Content for TS 33.256 Word version: 18.2.0
5 Security procedures for UAS
5.1 General
5.2 UUAA
5.2.1 UUAA in 5GS
5.2.1.1 General
5.2.1.2 UUAA Procedure at Registration
5.2.1.3 UUAA Procedure during PDU Session Establishment
5.2.1.4 UUAA re-authentication procedure (5G)
5.2.1.5 UUAA Revocation
...
...
5 Security procedures for UAS p. 8
5.1 General p. 8
5.2 UUAA p. 9
5.2.1 UUAA in 5GS p. 9
5.2.1.1 General p. 9
The UAV USS authentication and authorization (UUAA) is the procedure to ensure that the UAV can be authenticated and authorized by a USS before the connectivity for UAS services is enabled. This clause specifies the relationship between primary authentication (as described in clause 6.1 in TS 33.501) and UUAA. An UAV is allowed to perform UUAA with the USS/UTM only after the UAV (UE) has completed successfully primary authentication.
It may be triggered by the AMF when UAV is registering with 5GS or triggered by the SMF during the PDU session establishment procedure. The UUAA procedure may also be triggered by a USS for re-authentication if the USS had authenticated the UAV. Network support for UUAA during registration is optional while it is mandatory during the PDU Session establishment. UE Support for UUAA during registration and during the PDU Session establishment is mandatory.
The AMF or SMF triggers the UUAA procedure if the UAV has an Aerial UE subscription and the UAV requests access to UAS services by providing the CAA-Level UAV ID of the UAV in the Registration Request or PDU Session Establishment Request.
The UUAA is performed between the UAV and the USS. The UAV is authenticated based on the CAA-Level UAV ID and credentials associated to the CAA-Level UAV ID. The authentication messages are included in a transparent container and conveyed between the UAV and the USS via a 3GPP UAS NF.
On successful completion of a UUAA, the USS can send UAS security information in the UUAA Authorization Payload to the UAV. The contents of that security information are out of scope of the 3GPP specifications.
The UUAA procedure at registration in 5G is described in the clause 5.2.1.2 and the UUAA procedure during PDU session establishment procedure is described in the clause 5.2.1.3.
At any time after the initial registration, the USS or the AMF (when the networking supports UUAA during registration) may initiate the Re-authentication procedure for the UAV. The AMF initiated Re-authentication procedure is described in the clause 5.2.1.2, whereas the USS initiated Re-authentication procedure is described in the clause 5.2.1.4.
Figure 5.2.1.1-1 provides an example of how UUAA fits into the 5GS procedures. The complete description of this flow is given in TS 23.256.
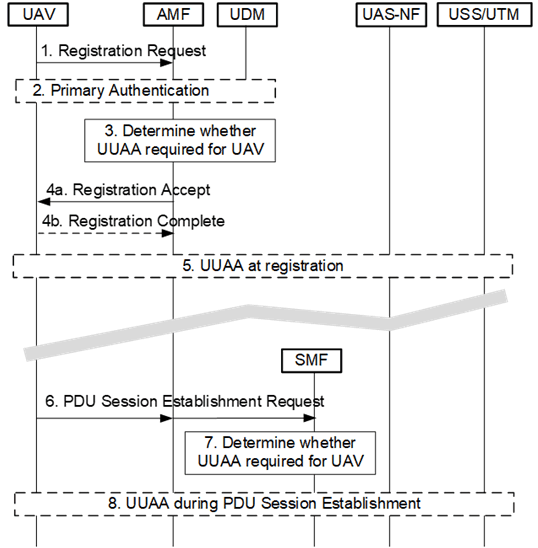
Step 1.
The following procedure is for UUAA during PDU session establishment:
The UE sends a Registration Request message to the AMF. The UE may provide a CAA-Level UAV ID, and optionally a USS address/IP address, to indicate the request is registering for UAS services. In case the CAA-Level UAV ID and/or USS address/IP address is configured not to be sent in plain text, e.g., the USS address or an IP address not to be exposed in public, the CAA-Level UAV ID, and USS/IP address if available, shall be sent after the NAS security is established.
Step 2.
AMF completes security set up including primary authentication as needed.
Step 3.
After successful Primary authentication, AMF determines whether UUAA is required for the UE. UUAA shall only be triggered if the UE has provided a CAA-Level UAV ID and has a valid Aerial UE subscription. AMF may skip UUAA if the UE has completed UUAA successfully before and the UE UUAA is current, i.e., the UE's authentication and authorization has not been revoked after a previous successful UUAA.
