Content for TS 33.180 Word version: 17.8.0
1…
4…
4.3.4
4.3.5
5…
5.1.3
5.1.4…
5.2…
5.2.3
5.2.4
5.2.5
5.2.6…
5.3…
5.4…
6…
7…
7.3…
8…
9…
9.4…
10…
A…
B…
C…
D…
E…
F…
J…
L…
4.3.4 Protection of application plane signalling p. 20
4.3.4.1 Application plane signalling security |R15| p. 20
Application plane signalling security protects application signalling between the MC client and the MCX server. Initial key distribution for application signalling is performed by sending a client-server key (CSK) from the MC client to the MCX Server over the SIP interface. The key is secured using the identity key material provisioned by the Key Management Server. Following initial key distribution, the MCX server may perform a 'key download' procedure to update key material, and to key the client to allow multicast signalling to be protected.
There are a variety of types of application plane signalling, including:
- XML signalling within SIP payloads
- Control signalling (e.g. RTCP for floor control or transmission control).
- MCData signalling payloads within SIP payloads.
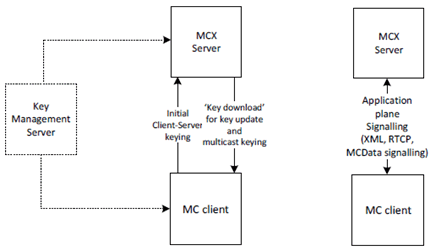
Application plane signalling security can also be applied between MCX servers. In this case the MCX servers are keyed manually. While not shown in Figure 4.3.4.1-1, application plane signalling uses SIP and HTTP and hence is also secured up to the SIP core and HTTP proxy respectively.
4.3.4.2 Security enforcement at the network edge |R15| p. 21
Clause 4.3.4.1 describes the application plane signalling security functions between the MC client and MCX Servers and between MCX Servers. These security functions can be enforced by the MCX Servers themselves as described in Clause 4.3.4.1.
However, in some scenarios, there may be value in applying application plane signalling security at the edge of the MC Domain. This deployment option involves moving security functions out of the MCX Servers and into Signalling Proxies at the edge of the MC Domain as shown in Figure 4.3.4.2-1.
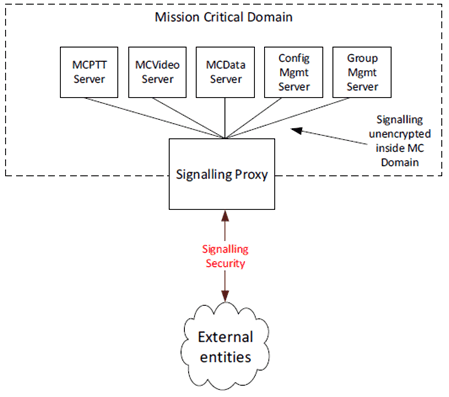
There are two types of Signalling Proxy:
- Client Signalling proxy (CS Proxy), which controls security towards the MC clients.
- Interconnection Signalling Proxy (IS Proxy), which controls security towards other MC Domains.
- The mission critical core network architecture is not exposed to Mission Critical clients or other external entitites. The client no longer needs to know the SIP URI of each distinct MCX Server.
- Intrusion detection within the XML signalling link is possible at the network edge.
- Policies can be assigned to signalling on entry to the Mission Critical network.
- The number of signalling protection keys required by the client and the MC Domain are reduced.
- Multicast bearers can be shared across multiple MCX Servers.