Content for TS 22.141 Word version: 18.0.0
4 Presence models p. 8
4.a A brief introduction to the Presence Service p. 8
This clause attempts to give a simplistic high level informative overview of what presence is from a user's perspective, and how it is used to published to, and accessed by, other users.
Mark's ability and willingness to be reached for communication is defined by a set of information known as presence information. Mark's presence information may be related to his mobile network connection status, however it represents much more than just whether he has network coverage or not. Mark also defines a set of access rules to control access to his presence information. For the presence service, Mark is represented by a presentity (presence entity) associated with Mark's presence information and set of access rules.. In this example, Mark's presence information consists of user status and location information.
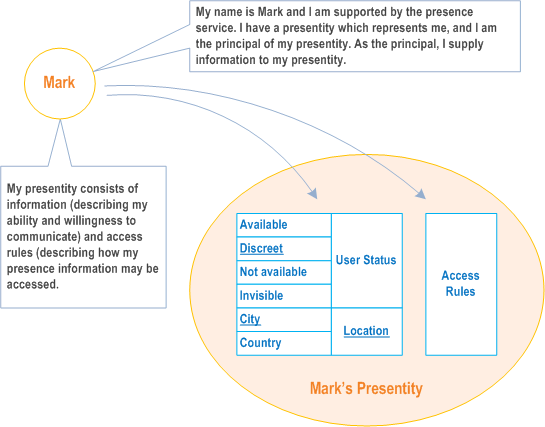
As well as representing a user such as Mark, a presentity may even be created to represent an abstract service or application (e.g. to provide road traffic information, sports results, news headlines etc.). The entity represented by the Presentity (in this case Mark) controls the supply of information for the presentity and is known as the principal; thus Mark is principal of his presentity (see Figure 4.a-1).
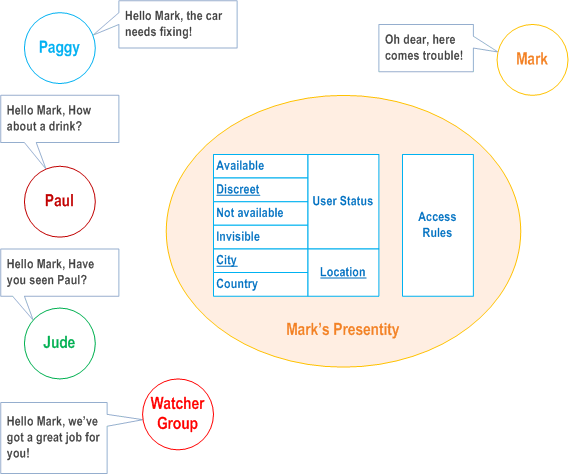
Paggy, Paul and Jude (e.g. Mark's callers or instant messaging buddies) who want to determine Mark's ability (and willingness) to communicate may do so by checking the status information in Mark's presentity. By doing so, Paggy, Paul and Jude become watchers of Mark (see Figure 4.a-2).
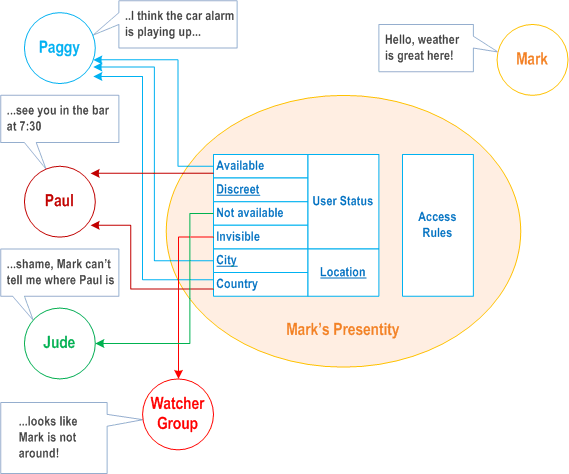
To protect his privacy and confidentiality, Mark has full control over whether Paggy, Paul and Jude, or any other group of watchers, can access his presence information. Mark may give different watchers different levels of access so that, for example Paggy can see all of Mark's of presence information, Paul may only see part of it, and Jude can see none of it. Hence, Mark can control (per watcher) which parts of his presence information may be seen, and he may decide that specific watchers have restricted access, and that some do not have any access at all. Indeed, Mark may also define his presence information and set up his access rules so that some watchers are given different information (e.g. Jude is told that Mark is not available, when in fact he is available), see Figure 4.a-3.
Mark's presentity consists of dynamic and static information supplied directly by himself and/or by the network. Some of the dynamic information may be derived from a number of sources (e.g. equipment login/attachment, roaming status, keyboard activity monitoring, equipment type, location information etc.). An example of the static information could be a fixed telephone number. The network may also add further information to the presentity (e.g. the evening/night times when his mobile is usually switched offderived from his usage patterns) to provide customised presence information.
By supporting a presence service in the network, the operator has the capability to offer an exciting range of advanced presence-based services and applications.