Content for TS 33.180 Word version: 17.8.0
1…
4…
4.3.4
4.3.5
5…
5.1.3
5.1.4…
5.2…
5.2.3
5.2.4
5.2.5
5.2.6…
5.3…
5.4…
6…
7…
7.3…
8…
9…
9.4…
10…
A…
B…
C…
D…
E…
F…
J…
L…
5.2.5 Key distribution with SAKKE-to-self payload p. 44
The key distribution mechanism defined in clauses 5.2.2, 5.2.3 and 5.2.4 may be extended to allow the initiating entity to be able to decrypt the distributed key, K contained within the payload.
In addition to encrypting the key, K, to the receiving entity, the key is also encrypted to the initiating entity. The UID used to encrypt the data is derived from the initiating entity's URI (e.g. sip:user.002@mcptt.example.org) and a time-related parameter (e.g. the current year and month). The encapsulated key is added to a SAKKE-to-self payload within the MIKEY I_MESSAGE. No other payloads (e.g. IDRr) are affected.
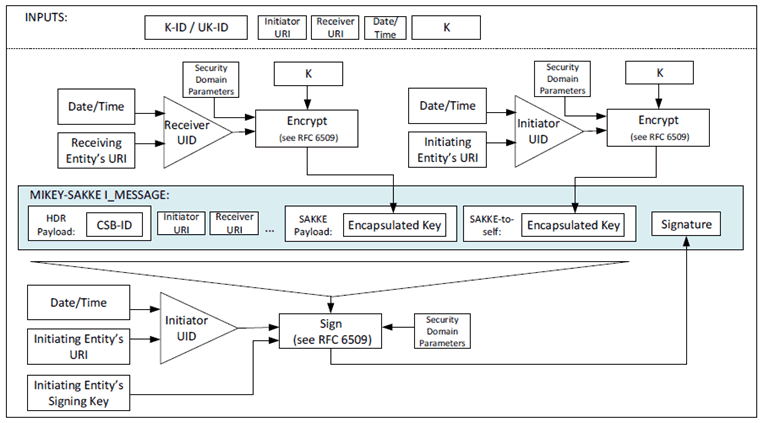
Figure 5.2.5-1: Common key distribution mechanism with SAKKE-to-self payload
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)