Content for TS 23.240 Word version: 17.0.0
4 Reference Architecture
4.1 GUP Functionalities
4.1.1 Harmonized access interface
4.1.2 Single point of access
4.1.3 Authentication of profile access
4.1.4 Authorization of profile access
4.1.5 Privacy control
4.1.6 Synchronization of data storage
4.1.7 Access of profile from visited network
4.1.8 Location of Profile Components
4.1.9 Charging for profile access
4.2 GUP functional entities
4.2.1 GUP Server
4.2.2 Repository Access Function (RAF)
4.2.3 GUP Data Repository
4.2.4 Reference Points
4.2.5 Applications
4.2.6 Message flow of using GUP
4 Reference Architecture p. 7
4.1 GUP Functionalities p. 7
4.1.1 Harmonized access interface p. 7
The GUP harmonized access interface is the interface which can be used by the GUP suppliers and GUP consumers to access, manage and transfer the profile data. This application layer interface is independent of the profile structure.
4.1.2 Single point of access p. 7
There exists for each Profile a single point of access, which knows the location of the various components of the Profile. A discovery service, e.g. Liberty Discovery Service Specification [2] may be used to get the contact reference information for this access point if not known by other means.
4.1.3 Authentication of profile access p. 7
A GUP functionality exists that is responsible to authenticate applications. Authentication is a vital function to be passed before any kind of access to GUP data is granted. GUP shall adopt generic mechanisms such as used for the OSA framework approach. More specifically GUP shall use authentication mechanisms from Liberty Alliance Project as specified in Liberty ID-WSF Security and Privacy Overview [5], Liberty Discovery Service [2] and Liberty ID-WSF Security Mechanisms [6].
4.1.4 Authorization of profile access p. 7
A GUP functionality exists that is responsible to authorise applications to access GUP data based on User specific or common privacy rules. All attempts to access the GUP data are to be authorized according to the defined policies which shall include the requestor information, the requested data, the target subscriber and the performed operation, or some of those.
GUP shall use authorization mechanisms from Liberty Alliance Project as specified in Liberty ID-WSF Security and Privacy Overview [5] and Liberty ID-WSF Security Mechanisms [6].
The GUP data structures need to satisfy the requirement to provide the authorization information on the different levels: profile, component or data element. In addition to the generic authorization data, additional service specific data may be defined (e.g. for LCS). The same applies for the authorization decision logic. The execution of the authorization logic leads to a decision whether a requestor is allowed to make the request at all, and additionally to which part of data the requestor has the appropriate access rights with regard to the nature of the request.
GUP provides mechanisms for the different GUP entities for managing the authorization data.
Both HPLMN based applications and non-HPLMN based applications are expected to send requests to the GUP Server. The GUP server shall have functionality to apply different authorization criteria, policy control and load control to HPLMN and non-HPLMN applications. Policy control and load control are out of the scope of the present document.
4.1.5 Privacy control p. 8
The tight connection of authentication, authorization and subscriber specific privacy requirements results in privacy control. Privacy control implies a centralized management for access rights including the subscriber's privacy requirements.
GUP shall use privacy control mechanisms and other privacy related features from Liberty Alliance Project as specified in Liberty ID-WSF Security and Privacy Overview [5] and Liberty ID-WSF Security Mechanisms [6].
4.1.6 Synchronization of data storage p. 8
The GUP data repository holds the master copy of the GUP component data. Applications or GUP server may copy (i.e. read) the component data or request synchronization. The present document defines how the data is requested and sent. What is thereafter done with the data by the application or GUP server is beyond the scope of the present document.
Synchronization means that the changes to the master copy of the data are propagated to the entities that request synchronization. The synchronization request specifies which data are monitored for changes. It is also possible to request that all changes are reported.
Synchronization may cause heavy processing load to the involved entities, thus some policies are required in the implementations but those are not specified for the time being. However the GUP interfaces should carry sufficient data for enabling the load control mechanisms to work.
The entity under a heavy processing load has the responsibility to handle the error cases and conditions and to reach the synchronization as fast as possible. All the unresolved errors or load balancing actions that affect synchronization shall be reported.
