Content for TS 33.163 Word version: 17.0.0
4 Security Procedures for Battery Efficient Security for Very Low Throughput MTC Devices (BEST)
4.1 Introduction
4.2 BEST framework service description
...
...
4 Security Procedures for Battery Efficient Security for Very Low Throughput MTC Devices (BEST) p. 8
4.1 Introduction p. 8
This specification defines elements, protocols and procedures that enable battery efficient security for low throughput devices such as MTC devices. The BEST service is a secure channel between a UE and a HSE, optimised for low throughput and high latency devices that are battery constrained. The security is between the UE and either an element in the service provider home network (the HSE) or an element in the enterprise domain (the EAS). The design is modular and extensible so that it can be used to satisfy a wide range of use cases.
The following services are defined:
- BEST key agreement only service: This service is a battery efficient service for key agreement between a BEST compliant UE and the HSE or the EAS. The user plane for this service is provided by the application layer between the UE and the EAS and is out of scope of this specification.
- BEST user plane integrity protected service: This service is a battery efficient integrity protected user plane service for low throughput devices. This service includes the key agreement and includes integrity protected security over small data over NAS User Plane. The user plane for this service can be either terminated in the HSE (so called UE-to-HSE mode) or in the EAS (so called UE-to-EAS mode). Control messages are always terminated in the HSE.
- BEST user plane confidential service: This service is a battery efficient integrity and confidentiality protected user plane service for low throughput devices. The user plane for this service can be either terminated in the HSE (so called UE-to-HSE mode) or in the EAS (so called UE-to-EAS mode). Control messages are always terminated in the HSE.
4.2 BEST framework service description p. 8
4.2.1 EPS architecture p. 8
Figure 4.2.1-1 shows the EPS architecture of the extended user plane protection service for the case where the UE's PDN connection terminates at the P-GW. Figure 4.2.1-2 shows the architecture of the extended user plane protection service for the case where the UE's PDN connection terminates at the SCEF.
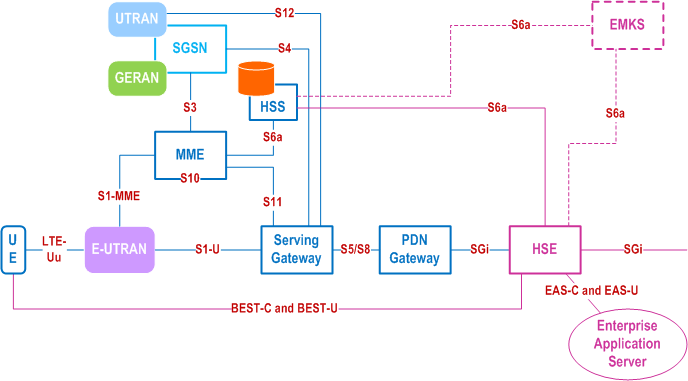
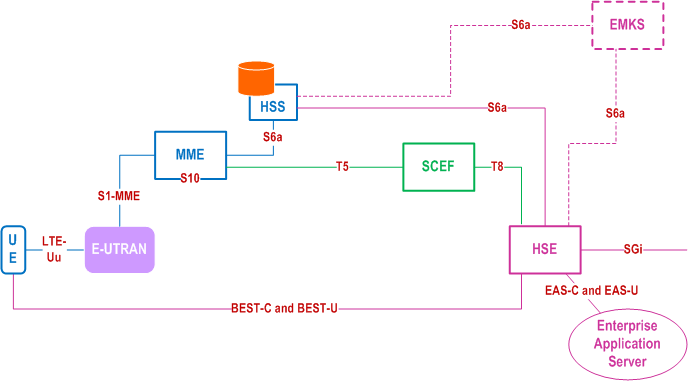
In an EPS network, the BEST service requires the following components:
-
Home Security Endpoint (HSE): This is the termination point in the home network that performs the following functions:
- Terminating the control plane for BEST between the UE and the HSE
- Terminating the secure communication for BEST between the UE and the HSE and forwarding to and from the Data Network via the SGi if UE-to-HSE security is selected.
- Routing the user plane traffic for BEST between the UE and the Enterprise Application Server (EAS) via the SGi if UE-to-EAS security is selected.
- Anchor for BEST Key agreement only service. Exposes an interface for EAS to obtain MNO provided pre-shared key.
- End to Middle Key Server (EMKS): This is an optional key server element that manages the key communication with the HSS (for quintets) and stores keys to reduce loading on the HSE and HSS. The EMKS has interfaces to the HSS (S6a) and the HSE (S6a).
- S6a between the HSS and the HSE
- S6a between the HSS and EMKS
- S6a between the EMKS and the HSE
- BEST-C and BEST-U between the UE and the HSE
- EAS-C and EAS-U between the HSE and the EAS. Definition of this interface is out of scope. Annex B describes a candidate interface based on Restful HTTP for the communication between the HSE and the EAS.
- The HSE may be implemented as part of the SCEF.
- The EAS may be an SCS/AS and use a T8 interface to access exposed network capabilities as described in TS 23.682.
- EMSDP via the SCEF only supports non-IP PDU Type communication.
4.2.2 5GS architecture |R17| p. 10
Figure 4.2.2-1 shows the 5GS architecture of the extended user plane protection service.
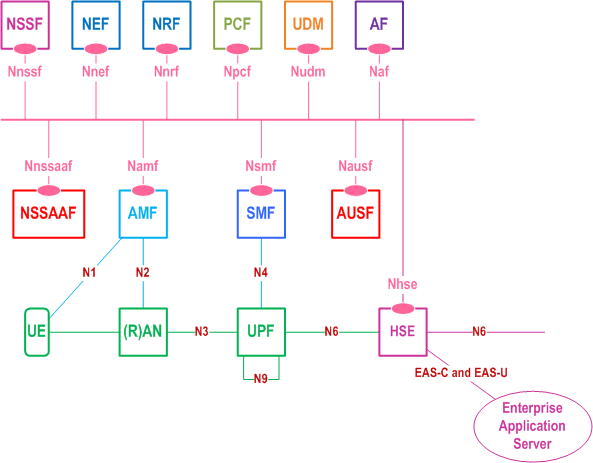
In a 5GS network, the BEST service requires the following components:
-
Home Security Endpoint (HSE): This is the termination point in the home network that performs the following functions:
- Terminating the control plane for BEST between the UE and the HSE
- Terminating the secure communication for BEST between the UE and the HSE and forwarding to and from the Data Network via the N3 if UE-to-HSE security is selected.
- Routing the user plane traffic for BEST between the UE and the Enterprise Application Server (EAS) via the N3 if UE-to-EAS security is selected.
- Anchor for BEST Key agreement only service. Exposes an interface for EAS to obtain MNO provided pre-shared key.
- SBA between the UDM and the HSE
- BEST-C and BEST-U between the UE and the HSE
- EAS-C and EAS-U between the HSE and the EAS. Definition of this interface is out of scope. Annex B describes a candidate interface based on Restful HTTP for the communication between the HSE and the EAS.
4.2.3 Architecture when using GBA, 5G GBA, AKMA or proprietary key agreement |R17| p. 11
When using GBA, according to TS 33.220, 5G GBA, according to TS 33.220, Annex N, AKMA, according to TS 33.535, or proprietary key agreement, the architecture may be either as for EPS architecture or 5GS architecture as required. In this case, the HSE shall be connected to the EPS or 5GS architecture according to the GBA, 5G GBA, AKMA or proprietary service instead. For GBA and 5G GBA, the HSE shall act as NAF. For AKMA, the HSE shall act as AF.