC-I (and equivalently XMAC-I) p. 19
MAC-I: the message authentication code for data integrity authentication
MAC-I[0], MAC-I[1], …, MAC-I[31]
The length of MAC-I is 32 bits.