Step 4a.
AMF shall return a Registration Accept message to the UE and indicate that UUAA is pending.
Step 4b.
UE may send a Registration Complete message to acknowledge the AMF.
Step 5.
AMF triggers the UUAA procedure if determined needed in step 3 as described in clause 5.2.1.2.
Step 6.
The UE sends a PDU Session Establishment Request message to the SMF including a CAA-Level UAV ID to indicate the request is for UAS services.
Step 7.
The SMF determines whether UUAA is required for the UE. UUAA shall only be triggered if the UE has provided a CAA-Level UAV ID and has a valid Aerial UE subscription. SMF may skip UUAA, the UE has completed UUAA successfully with the same USS/DN before, i.e., at registration as in step 5 or in previous PDU Session Establishment procedures and a successful UUAA result is available.
Step 8.
The SMF triggers the UUAA procedure if determined needed at step 7 as described in clause 5.2.1.3.
5.2.1.2 UUAA Procedure at Registration p. 11
The UUAA procedure at registration is triggered by an AMF with the details described below, which considers only the security related parameters (see TS 23.256 for full details of the flows). For an AMF initiated re-authentication, the procedure starts from the step 2.
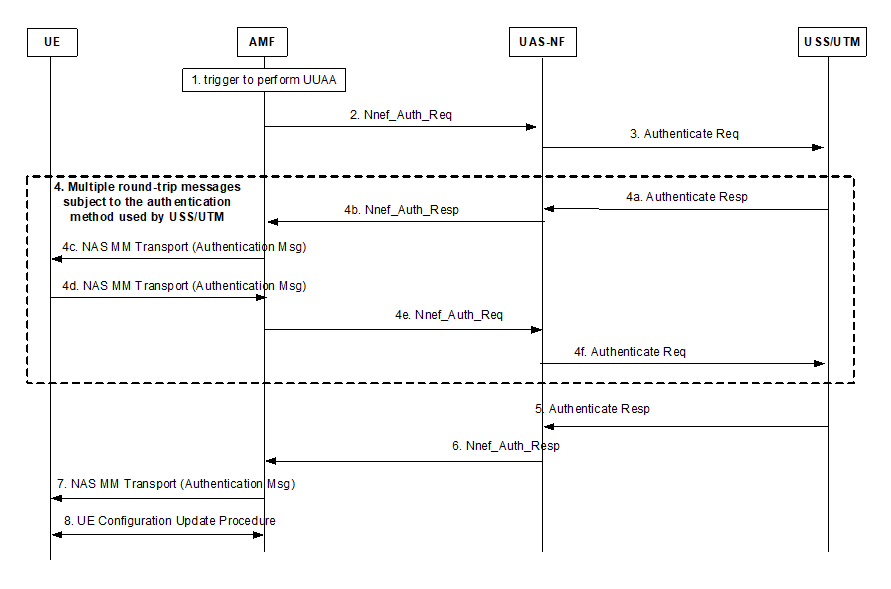
Step 1.
The AMF triggers the UUAA procedure as described in clause 5.2.1.1.
Step 2.
The AMF sends a message Nnef_Auth_Req to the UAS NF, including the GPSI and the CAA-Level UAV ID, and the Aviation Payload if provided by the UE for USS to authenticate the UAV. The AMF may include other information in the request as in TS 23.256.
Step 3.
The UAS NF resolves the USS address based on CAA-Level UAV ID or uses the provided USS address. Only authorized USS shall be used in order to ensure only legitimate entities can provide authorization for UAVs. The UAS NF sends an Authentication Request to the USS. The Authentication Request shall include the GPSI, the CAA-Level UAV ID, a UAS NF Routing information (e.g., an FQDN or IP address) which uniquely identifies the UAS NF located in the 3GPP network that handles the UAV related messages exchanges with the corresponding external USS/UTM and the transparent container. Other information may also be included in this message as in TS 23.256.
Step 4.
The USS and the UE exchange Authentication messages:
Step 4a.
Step 5.
The USS replies to UAS NF with the Authentication Response message. It shall include the GPSI and a transparent container composed of an authentication message.
Step 4b.
The UAS NF sends the transparent container received in 4a to the AMF with the GPSI.
Step 4c.
The AMF forwards the transparent container to the UE over NAS MM transport messages.
Step 4d.
The UE responds to the AMF with an Authentication message embedded in a transparent container over a NAS MM transport message.
Step 4e.
