Content for TS 22.259 Word version: 18.0.1
5 PNE networks
5.1 General description
5.2 Personal area network management
5.3 PNE redirecting application
5.4 PN access control for PNE networks
...
...
5 PNE networks p. 12
5.1 General description p. 12
PNE Networks enable functions for the management and direct accessibility of the physically separated components of a UE, i.e. TEs and MEs..
PNE Network functions comprise the management and communication of these PNEs within a PN as well as the extension of the PN UE Redirecting application and the PN access control function to include the redirection to UE and PAN components.
5.2 Personal area network management p. 12
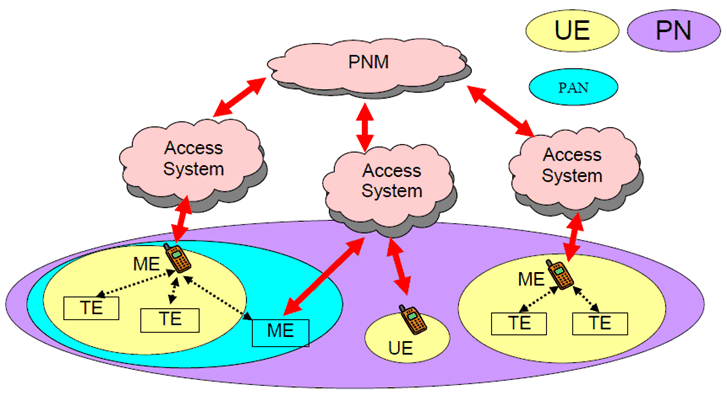
Service requirements cover the management of UE(s), as well as UE components and TE(s), ME(s) or MT(s) and belonging to the same PAN(s) (see Figure 2).
A UE including a USIM, can comprise physically separated TEs and can also have connections with other MTs or MEs (e.g., a PDA, music player, laptop, camera, headset, etc.). The devices are connected through short-range wired or wireless connections (when they are in close proximity) and form a small network, called a PAN (Personal Area Network). The owner of the PNE that holds the USIM controls the PAN.
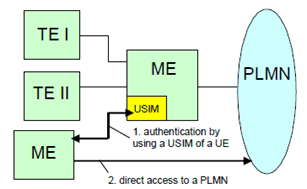
PNEs of a PAN without / not requiring a USIM, may have the need to access services provided by the PLMN or to communicate with another entity through the PLMN. In this case PNEs must be authenticated and authorized by using the USIM associated with the PLMN (i.e., a single USIM authority shall be shared by all the PNEs of the PAN that access services provided by the PLMN).
For managing a PAN means are required to identify a particular PNE within a PAN. The PNE identifiers enable connections between selected PNEs and directing of terminating services to a particular PNE.
Thus PNM identifiers are divided into subscriber identities and PNE identities. 3GPP private subscriber identifiers are the unique IMSI and the unique IMS Private User Identies stored in USIM and ISIM. The subscriber identities are used, for example, for registration, authorization, administration, and accounting purposes in the network. The PNE Identifiers are used to identify devices within a PN and may be used, for example, for blacklist and Device Management purposes. When the PNE is a ME, the IMEI should be reused as PNE identifier unless for security reasons or other reasons this is not feasible. In contrast to MEs the PNE identifiers of TEs are PNM-specific and have little network security relevance as TE have no own radio access means.
Annex A.3 shows two use cases where users access a PLMN from their PANs.
The PN shall support the combination and separation of PANs.
5.2.1 Personal area network requirements p. 13
- The PN-User shall be able to control which PNEs (i.e. TEs, MTs and MEs) are part of a PAN via MMI procedures.
- A user may set-up more than one PAN within a PN.
- The PN-User shall be able to register and deregister PNEs that can be used in a PAN.
- The PN-User shall be able to activate and deactivate the PNEs registered to a PAN.
- A PAN uses exactly one active USIM for authentication. Hence a PAN contains exactly one 3GPP UE.
- In case of only one ME within the PAN the PAN reduces to a 3GPP UE and shall behave as such.
- The PNE Identifier of MEs shall be the IMEI. For TEs it shall be possible to allocate PNM-specific PNE identifiers.
- PNM-specific PNE Identifiers should only be required for PNM-internal purposes but should be harmonized with other optional device identifiers (i.e. Personal ME Identifier in CSI [11]).
- PNM-specific PNE Identifiers shall not be used for routing purposes in the network except PN-internal forwarding to a particular PNE within a PAN.
- PNE Identifiers shall be unique within a PN. Procedures are needed to avoid that PNEs of one PN have the same PNE Identifier.
- It shall not be necessary to store PNE Identifiers in TEs. Instead PNE identities should be managed by a PAN device responsible for processing PAN Management functions.
- It shall be possible to simultaneously access a PLMN via multiple access systems. For example, the user might use PNE1 for data services (internet access) together with PNE2 on a PLMN for a speech call.
- The PN shall support the combination of two or more PANs into one PAN when they are in close proximity. In this case a UE shall be designated for the new PAN. Other UEs who participate in the combination shall be deactivated and hence act as MEs in the new PAN.
- The PN shall support the separation of PAN under specific conditions. In case that there is no active UE among the separated devices, a ME with a USIM shall be designated and activated as UE for the new PAN.
- The PN shall be able to update registration information of PNEs that participate in the combination or separation of PANs.
