Content for TS 23.222 Word version: 19.1.0
0…
4…
5…
6…
6.3…
6.4…
7…
8…
8.5…
8.8…
8.9…
8.13…
8.17…
8.21…
8.25…
8.26…
8.28…
8.30…
9…
10…
10.4…
10.7…
11…
A
B…
B.2…
B.3…
C…
D…
8.21 Monitoring service API invocation
8.21.1 General
8.21.2 Information flows
8.21.2.1 Monitoring service API event notification
8.21.2.2 Monitoring service API event notification acknowledgement
8.21.3 Procedure
8.22 Auditing service API invocation
8.22.1 General
8.22.2 Information flows
8.22.2.1 Query service API log request
8.22.2.2 Query service API log response
8.22.3 Procedure
8.23 CAPIF revoking API invoker authorization
8.23.1 General
8.23.2 Information flows
8.23.2.1 Revoke API invoker authorization request
8.23.2.2 Revoke API invoker authorization response
8.23.2.3 Revoke API invoker authorization notify
8.23.3 Procedure for CAPIF revoking API invoker authorization initiated by AEF
8.23.4 Procedure for CAPIF revoking API invoker authorization initiated by CAPIF core function
8.24 API topology hiding management
8.24.1 General
8.24.2 Information flows
8.24.2.1 API topology hiding notify
8.24.3 Procedure
...
...
8.21 Monitoring service API invocation p. 74
8.21.1 General p. 74
The procedure in this subclause corresponds to the architectural requirements for monitoring service API invocation.
8.21.2 Information flows p. 74
8.21.2.1 Monitoring service API event notification p. 74
The information flow for the monitoring service API event notification from the CAPIF core function to the API management function is same as the event notification from the CAPIF core function to the subscribing entity. Table 8.8.2.3-1 describes the information elements which are included in the monitoring service API event notification.
8.21.2.2 Monitoring service API event notification acknowledgement p. 74
The information flow for the monitoring service API event notification acknowledgement from the API management function to the CAPIF core function is same as the event notification acknowledgement from subscribing entity to the CAPIF core function. Table 8.8.2.4-1 describes the information elements which are included in the monitoring service API event notification acknowledgement.
8.21.3 Procedure p. 74
Figure 8.21.3-1 illustrates the procedure for monitoring service API invocation.
Pre-condition:
- The API management function has subscribed to monitoring event including filters such as invoker's ID and IP address, service API name and version, input parameters, and invocation result.
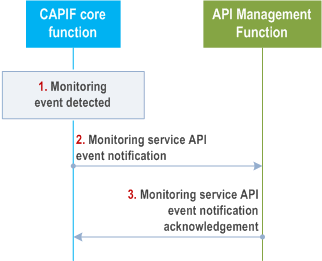
Step 1.
The CAPIF core function monitors the service API invocations applying the monitoring filters specified before.
Step 2.
Detection of a monitoring event by the CAPIF core function triggers notification to the API management function with the details of the monitored event.
Step 3.
The API management function sends a monitoring service API event notification acknowledgement to the CAPIF core function for the notification received.
8.22 Auditing service API invocation p. 75
8.22.1 General p. 75
The procedure in this subclause corresponds to the architectural requirements for auditing service API invocation. This procedure can be used for auditing of other CAPIF interactions i.e. service API invocation events, API invoker onboarding events and API invoker interactions with the CAPIF (e.g. authentication, authorization, discover service APIs) as well. The API management function can be within PLMN trust domain or within 3rd party trust domain.
8.22.2 Information flows p. 75
8.22.2.1 Query service API log request p. 75
Table 8.22.2.1-1 describes the information flow query service API log request from the API management function to the CAPIF core function.
| Information Element | Status | Description |
|---|---|---|
| Identity information | M | Identity information of the entity querying service API log request |
| Query information | M | List of query filters such as invoker's ID and IP address, service API name and version, input parameters, and invocation result |
8.22.2.2 Query service API log response p. 75
Table 8.22.2.2-1 describes the information flow query service API log response from the CAPIF core function to the API management function.
| Information Element | Status | Description |
|---|---|---|
| Result | M | Indicates the success or failure of query service API log request |
| API invocation log information | O (1) | API invocation log information such as API invoker's ID, IP address, service API name, version, invoked operation, input parameters, invocation result, time stamp information, Network Slice Info |
|
NOTE 1:
Information element shall be present when result indicates success.
|
||
8.22.3 Procedure p. 75
Figure 8.22.3-1 illustrates the procedure for auditing service API invocation.
Pre-conditions:
- Service API invocation logs are available at the CAPIF core function.
- Authorization details of the AMF are available with the CAPIF core function.