4.1.7 Access of profile from visited network p. 8
Access to GUP from a visited network shall follow the single point of access principle.
4.1.8 Location of Profile Components p. 8
A GUP functionality exists that keeps information where GUP data are located.
4.1.9 Charging for profile access p. 8
The GUP Server shall be capable of providing charging information, e.g. to enable transaction/event based charging.
Some GUP Data Repositories may provide charging information, while other GUP Data Repositories do not provide charging information.
Mechanisms are needed to permit the GUP Server to know which GUP Data Repositories are (and are not) producing their own charging information. When the GUP Data Repository is capable of producing charging information, mechanisms are needed for the correlation of the charging information produced by GUP Server and GUP Data Repository.
The charging information may also be used for other event logging, customer care, privacy auditing, etc. functions.
4.2 GUP functional entities p. 9
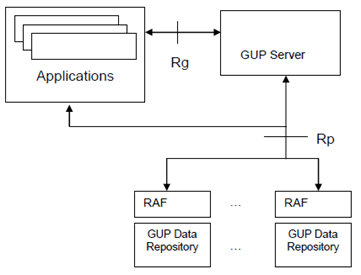
The GUP reference architecture as shown in Figure 4.1 consists of:
- GUP Server;
- Repository Access Function (RAF);
- GUP Data Repositories;
- Rg and Rp reference points;
- Applications.
An example of mapping the GUP reference architecture to current infrastructure environment is shown in Figure 4.2.
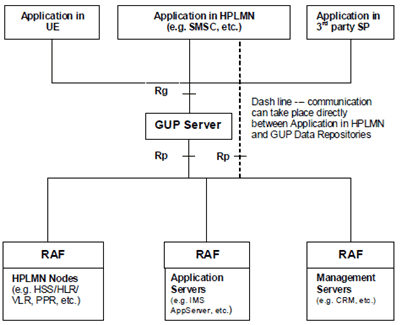
Figure 4.2: An example of mapping the GUP reference architecture to current infrastructure environment
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
4.2.1 GUP Server p. 10
The GUP Server is a functional entity providing a single point of access to the Generic User Profile data of a particular subscriber. The reference architecture does not specify or limit the physical location of the GUP Server enabling flexibility in the implementations. However, the GUP Server shall be located in the home operator network of the targeted subscriber.
The GUP Server includes the following main functionalities:
- Single point of access for reading and managing generic user profile data of a particular subscriber.
- Location of Profile Components.
- Authentication of profile requests.
- Authorization of profile requests.
- Synchronization of Profile Components.
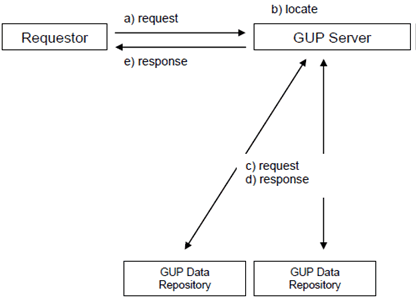
- Proxy mode (see Figure 4.3). The Application requests user related data located in the GUP Data Repositories from the GUP Server. After taking care of needed actions specified for the GUP Server (and depending on the type of the request) the GUP Server makes requests to the corresponding GUP Data Repositories and receives responses from them. Finally the Application gets a response to the original request from the GUP Server. Depending on the type of the request also possible subsequent responses are delivered through the GUP Server.
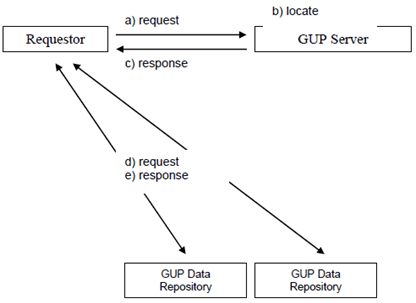
- Redirect mode (see Figure 4.4). The Application requests user related data located in the GUP Data Repositories from the GUP Server. After taking care of needed actions specified for the GUP Server (and depending on the type of the request) the GUP Server returns to the Application the information (e.g. address of GUP Data Repository(s)) to allow the Application to request the information from the GUP Data Repositories. The Application then directly requests the information from the GUP Data Repositories.