The AMF sends a message Nnef_Auth_Req to the UAS NF, including the GPSI and the CAA-Level UAV ID, and the transparent container provided by the UE.
Step 4f.
The UAS NF sends an Authentication Request to the USS. The Authentication Request shall include the GPSI, the CAA-Level UAV ID and the transparent container.
The USS sends the UAS NF an Authentication Response message. The Authentication Response shall include the GPSI, the UUAA result (success/failure), the authorized CAA-level UAV ID, and a UUAA Authorization Payload that contains UAS security information if the USS has such information to send.
The UAS NF stores the GPSI, USS Identifier (and the binding with the GPSI) and the CAA-level UAV ID (and the binding with the GPSI).
Step 6.
The UAS NF sends the AMF an Authentication Response message, including the GPSI, the UUAA result (success/failure), the authorized CAA-level UAV ID, and the UUAA Authorization Payload received in step 5.
Step 7.
The AMF sends to the UE the UUAA result (success/failure) received in step 6. The message(s) used in step 7 are given in TS 23.256.
The AMF stores the results, together with the GPSI and the CAA-level UAV ID.
Step 8.
If UUAA result is success, the AMF sends to the UE the UUAA Authorization Payload, received in step 6, during a UCU procedure as described in TS 23.256. The UE shall store the authorization information if received such as UAS Security information along with the CAA-level UAV ID.
5.2.1.3 UUAA Procedure during PDU Session Establishment p. 12
1. The SMF determines whether UUAA is required as described in the clause 5.2.1.1 if the UE provides a CAA-Level UAV ID indicating UAS services and optionally the Aviation Payload if provided by the UE for USS to authenticate the UAV in the PDU Session Establishment request. The SMF triggers a UUAA procedure after the determination in step 7 in the clause 5.2.1.1.
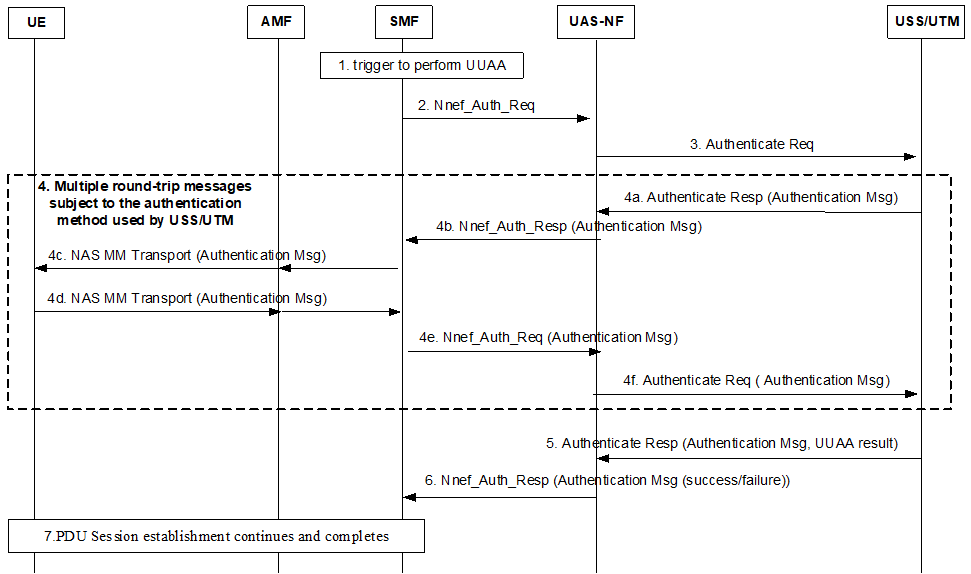
Step 1.
The SMF determines whether UUAA is required as described in the clause 5.2.1.1 and if the UUAA result is not received from the AMF, if the UE provides a CAA-Level UAV ID indicating UAS services and optionally the Aviation Payload if provided by the UE for USS to authenticate the UAV in the PDU Session Establishment request. The SMF triggers a UUAA procedure after the determination in step 7 in the clause 5.2.1.1.
Step 2.
The SMF sends a message Nnef_Auth_Req to the UAS NF, including the GPSI and the CAA-Level UAV ID, and the transparent container if provided by the UE. The SMF may include other information in the request as in TS 23.256.
Step 3.
The UAS NF resolves the USS address based on CAA-Level UAV ID or uses the provided USS address. Only authorized USS shall be used in order to ensure only legitimate entities can provide authorization for UAVs. The UAS NF sends an Authentication Request to the USS which includes the GPSI, the CAA-Level UAV ID, the UAS NF Routing information (e.g., a FQDN or IP address) which uniquely identifies the NF located in the 3GPP network that handles the UAV related messages exchanges with the corresponding external USS/UTM, and the transparent container. Other information may also be included in this message (see TS 23.256).