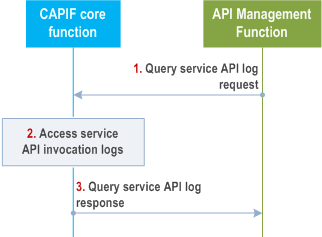
Step 1.
For auditing service API invocations, the API management function triggers query service API log request to the CAPIF core function.
Step 2.
Upon receiving the query service API log request, the CAPIF core function accesses the necessary service API log information for auditing purposes.
Step 3.
The CAPIF core function returns the log information to the API management function in the query service API log response.
8.23 CAPIF revoking API invoker authorization p. 76
8.23.1 General p. 76
The CAPIF controls the access of service API by the API invoker based on policy or usage limits. If the usage limits have exceeded, the authorization of the API invoker for accessing the service APIs is revoked. The decision to revoke the API invoker authorization may be triggered by the AEF or the CAPIF core function. The AEF can be within PLMN trust domain or within 3rd party trust domain.
In RNAA scenarios, the decision to revoke the API invoker authorization may be initiated by the CAPIF core function based on triggers at the CAPIF core function.
8.23.2 Information flows p. 76
8.23.2.1 Revoke API invoker authorization request p. 76
Table 8.23.2.1-1 describes the information flow revoke API invoker authorization request from the API exposing function to the CAPIF core function or from the CAPIF core function to the API exposing function.
| Information Element | Status | Description |
|---|---|---|
| API invoker identity information | M | The information that determines the identity of the API invoker |
| Service API identification | M | The identification information of the service API for which the authorization is revoked. |
| Cause | M | The cause for revoking the API invoker authorization |
8.23.2.2 Revoke API invoker authorization response p. 77
Table 8.23.2.2-1 describes the information flow revoke API invoker authorization response from the CAPIF core function to the API exposing function or from the API exposing function to the CAPIF core function.
| Information Element | Status | Description |
|---|---|---|
| Result | M | Indicates the success or failure of revoke API invoker authorization. |
8.23.2.3 Revoke API invoker authorization notify p. 77
Table 8.23.2.3-1 describes the information flow revoke API invoker authorization notify from the CAPIF core function to the API invoker.
| Information Element | Status | Description |
|---|---|---|
| API invoker identity information | M | The information that determines the identity of the API invoker whose authorization has been revoked |
| Service API identification | M | The identification information of the service API for which the authorization is revoked. |
| Cause | M | The cause for revoking the API invoker authorization |
8.23.3 Procedure for CAPIF revoking API invoker authorization initiated by AEF p. 77
Figure 8.23.3-1 illustrates the procedure for revoking API invoker authorization to access service API initiated by the AEF.
Pre-conditions:
- The API invoker is authenticated and authorized to use the service API.
- The AEF in the CAPIF is configured with the access policy to be applied to the service API invocation corresponding to the API invoker and the service API.
- Authorization details of the AEF are available with the CAPIF core function.
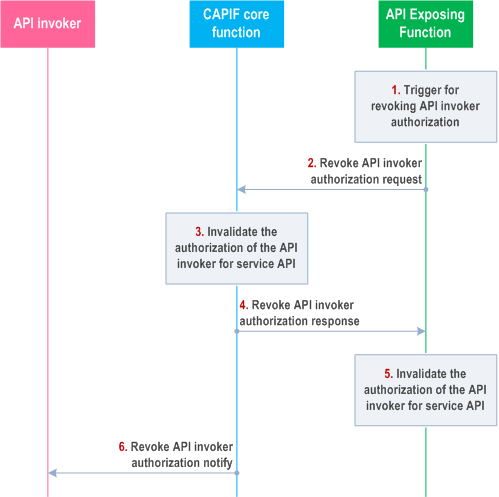
Step 1.
The AEF triggers the revocation of the API invoker authorization.
Step 2.
The AEF sends revoke API invoker authorization request to the CAPIF core function with the details of the API invoker and the service API.
Step 3.
Upon receiving the information to revoke the API invoker's authorization for service API invocation, the CAPIF core function invalidates the API invoker authorization corresponding to the service API.
Step 4.
The CAPIF core function sends a revoke API invoker authorization response to the AEF.
Step 5.
Upon successful revocation of API invoker authorization corresponding to the service API at the CAPIF core function, the AEF invalidates the API invoker authorization corresponding to the service API.
Step 6.
The CAPIF core function sends a revoke API invoker authorization notify to the API invoker whose authorization to access the service API has been revoked.
8.23.4 Procedure for CAPIF revoking API invoker authorization initiated by CAPIF core function p. 78
Figure 8.23.4-1 illustrates the procedure for revoking API invoker authorization to access service API initiated by the CAPIF core function. This procedure is also used for revoking API invoker authorization supporting RNAA scenarios.