4.2.1.1 Single point of access p. 11
The GUP Server shall accept data management related requests from the applications via the Rg reference point, and either convey the corresponding GUP component specific requests to GUP Data Repositories via Rp reference point or redirect the Application to convey the requests to the GUP Data Repositories. Note that one data request from an application to the GUP Server can cause sending of several GUP Data Repository requests by the GUP Server or Application. Also mapping to proprietary interfaces instead of Rp is possible in implementations.
In Proxy mode the GUP Server shall receive the results of the requests from GUP Data Repositories and deliver the results back to the requestor (Application). In case of responses from several GUP Data Repositories the GUP Server shall combine separate XML documents received from the repositories and deliver the composed information to the requestor. In redirect mode the Application will receive the results of the requests from the GUP Data Repositories.
4.2.1.2 Location of profile components p. 12
The GUP Server stores information about the GUP Components and the locations of data repositories of GUP Components related to each subscriber. Thus e.g. the separate GUP components composing the whole User Profile of a certain subscriber can be located and identified. The application shall be able to affect where a new GUP Component is created by the GUP Server. It is beyond this specification how the GUP server gets the component locations in the cases when it is not involved in the creation of those components.
4.2.1.3 Authentication of profile request p. 12
The GUP Server shall make sure that the application requesting user profile data is properly authenticated. The authentication is based on the identification of the requesting application and/or the identification of the possible subscriber requesting the user profile data. The GUP Server may rely on the authentication made by other trusted entities.
4.2.1.4 Authorization of profile request p. 12
The GUP Server shall take care of the authorization of the access to the user profile data. The authorization itself may be handled by a separate entity in the network, or alternatively by the RAF or GUP Data Repository. The authorization shall be based on the requestor information, the requested data, the target subscriber and the performed operation, or some of them. The authorization rules of the requested data shall be defined at least in the GUP Component level in GUP Server. (Note that the authorization may be based on also on finer granularity of the data content.) It shall be possible to manage the authorization data via the Rg and Rp reference points.
4.2.1.5 Synchronization of profile components p. 12
In proxy mode, the GUP Server shall convey the data synchronization requests from the applications to the RAFs in the same way as the other profile requests. Also the related change notifications from the RAFs are passed on to the requesting application. This requires that some kind of book keeping about the synchronization requests implemented. In redirect mode the GUP server shall redirect the Application to the RAFs in the same way as the other profile requests.
The GUP Server may store a copy of the actual data from the GUP Data Repository, but it is up to the local policy of the GUP Server.
4.2.1.6 Additional functionality p. 12
The GUP Server may take part in the charging of the data management operations concerning the profile.
The GUP Server may take part in the rate and/or size limiting of the data operations towards the profile.
The GUP Server may utilise a discovery service to register its contact reference information.
4.2.2 Repository Access Function (RAF) p. 12
The Repository Access Function (RAF) realizes the harmonized access interface. It hides the implementation details of the data repositories from the GUP infrastructure. The RAF performs protocol and data transformation where needed.
The protocol between the RAF and the GUP data repository is out of the standardization scope. It is recommended that the protocol used should support GUP requirements.
The RAF may take part in the authorization of access to such GUP information, which are under the control of the RAF. In addition, the authorization data may be managed via the Rp reference point.
4.2.3 GUP Data Repository p. 13
Each GUP Data Repository stores the primary master copy of one or several profile components. The RAF provides for the standardized access to the GUP Data Repository. The storage formats or the interface between the RAF and GUP Data Repository are not specified by GUP. It is presumed that the RAF and the GUP Data Repository are usually co-located in the same network element.
The GUP Data Repository may contain also the authorization data depending on the authorization model and architecture.
4.2.4 Reference Points p. 13
Reference Points in the GUP Reference Architecture:
- Reference point Rg This reference point shall allow applications to create, read, modify and delete any user profile data using the harmonized access interface. The GUP Server locates the data repositories responsible of the storage of the requested profile component(s) and in case of proxy mode carries out the requested operation on the data. The reference point Rg shall support interworking to other mechanisms that support parts of the user profile outside the scope of 3GPP e.g. Liberty ID-WSF SOAP Binding Specification [3] and Liberty ID-WSF Data Services Template [4]. In the redirect mode, the GUP Server returns the locations of the GUP Data Repositories and the application can then send the requested operations via reference point Rp directly to the corresponding GUP Data Repositories. The reference point Rg carries user related data, and therefore shall be protected by security mechanisms.