Step 4.
The USS and the UE exchange multiple Authentication messages:
Step 4a.
The USS replies to UAS NF with the Authentication Response message. It shall include the GPSI, a transparent container composed of an authentication message.
Step 4b.
The UAS NF sends the transparent container to the SMF.
Step 4c.
The SMF forwards the transparent container to the AMF, which then forwards to the UE over a NAS MM transport message.
Step 4d.
The UE responses the AMF with an Authentication message embedded in a transparent container over a NAS MM transport message. The AMF forwards to the SMF.
Step 4e.
The SMF sends a message Nnef_Auth_Req to the UAS NF, including the GPSI and the CAA-Level UAV ID, and the transparent container provided by the UE.
Step 4f.
The UAS NF sends an Authentication Request to the USS. The Authentication Request shall include the GPSI, the CAA-Level UAV ID and the transparent container.
Step 5.
The USS sends the UAS NF an Authentication Response message. The Authentication Response shall include the GPSI, the UUAA result (success/failure), the authorized CAA-level UAV ID, and a UUAA Authorization Payload that contains UAS security information if the USS has such information to send to the UAV.
If UUAA successful, the UAS NF stores the UAV UEs' UUAA context, including the GPSI, USS Identifier (and the binding with the GPSI) and the CAA-level UAV ID (and the binding with the GPSI).
Step 6.
The UAS NF sends the SMF an Authentication Response message, including the GPSI, the UUAA result (success/failure), the authorized CAA-level UAV ID, and the UUAA Authorization Payload received in step 5.
The SMF stores the results, together with the GPSI and the CAA-level UAV ID.
Step 7.
The SMF sends the UUAA result (success/failure), and the UUAA Authorization Payload received in step 5 to the UE. The message(s) used in step 7 and any further actions the UE and SMF take are given in TS 23.256.
Step 8.
The UE on receiving the UUAA result as success, shall store the authorization information if received such as, CAA-level UAV ID, and UAS Security information.
5.2.1.4 UUAA re-authentication procedure (5G) p. 14
As described in clause 5.2.1.1, the USS or the AMF (if support UUAA during registration) may initiate the Re-authentication procedure for the UAV at any time.
This clause describes the USS initiated Re-authentication procedure (the AMF initiated Re-authentication procedure is described in the clause 5.2.1.2). The below description considers only the security related parameters (for full details of the flows see TS 23.256).
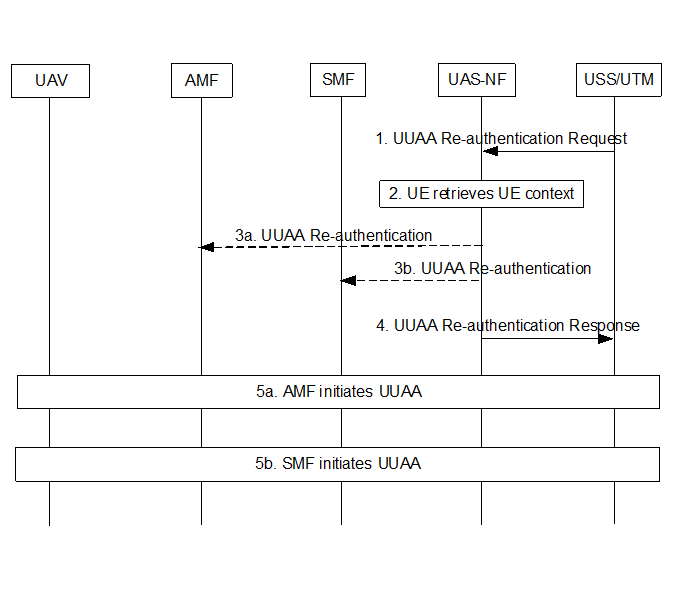
Step 1.
The USS sends a re-authentication request for the UAV to UAS-NF that includes GPSI, CAA-Level UAV ID, and an authentication message. It may contain the PDU Session IP address if available. The USS shall use the UAS NF Routing information received during the previous successful UUAA related to GPSI for sending the re-authentication request.
Step 2.
The UAS NF retrieves the UAV UE's context. The UE's context contains identity mapping between the GPSI and the USS identifier that performed UAA. The UAS-NF verifies the USS re-authentication request by checking whether the GPSI and the USS identifier match of the USS requesting the re-authentication the stored mapping of GPSI and USS identifier. The UAS-NF shall only continue the re-authentication procedures if match.
