Content for TS 23.259 Word version: 17.0.0
7 Procedures and information flows for PN access control
7.1 General
7.2 PN access control procedures in the IM CN subsystem
...
...
7 Procedures and information flows for PN access control p. 31
7.1 General p. 31
Upon receiving a UE-terminating initial request, the PNM AS shall first check whether the request originates from another PN UE within the same PN as the terminating PN UE and if so the PNM AS shall allow the session establishment to continue. If the request does not originate from another PN UE within the same PN as the terminating PN UE the PNM AS shall invoke the PN access control application if it is enabled. If no access control list exists for the terminating UE, and if the PNM AS does not invoke the PN UE redirection for the terminating UE, the PNM AS sends the initial request to the terminating UE (i.e., a UE of a PN). Otherwise, the PNM AS verifies whether the originating UE of the initial request is a valid entry contained in the PN access control list for the terminating UE, before it initiates session towards the terminating UE. With a successful verification, the PNM AS sends the initial request to the terminating UE. With an unsuccessful verification, if the terminating UE is not a controllee UE, then the PNM AS rejects the initial request. If the terminating UE is a controllee UE, the PNM AS queries the controller UE whether the session to the controllee UE is allowed to be established. If it is allowed, and if the PNM AS does not invoke the PN UE redirection for the terminating UE, the PNM AS sends the initial request to the controllee UE. Otherwise, the PNM AS rejects the initial request. Figure 7.1-1 gives a snapshot of the scenario.
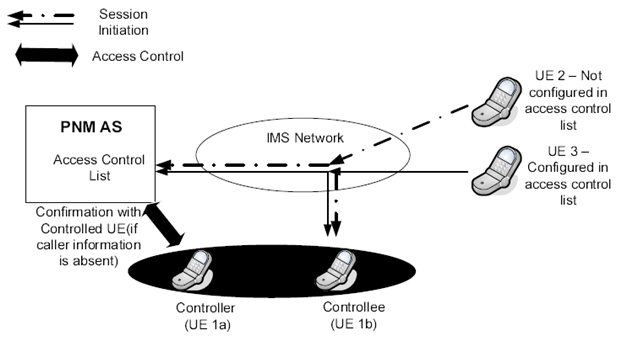
Figure 7.1-1: Overview of privacy based access control Procedures and Information Flows
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
The procedures at the PNM AS to accomplish the PN access control execution are described with the assistance of Figure 7.1-2.
When the PNM AS receives a SIP initial request and its PN access control logic is switched-on, if the Request URI of the initial request identifies with the controllee UE(s), the PNM AS shall further decide whether the Request URI uniquely identify a controllee UE within a PN:
-
if a controllee UE is uniquely identifiable, the PNM AS shall check whether the Caller is in the PN access control list;
- if the Caller is in the PN access control list, the PNM AS shall send the initial request to the controllee UE;
-
if the Caller is not in the PN access control list,
- if there is no need to interrogate the controller UE, the PNM AS shall reject the initial request;
- if there is a need to interrogate the controller UE, the PNM AS shall interrogate the controller UE and handle the initial request message based on the interrogation results from the PN-user.
-
if a controllee UE is not uniquely identifiable, the PNM AS shall perform the PN access control without invoking the controller UE (i.e., without any PN-user interaction) and check whether the Caller is in the PN access control list;
- if the Caller is in the PN access control list, the PNM AS shall send the initial request back to the S-CSCF (see TS 23.228);
- if the Caller is not in the PN access control list, the PNM AS shall reject the initial request.
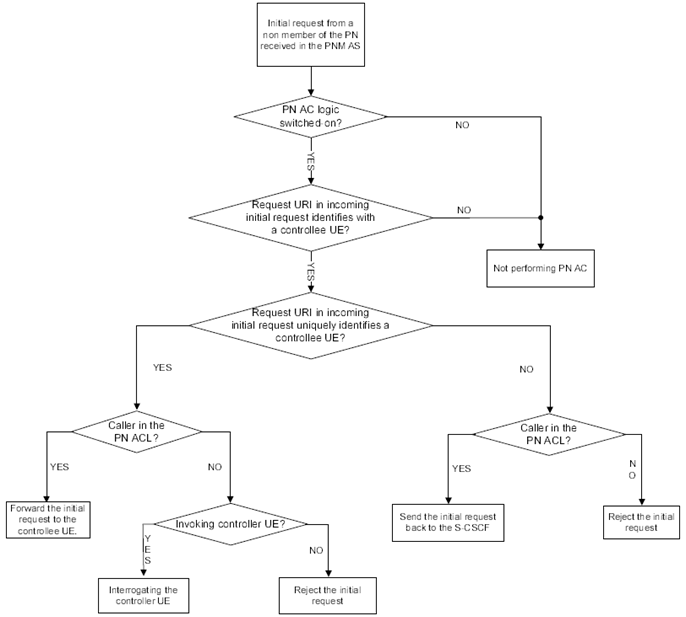
Figure 7.1-2: PN access control execution flow at the PNM AS (AC and ACL stand for Access Control and Access Control List, respectively)
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
7.2 PN access control procedures in the IM CN subsystem p. 33
Without lack of generality, the following assumptions have been made with respect to the terminals and the network.
<Assumptions related to identities of UEs>
- PN-user 1 has two UEs - UE 1a & UE 1b in the PN, containing identities user1_public1@home1.net and user1_public2@home1.net respectively, and having a subscription with the home network providing PNM service.
- UE 1b is configured as controllee UE and UE 1a as controller UE by the PN-user 1.
- The originating UE which initiates the request may belong to the same/different network where the PNM AS is located. The originating UE of the initial request needs not be aware of the setting of the access control done by PN-user 1.
- PN-user 1has configured UE2 with user2_public@home2.net as the only entry in the access control list related to the controllee UE in this example. When the PNM AS receives initial requests not coming from UE2, the PNM AS can query the controller UE and the continuation of the initial request depends on the outcome of the query.
- The following table summarizes the above assumptions.
| PN Of user | controllee UE | controller UE | Access List entries |
|---|---|---|---|
| (UE 1a) user1_public1@home1.net | No | N/A | N/A |
| (UE 1b) user1_public2@home1.net | Yes | UE 1a | (UE 2) user2_public@home2.net |
<Network assumptions>
- PN-user's home network provides PN access control, which allows PN-users to configure identities (e.g., a SIP URI) which are permitted to initiate sessions to the UE of the PN.
- This service is hosted by the PNM Server which is a SIP application server, serving scscf#1.
- For simple illustration, in this example, both identities of the PN are shown to be registered with the same S-CSCF (S-CSCF#1) to improve efficiency in signalling, which might be the case in most implementations.
- The PNM AS stores access control lists of controllee UE and the controller UE can process access control requests during dynamic procedures.