- Reference point Rp
4.2.5 Applications p. 13
The applications that may apply GUP reference points Rg and Rp may be targeted for different purposes e.g. for value added services or subscription management. Both operator's own applications and third party applications are covered. The latter ones shall apply Rg reference point.
Additionally the applications may utilise a discovery service to discover the contact reference information if not found out by other means. A discovery service e.g., as specified in Liberty Discovery Service Specification [2], may also act as Trusted Authority providing essential security related information (e.g. preferences in terms of peer entity and message authentication mechanism to be used and authentication and/or authorization assertions). Different policies may be followed in the use of discovery service. It may be used by different applications in different ways: per each operation, occasionally or not at all. In general terms, third party applications belonging to external security domains shall use a discovery service as a normal step, but in operator's services it may not be needed at all.
Applications have different authorization rights to the GUP data of different subscribers as agreed between the parties.
4.2.6 Message flow of using GUP p. 13
For an application requesting GUP data component(s) a message flow is described in the following:
- The application requests a GUP component(s) via Single Point of Access (Rg) from the GUP server. The application will indicate if it can support the Redirect mode.
- The GUP server authenticates the application. Note that also separate authentication services may be applied.
- The GUP Server identifies the level of authorization the Application is allowed to access the GUP data.
- The GUP Server identifies the location of the GUP component(s).
- Access the GUP component(s) by means of the Harmonized Access Interface (Rp) or by other means outside the scope of GUP.
- Respond to the application with the result of the request, optionally combining results from different GUP data repositories.
- Respond to the application with reference(s) to the component(s) and additionally authorization credentials with limited lifetime. Note that authorization credentials from other sources are not excluded.
- The application uses the reference(s) and the authorization credentials to access GUP data repositories by means of the Rp reference point.
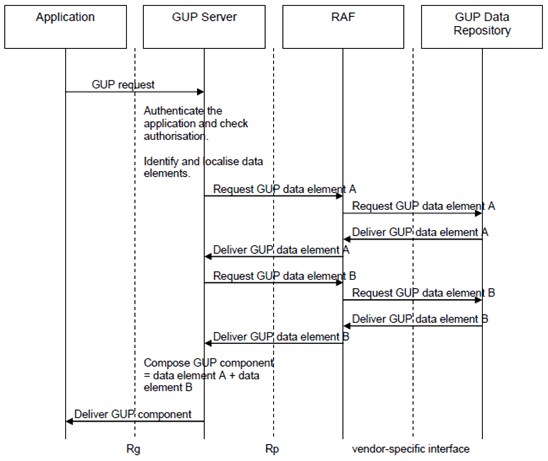
Figure 4.5: An Example of Application requesting GUP data component(s) message flow (Proxy mode)
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)
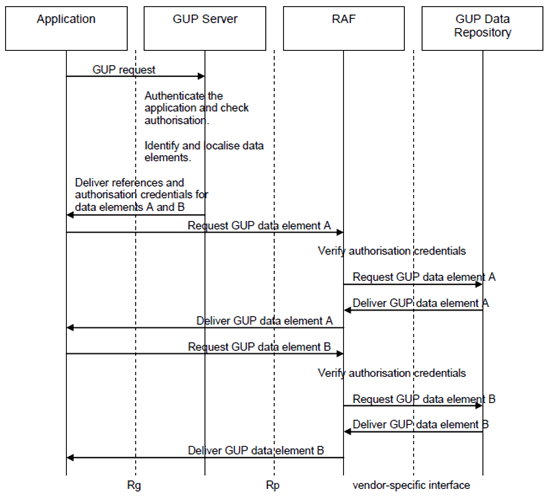
Figure 4.6: An Application requesting GUP data component(s) message flow (Redirect mode)
(⇒ copy of original 3GPP image)
(⇒ copy of original 3GPP image)