The UAS NF determines whether the target NF is an AMF or an SMF.
Step 3a or 3b.
- If the target NF is an AMF, the UAS NF further determines the target AMF for re-authentication and continues step 3a.
- If the target NF is an SMF, the UAS NF further determines the target SMF for re-authentication and continues step 3b.
The UAS NF sends to either the target AMF or the target SMF the UAA re-authentication request for the UE identified by the GPSI and for the SMF only the PDU Session IP address if available.
Step 4.
The UAS NF responses the USS that the UAA Re-authentication has been initiated.
Step 5a.
If the target NF is an AMF, the AMF initiates re-authentication of the UAV as UUAA described in the clause 5.2.1.2 (step 2 to step 9).
Step 5b.
If the target NF is an SMF, the SMF initiates re-authentication of the UAV as UUAA described in the clause 5.2.1.3 (step 2 to step 7).
5.2.1.5 UUAA Revocation p. 16
USS may trigger revocation of UUAA at any time. The below description considers only the security related parameters (for full details of the flows see TS 23.256).
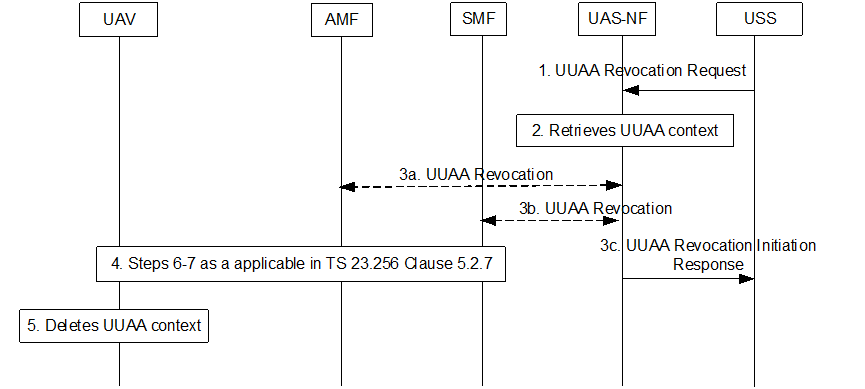
Step 1.
The USS sends an UUAA revocation request to UAS-NF. The request includes GPSI and CAA-Level UAV ID.
Step 2.
The UAS NF retrieves the UAV UE's context. The UE's context contains identity mapping between the GPSI and the USS identifier that performed UUAA. The UAS-NF verifies the USS revocation request by checking whether the GPSI and the USS identifier of the USS requesting the revocation match the stored mapping of GPSI and USS identifier. The UAS-NF shall only continue the revocation procedures if they match.
The UAS NF determines whether the target NF is an AMF or an SMF.
Step 3a or 3b.
- If the target NF is an AMF, the UAS NF further determines the target AMF for revocation and continues step 3a.
- If the target NF is an SMF, the UAS NF further determines the target SMF for revocation and continues step 3b.
The UAS NF sends to either the target NF, i.e., the target AMF or the target SMF the UUAA revocation message for the UE identified by the GPSI and the PDU session identified by the GPSI and the IP address. The target NF (i.e., the target AMF or the target SMF) shall respond to the UAS NF to indicate the revocation has been successful.
Step 3c.
The UAS NF responds back to the USS indicating that authorization revocation request has been successfully initiated as in TS 23.256 and the UAS NF shall delete the UUAA context.
Step 4.
The target NF i.e., either the target AMF or the target SMF on receiving UUAA revocation notification message, determines to send UUAA revocation indication to the UE. The target NF (either an AMF or an SMF) informs the UE that UUAA is revoked and takes actions as described in TS 23.256 with the following adaptations.
Step 4a.
If the target NF is AMF, the AMF shall send UUAA revocation indication in the UCU procedure as described in clause 5.2.7 of TS 23.256 and the AMF shall delete the UUAA context being revoked.
Step 4b.
If the target NF is SMF, the SMF shall send UUAA revocation indication in a network initiated PDU session release process as described in clause 5.2.7 of TS 23.256 and the SMF shall delete the UUAA context being revoked.
Step 5.
The UE on receiving UAA revocation indication shall delete all UUAA related authorization data corresponding to the CAA-Level-UAV ID and the UE sends an UUAA revocation acknowledgement to the target NF which provided the UUAA revocation indication.