5.2.2 Usability requirements of personal area network management p. 14
The following PAN Management procedures shall be supported by PAN in a user friendly and secure manner:
- Authentication and authorization of PNEs in a PAN
- Registration of PNEs in a PAN
- Deregistration of PNEs in a PAN
- Activation of PNEs in a PAN
- Deactivation of PNEs in a PAN
- Management of PNE identities within a PAN
- Registration update of PNEs in a PAN
- Combination management of PAN
- Separation management of PAN
- Capability announcement of PNEs in a PAN
5.2.3 Security p. 14
In order to maintain security between a PAN and a PLMN, MTs or MEs providing direct connectivity must be authenticated and authorized when they get attached to the network and start using/accessing 3GPP services. For authentication and authorization, existing security mechanisms, which are based on USIMs , shall be used.
For improved security, the MT or ME may use suitable trusted computing technologies.
5.2.3.1 General p. 14
- A secured interface between the UE holding the (U)SIM and other PNE's in the PAN is required. This "local interface" must be able to protect against eavesdropping, and undetected modification attacks on security-related signalling data (e.g. authentication challenges and responses). Cryptographic or physical means may be used for this purpose.
- Both endpoints of the local interface shall be mutually authenticated and authorized.
- The ME/MT without (U)SIM shall be capable of communicating with the U(SIM) only if the UE containing (U)SIM is switched on and a (U)SIM is powered on. Furthermore the ME/MT without (U)SIM shall not be allowed to change the status of the UE with active (U)SIM, or the remote (U)SIM, e.g. to reset it, or to switch its power on or off.
- The ME/MT without the (U)SIM shall be capable of detecting the presence and availability of the active (U)SIM on the UE containing it. It also has the ability to terminate an authenticated network sessions when, the (U)SIM is no longer accessible within a short monitoring time period.
- The user shall have the capability to shut off sharing of (U)SIM feature. The owner of the UE holding the active (U)SIM should authorize its use.
- Integrity and privacy of signalling between ME/MTs and the PLMN shall be supported. No leakage of (U)SIM information to the user, or any third party over the wireless interface (e.g. Bluetooth/WLAN).
- Whenever someone (a specific device) tries to remotely access a (U)SIM for the first time some sort of alert shall be sent, e.g. a message will be displayed informing the user of the access. The user can then decide whether the access is authorized and can allow or disallow it.
- The UE holding the (U)SIM should be responsible for mediating access to the (U)SIM Application/Data such as controlling the logical channels.
- UICC presence detection shall be supported via the local interface.
- When the (U)SIM is re-used over local interfaces, additional access control on the Applications/Data information shall be implemented by the UE holding the active (U)SIM compared to the case when it is accessed by the UE holding the (U)SIM directly. For example, some AT commands might have to be restricted.
5.2.3.2 PNE management requirements p. 15
- Default Settings The default settings of any PNE coming from the manufacturer should always be set to "Do Not Auto Connect" or "Do Not Make Discoverable". The user must be aware that they are allowing their PNE to "be seen" by other devices.
- Connection Confirmation A PNE shall only accept a connection from another PNE after receiving a confirmation from the user indicating willingness to accept such a connection (i.e. there should be no "auto-accept" feature on the PNE). The requesting PNE should represent itself via its Unique Identifier.
5.2.4 Charging p. 15
If any charges are made for the provision of PNM these should be levied to the active subscription of the PAN.
5.3 PNE redirecting application p. 15
The Personal Network may comprise more than one UE or PAN. Each entity belonging to a Personal Network is generally termed as a PNE. The PNE may be a single device or a group of devices. The Personal Network from a user's perspective is his own network. Any of his PNEs may connect to each other, whereby the user may restrict public access via means provided by PNM. Personal Network Elements may not have public user IDs (E.g. MSISDN or URI), and therefore "other" users are not able to directly address data to these TEs.
The PNE Redirecting application is based on the PN UE Redirecting Service. In contrast to the PN UE Redirecting Service the PNE Redirecting application shall not only allow to activate/deactivate UEs but is able to direct data to particular TEs of the UEs or to connected MEs. Thus a PNE is not limited to UEs and it is possible to handle particular components within a UE or PAN as PNE.
Annex A.1 shows a use case describing aspects of PNE-PNE connection.
5.3.1 Requirements for PNE redirecting application p. 15
- All PN UE Redirecting requirements shall apply to the PNE Redirecting Service with PNE substituting UE.
- Registration data in the network shall include information that determines the PAN or UE a registered PNE belongs to. Furthermore registration data shall comprise the public user identities of the UEs and PANs in the Personal Network.
- It shall not be possible to register PNEs that are neither part of a UE or registered component of a PAN.
5.3.2 Usability requirements p. 16
- All usability requirements of the PN UE Redirecting application shall apply to the PNE Redirecting Service.
5.3.3 Security p. 16
- Registration of PNEs to a PN shall require the consent of the subscriber by appropriate means, e.g. an "invite" function,
- Advanced PNM shall ensure the integrity and confidentiality of between PNEs in a Personal Network.
- The PNE shall be authenticated towards the PLMN based on a locally connected USIM. Only authorised and suitably authenticated PNEs should be able to use a locally connected USIM for network authentication purposes.
5.3.4 Charging p. 16
- All charges for terminating services shall be levied to the active subscription of the PAN where the activated PNE belongs to, even when a terminating service was originally addressed to another PNE belonging to the PN.
- It shall be possible to raise registration/deregistration and activation/deactivation fees.
5.4 PN access control for PNE networks p. 16
- Guest UEs may be provided access to PNEs of a PN.
5.4.1 Requirements for PN access control for PNE networks p. 16
- All Service requirements for PN Access Control for Personal UE networks shall also apply to the PNE networks.
5.4.2 Usability requirements for PN access control in PNE networks p. 16
- PN access level settings for a particular PNE of the PN to be public / private