Content for TS 33.180 Word version: 17.8.0
1…
4…
4.3.4
4.3.5
5…
5.1.3
5.1.4…
5.2…
5.2.3
5.2.4
5.2.5
5.2.6…
5.3…
5.4…
6…
7…
7.3…
8…
9…
9.4…
10…
A…
B…
C…
D…
E…
F…
J…
L…
5.3 User key management
5.3.1 Key Management Server (KMS)
5.3.2 Functional model for key management
5.3.3 Security procedures for key management
5.3.4 Provisioned key material to support end-to-end communication security
5.3.5 KMS Certificate
5.3.6 KMS provisioned Key Set
...
...
5.3 User key management p. 53
5.3.1 Key Management Server (KMS) p. 53
5.3.1.1 General |R15| p. 53
To be able to be involved in end-to-end communication security the MC user requires key material to be provisioned from their Home Key Management Server (KMS). In addition, management entities which setup or control the end-to-end communication, such as the MCX Server and Group Management Server, will also require provisioning of key material.
In this clause, the 'user' could be a GMS, MCX Server, Signalling Proxy or any other entity containing a Key Management (KM) client.
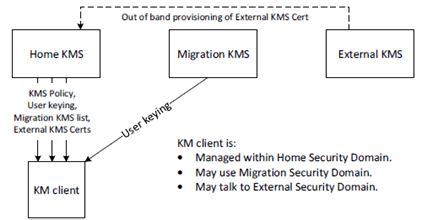
From the perspective of a user (KM client), there are three types of KMS:
- The Home KMS.
- Migration KMSs.
- External KMSs.
5.3.1.2 Home KMS |R15| p. 54
The Home KMS is the KMS trusted by the user (KM client) to manage the user's primary security domain. The Home KMS controls the use of media security for users (KM clients) within the primary security domain and is the source of KMS certificates for users or groups home to partner (i.e. external) MC domains.
The Home KMS shall provide the following to KM clients:
- The Home KMS Certificate.
- Policy around the use of provisioned key material.
- User key material for the authenticated user's identity.
- A list of permitted Migration KMSs and their addresses.
- A list of permitted External KMSs, and their KMS certificates.
- Received KMS Redirect Responses (KRRs).
5.3.1.3 Migration KMS |R15| p. 54
A Migration KMS is the KMS of a migration MC domain that controls media security of users (KM clients) while those users are authorised members of that migration MC domain.
A Migration KMS may provide the following to KM clients:
- The Migation KMS Certificate.
- User key material for the authenticated user's identity while a member of the migration MC domain.
- KMS Redirect Responses (KRRs).
5.3.1.4 External KMS |R15| p. 55
External KMSs serve partner security domains with which the user is able to communicate. To communicate with the partner security domain, the user (KM client) requires the External KMS certificate. External KMS certificates are provided by the user's Home KMS. In this way, the Home KMS maintains control of external communications.
The user (KM client) never connects to an External KMS.
5.3.2 Functional model for key management p. 55
Within the mission critical architecture, the Key Management Server (KMS) provisions key material associated with a specific MC identity (e.g. MCPTT ID). The KMS has interfaces with the key management clients. A key management client is responsible for making requests for identity-specific key material. Key provisioning clients are located in the MC UE, in the MCX Server(s) and in the Group Management Server(s).
The reference points for the KMS are shown in Figure 5.3.2-1.
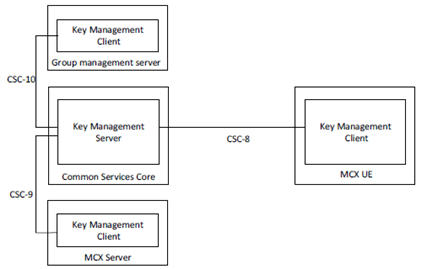
Figure 5.3.2-1 shows the CSC-8, CSC-9 and CSC-10 reference points for the Key Management Server within a MC domain.
The KMS may or may not be located within the Common Services Core (CSC) of the MC domain and may or may not make use of the HTTP proxy.
If the KMS does not make use of the HTTP proxy, then a secure HTTP connection (HTTPS) shall be established directly between the KMS and the KM client. In this case, each of CSC-8, CSC-9 and CSC-10 is a direct HTTP connection between the KMS and KM client in the MC UE, MCX Server or GMS (resp). The use of the TrK as defined in clause 9.3.3 may be used to protect the key material content in this configuration, and the InK may be used to integrity protect the key material content.
If the KMS does connect to and employ the use of the HTTP proxy, then for public safety users the TrK shall be used as defined in clause 9.3.3 to protect the key material content and the InK should be used for integrity protection. In this case, each of CSC-8, CSC-9 and CSC-10 uses HTTP-1 and HTTP-2 between the KMS and KM client in the MC UE, MCX Server or GMS (resp).
When a TrK is used to protect the transfer of key material between the KM client and KMS, the MC UE TrK identifier (TrK-ID) shall be provided by the KM client to the KMS during user KM authorization. If the InK-ID is not provided in the same user authorization request, then the TrK shall be used for integrity protection. If the InK-ID is provided in the same user authorization request, then the InK shall be used for integrity protection.
5.3.3 Security procedures for key management p. 56
The procedure for the provision of identity-specific key material when the HTTP proxy is supported between the KMS and the KM client is described in Figure 5.3.3-1. The procedure is the same whether the key management client in the MC UE, an MCX Server or a Group Management Server is making the request.
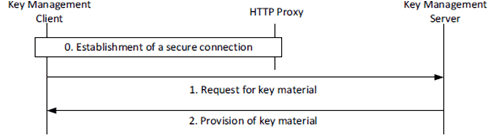
The procedure in Figure 5.3.3-1 is now described step-by-step.