Pre-conditions:
- The API invoker is authenticated and authorized to use the service API.
- The AEF in the CAPIF is configured with the access policy to be applied to the service API invocation corresponding to the API invoker and the service API.
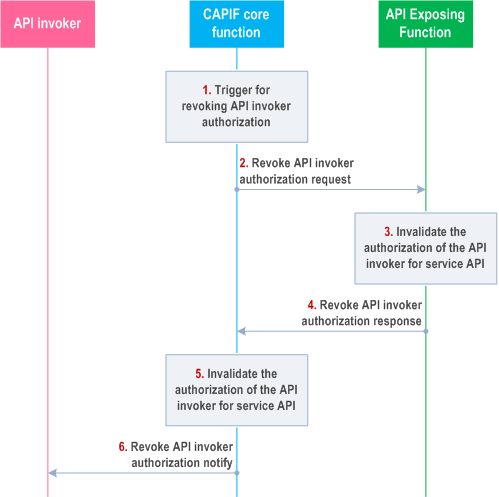
Step 1.
The CAPIF core function is triggered to revoke the API invoker authorization.
Step 2.
The CAPIF core function sends revoke API invoker authorization request to the AEF with the details of the API invoker and the service API.
Step 3.
Upon receiving the information to revoke the API invoker's authorization for service API invocation, the AEF invalidates the API invoker authorization corresponding to the service API.
Step 4.
The AEF sends a revoke API invoker authorization response to the CAPIF core function.
Step 5.
The CAPIF core function invalidates the API invoker authorization corresponding to the service API.
Step 6.
The CAPIF core function sends a revoke API invoker authorization notify to the API invoker whose authorization to access the service API has been revoked.
8.24 API topology hiding management |R16| p. 79
8.24.1 General p. 79
The following procedure in this subclause corresponds to the architectural requirements on API topology hiding. The procedure in this subclause supports API topology hiding by dynamically configuring the address of the AEF providing the Service API to the AEF entry point providing the topology hiding. The API publishing function and the API exposing function can be within PLMN trust domain or within 3rd party trust domain.
8.24.2 Information flows p. 79
8.24.2.1 API topology hiding notify p. 79
Table 8.24.2.1-1 describes the information flow API topology hiding notify from the CAPIF core function to the API exposing function.
| Information Element | Status | Description |
|---|---|---|
| Service API identification | M | The identification information of the service API with the API topology hiding |
| API exposing function(s) information | M | Indicates the one or more AEF(s) which provides the service API to apply the topology hiding including the interface details (e.g. IP address, port number, URI). |
| Action | M | Indicates the notification action for the API topology hiding (created or revoked). |
8.24.3 Procedure p. 80
Figure 8.24.3-1 illustrates the procedure for API topology hiding management by API (un)publish function.
Pre-condition:
- Authorization details of the APF are available with the CAPIF core function.
- The API exposing function has subscribed to CAPIF event for API topology hiding status.
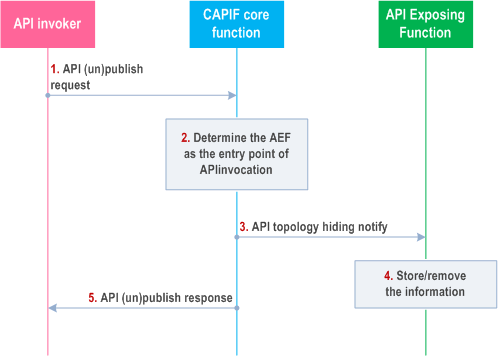
Step 1.
The API publishing function sends a service API publish request as described in subclause 8.3.2.1 or a service API unpublish request as described in subclause 8.4.2.1 to the CAPIF core function.
Step 2.
Upon receiving the service API (un)publish request, the CAPIF core function checks whether the API publishing function is authorized to perform the service API (un)publish. If authorized, based on the service APIs and policy:
Step 3.
- For service API publish, the CCF applies the topology hiding by selecting an AEF providing the topology hiding as the entry point for service API invocation. The selected AEF information is stored with the service API information received from API publish function at the CAPIF core function (API registry).
- For service API unpublish, the previously selected AEF as topology hiding entry point and the associated service API information at the CAPIF core function (API registry) are removed.
The CCF sends the API topology notify to the AEF selected as the entry point for service API invocation. The service API identification and the AEF(s) information which provides the service API details are included.
Step 4.
Upon receiving the notification, the AEF stores the received information for further service API invocation request forwarding if the action in the API topology notify indicates "created" or removes the stored API forwarding information if the action in the API topology notify indicates "revoked".
Step 5.
The CCF sends an API (un)publish response to the API publish function.