Step 0.
The procedure for the provisioning of identity-specific key material when the HTTP proxy is not used between the KMS and the KM client is as described in Figure 5.3.3-2.
The key management client establishes a connection to the KMS. As with other elements in the Common Services Core, the connection is routed via, and secured by, the HTTP Proxy. The message flow below is within this secure connection.
Step 1.
The key management client makes a request for user key material from the KMS. The request contains an access token to authenticate the user as defined in clause 5.1. The request shall also contain the TrK-ID and may contain the InK-ID. There are the followingtypes of request (as defined in Annex D):
- KMSInit Request. This request is the first request sent to the KMS to setup the user. This type of request is permitted to the Home KMS or to Migration KMSs.
- KMSKeyProv Request: This request is to obtain new key material from the KMS. The request may contain details of a specific identity (e.g. MCPTT ID) required for key management, and may contain a specific time for which the key material is required. This type of request is permitted to the Home KMS or to Migration KMSs.
- KMSCertCache Request: This request is to obtain external KMS certificates associated with external security domains (managed by another KMS). The request may contain details of the latest version of the cache received by the client. This type of request shall only be made to the Home KMS.
- KMS Redirect Response (KRR) upload: This procedure uploads a KRR received by the client to the Home KMS. This type of message shall only be sent to the Home KMS.
- KMS Cert Request: This request is to obtain a single KMS certificate based on a provided KMS URI.
- KMS Lookup: This message is to lookup the external KMS that should be used for a provided SIP URI.
- KMS Redirect Upload: This message is to upload a received discovery request response to the KMS for audit purposes.
- KMSInit Response. This response contains domain parameters and optionally, a new TrK and/or a new InK.
- KMSKeyProv Response: This response provides new key material to the user and optionally, a new TrK and/or a new InK.
- KMSCertCache Response: This response contains new or updated home KMS certificates and/or external KMS certificates required by the user for communications with external security domains.
- KMS Cert Response: This response is a KMSCertCache Response containing a single KMS Certificate (or an error message).
- KMS Lookup Response: This response is a to provide the client with information related to a Discovery Lookup request. Either the KMS URI that should be used for a user is provided, or permission is provided to use a specific External KMS.
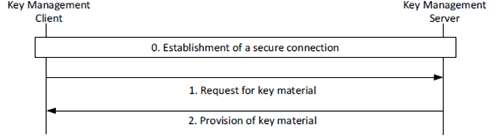
The procedure in Figure 5.3.3-2 is now described step-by-step:
Step 0.
As a result of this procedure, the key management client has securely obtained key material for use within the MC system.
The key management client establishes a direct HTTPS connection to the KMS. The following message flow is within this secure connection.
Step 1.
The key management client makes a request to the KMS. The request may contain the TrK-ID and may contain the InK-ID. The same requests can be made as defined above with a proxy.
Step 2.
The KMS provides a response based upon the authenticated user and the user's request. Optionally, the key material itself may also be encrypted using a 256-bit transport key (TrK). The response may also be signed using the TrK or the InK. The TrK and InK are initially distributed via an out-of-band mechanism along with their 32-bit identifiers (TrK-ID and InK-ID respectively).
5.3.4 Provisioned key material to support end-to-end communication security p. 58
End-to-end communication security for either group or private calls requires the provisioning of key material from the KMS. The key material provisioned to each user is listed below:
-
A KMSInit Response contains the KMS Certificate (domain specific key material associated to the KMS), and may contain:
- An updated TrK for the user (to replace the off-network-provisioned, bootstrap TrK).
- Policy around the use of KMS key material (Home KMS only)
- Address to which 'KMSCertCache' requests should be sent.
- Address to which 'KRRupload' messages should be sent.
-
A KMSKeyProv Response contains zero, or more, KMSKeySets and may contain:
- An updated TrK for the user (to replace existing TrK).
-
A KMSCertCache Response may contain:
- The KMS's Certificate(s) (current, updated or future).
- Migration KMSs (KMS URIs, access addresses, provisional TrKs).
- External KMS Certificates. This is domain specific key material associated with other KMSs. It is required to enable secure communications across security domains.
-
A KMSCert Response may contain:
- An External KMS Certificate. This is domain specific key material associated with the requested KMS URI. It is required to enable secure communications across security domains.
- A KMS Lookup Response does not contain key material, but may contain KMS URIs.
5.3.5 KMS Certificate p. 58
A KMS Certificate is defined in Annex D.3.2. A KMS Certificate contains the following:
- A Role of 'Home' or 'External', depending on whether the certificate is the issuing KMS's or is provided by another external KMS.
- The KMS Public Authentication Key (KPAK in RFC 6507 [9]).
- The KMS Public Confidentiality Key (Z_T in RFC 6508 [10]).
- The UID conversion (as described below).
- Choice of cryptographic domain parameters (such as those listed in RFC 6509 [8]).
- The time period for which this information is valid.
UID = Hash (MCPTT ID, KMS URI, validity period info).
As a consequence, there is a one-to-one correspondence between MC Service IDs and UIDs during each time period.
5.3.6 KMS provisioned Key Set p. 59
KMSKeySet(s) are defined in Annex D.3.3.2 and contain the following:
- A user signing key for each UID for the current time period (SSK and PVT in RFC 6507).
- A user decryption key for each UID for the current time period (RSK in RFC 6508).
- The key period number associated with the current keys.
- Optionally, the time period, for which the user key material is valid (e.g. month).